HTTPS secures data transmission over the web by encrypting HTTP messages using SSL/TLS protocols, ensuring confidentiality and integrity. SSH provides a secure channel for remote command execution and file transfers through encrypted connections, often used for secure server access and management. Both protocols use strong encryption but serve different purposes: HTTPS for web communication and SSH for secure shell access.
Table of Comparison
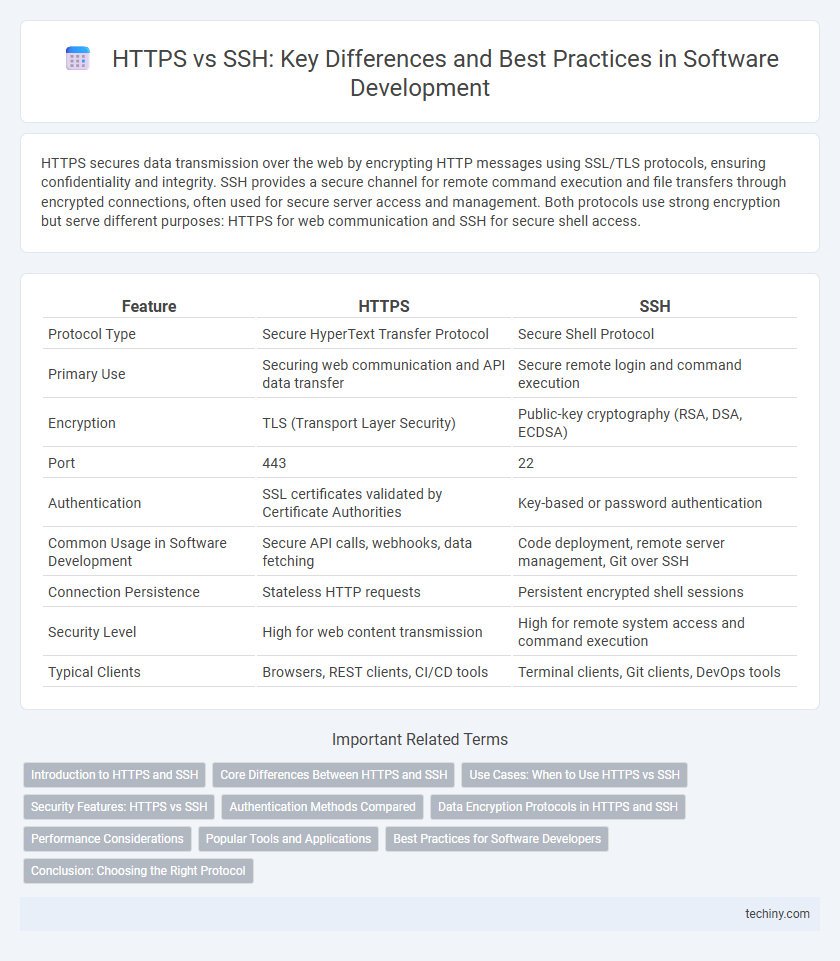
| Feature | HTTPS | SSH |
|---|---|---|
| Protocol Type | Secure HyperText Transfer Protocol | Secure Shell Protocol |
| Primary Use | Securing web communication and API data transfer | Secure remote login and command execution |
| Encryption | TLS (Transport Layer Security) | Public-key cryptography (RSA, DSA, ECDSA) |
| Port | 443 | 22 |
| Authentication | SSL certificates validated by Certificate Authorities | Key-based or password authentication |
| Common Usage in Software Development | Secure API calls, webhooks, data fetching | Code deployment, remote server management, Git over SSH |
| Connection Persistence | Stateless HTTP requests | Persistent encrypted shell sessions |
| Security Level | High for web content transmission | High for remote system access and command execution |
| Typical Clients | Browsers, REST clients, CI/CD tools | Terminal clients, Git clients, DevOps tools |
Introduction to HTTPS and SSH
HTTPS (Hypertext Transfer Protocol Secure) encrypts data exchanged between web browsers and servers, ensuring secure online communication through SSL/TLS protocols. SSH (Secure Shell) enables secure remote access and command execution on networked devices by encrypting data and authenticating users via public-key cryptography. Both HTTPS and SSH protect data confidentiality and integrity, but HTTPS primarily secures web traffic while SSH focuses on secure system administration and file transfers.
Core Differences Between HTTPS and SSH
HTTPS uses TLS/SSL protocols to secure data transfer over web browsers, ensuring encrypted communication between clients and servers. SSH provides secure remote access and command execution on servers through encrypted channels, primarily for system administration and file transfers. The core difference lies in HTTPS's role in web security and data encryption for web traffic, whereas SSH focuses on secure shell access and network service tunneling.
Use Cases: When to Use HTTPS vs SSH
HTTPS is commonly used for secure web browsing, API interactions, and situations requiring encrypted data transfer over the internet, making it ideal for accessing web applications and remote resources. SSH is preferred for secure remote system administration, executing commands on servers, and managing version control repositories like Git due to its strong authentication and encrypted communication. Selecting HTTPS or SSH depends on the specific task--use HTTPS for web-based security and secure data exchange, while SSH is optimal for secure shell access and command execution in software development environments.
Security Features: HTTPS vs SSH
HTTPS encrypts data using TLS protocols, ensuring secure communication between web browsers and servers by protecting data integrity and confidentiality. SSH provides secure remote access and file transfer through cryptographic network protocols, offering robust authentication methods including public key authentication to prevent unauthorized access. Both protocols safeguard data transmission but serve distinct purposes: HTTPS for secure web browsing and SSH for secure server management.
Authentication Methods Compared
HTTPS uses username and password or client-side certificates for authentication, ensuring secure communication through SSL/TLS encryption. SSH relies on public key authentication, where a pair of cryptographic keys grants access without transmitting passwords, enhancing security against credential theft. Both protocols provide robust authentication but SSH's key-based method offers stronger protection against unauthorized access in software development environments.
Data Encryption Protocols in HTTPS and SSH
HTTPS uses the TLS (Transport Layer Security) protocol to encrypt data between web browsers and servers, ensuring secure transmission by protecting against interception and tampering. SSH (Secure Shell) employs its own encryption protocol to establish a secure channel for remote command execution and file transfers, utilizing asymmetric cryptography for authentication and session encryption. While HTTPS primarily secures web traffic with certificate-based encryption, SSH provides encrypted access to network services and devices, emphasizing secure administration and file management.
Performance Considerations
HTTPS typically incurs higher latency due to the SSL/TLS handshake process that establishes a secure connection, impacting initial response times in software development workflows. SSH, optimized for secure remote access, often delivers faster authentication and data transfer speeds, making it preferable for tasks such as remote code execution or repository management. Choosing between HTTPS and SSH depends on the specific performance demands of development activities, with SSH generally offering better efficiency for version control operations.
Popular Tools and Applications
Popular tools using HTTPS include web browsers like Google Chrome and Firefox, which ensure secure data transmission for websites, while applications such as Postman utilize HTTPS for API testing. SSH dominates in secure shell access and file transfers, with tools like PuTTY and OpenSSH enabling encrypted command-line sessions and remote server management. Both protocols are integral in software development workflows, with HTTPS favored for web communication and SSH preferred for secure, authenticated server interactions.
Best Practices for Software Developers
Software developers should prioritize HTTPS for secure web communication, ensuring encrypted data transmission to protect sensitive user information from interception. SSH is essential for secure remote access and managing servers, enabling encrypted command-line sessions and file transfers, minimizing the risk of unauthorized access. Combining HTTPS for web-based applications and SSH for backend infrastructure aligns with industry best practices for maintaining robust security in the software development lifecycle.
Conclusion: Choosing the Right Protocol
Choosing between HTTPS and SSH depends on the specific requirements of your software development workflow, such as security, ease of use, and compatibility. HTTPS is ideal for secure, encrypted web communications and is widely supported by browsers and APIs, while SSH excels in secure remote server access and automated deployments with key-based authentication. Evaluating project needs and infrastructure helps ensure the selected protocol optimizes security and operational efficiency.
HTTPS vs SSH Infographic
 techiny.com
techiny.com