Biometric authentication in wearable technology for pets relies on unique physical traits such as fingerprints or facial recognition to verify identity, offering high security but requiring specialized hardware. Physiological authentication monitors vital signs like heart rate or body temperature, enabling continuous and non-invasive verification tailored to the pet's health patterns. Combining these methods can enhance accuracy and reliability in pet monitoring systems, improving safety and personalized care.
Table of Comparison
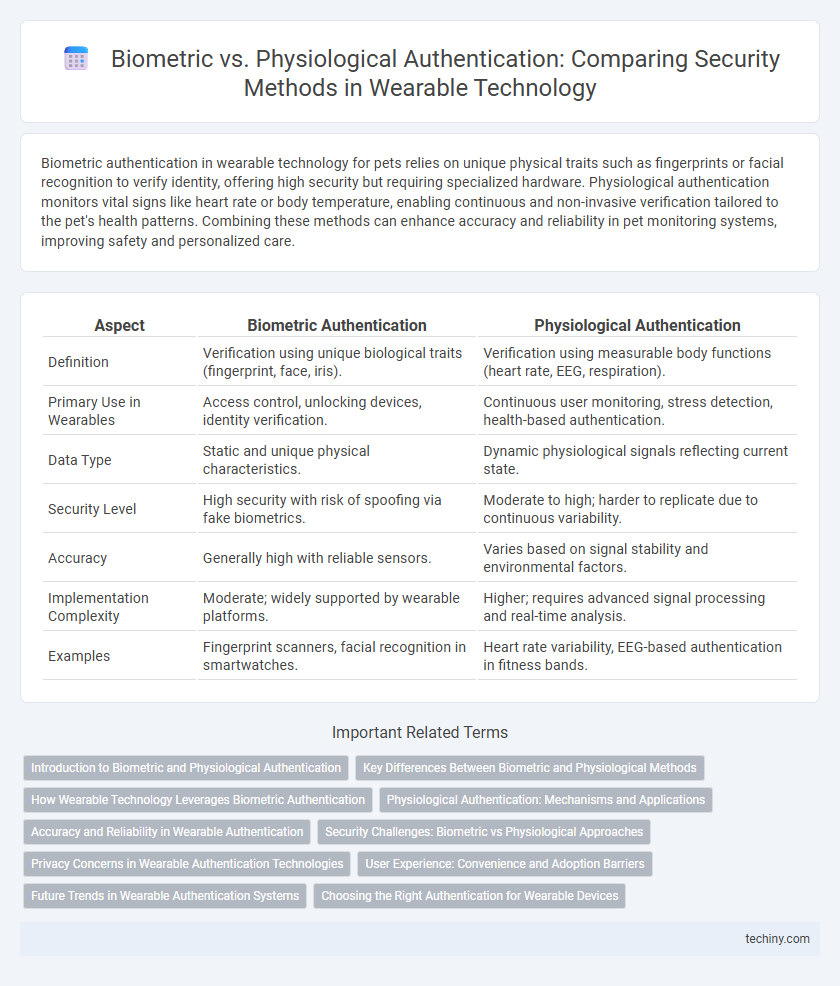
| Aspect | Biometric Authentication | Physiological Authentication |
|---|---|---|
| Definition | Verification using unique biological traits (fingerprint, face, iris). | Verification using measurable body functions (heart rate, EEG, respiration). |
| Primary Use in Wearables | Access control, unlocking devices, identity verification. | Continuous user monitoring, stress detection, health-based authentication. |
| Data Type | Static and unique physical characteristics. | Dynamic physiological signals reflecting current state. |
| Security Level | High security with risk of spoofing via fake biometrics. | Moderate to high; harder to replicate due to continuous variability. |
| Accuracy | Generally high with reliable sensors. | Varies based on signal stability and environmental factors. |
| Implementation Complexity | Moderate; widely supported by wearable platforms. | Higher; requires advanced signal processing and real-time analysis. |
| Examples | Fingerprint scanners, facial recognition in smartwatches. | Heart rate variability, EEG-based authentication in fitness bands. |
Introduction to Biometric and Physiological Authentication
Biometric authentication uses unique biological characteristics such as fingerprints, facial recognition, and iris patterns to verify identity, ensuring high security in wearable technology. Physiological authentication relies on measurable internal signals like heart rate variability, electrocardiogram (ECG), and electroencephalogram (EEG) patterns to authenticate users continuously and passively. Both methods enhance personalized security by integrating advanced sensors and machine learning algorithms within wearable devices.
Key Differences Between Biometric and Physiological Methods
Biometric authentication uses unique physical characteristics like fingerprints, iris patterns, and facial features to verify identity, while physiological authentication monitors dynamic body signals such as heart rate, electrocardiogram (ECG), and brain waves. Biometric methods provide static data that remain relatively constant over time, whereas physiological methods rely on continuous, real-time measurements that reflect the user's current state. Accuracy and security vary as biometric systems excel in identity verification, and physiological approaches offer enhanced protection through liveness detection and resistance to spoofing.
How Wearable Technology Leverages Biometric Authentication
Wearable technology leverages biometric authentication by utilizing unique physiological and behavioral traits such as fingerprint patterns, heart rate variability, and electrocardiogram (ECG) signals to securely verify user identity. Advanced sensors embedded in devices like smartwatches and fitness trackers continuously capture and analyze biometric data, enabling real-time authentication that enhances security and user convenience. This integration of biometric authentication in wearables reduces reliance on passwords and PINs, providing seamless access control while protecting sensitive personal information.
Physiological Authentication: Mechanisms and Applications
Physiological authentication in wearable technology utilizes unique biological traits such as heart rate patterns, gait analysis, and electrodermal activity to verify user identity with high accuracy. Mechanisms involve continuous monitoring through embedded sensors that capture real-time physiological data for seamless, non-intrusive security verification. Applications range from secure access control in healthcare and financial services to personalized fitness tracking and stress management, enhancing both user convenience and data privacy.
Accuracy and Reliability in Wearable Authentication
Biometric authentication in wearable technology utilizes unique physical traits such as fingerprints or iris patterns, offering high accuracy due to distinctive identifiers. Physiological authentication relies on dynamic signals like heart rate variability and electrocardiogram patterns, which provide continuous monitoring but face challenges with variability caused by physical activity or environmental factors. The reliability of biometric methods generally surpasses physiological systems, though combining both enhances overall security and user authentication precision in wearables.
Security Challenges: Biometric vs Physiological Approaches
Biometric authentication relies on unique biological traits like fingerprints or iris patterns, offering high accuracy but facing vulnerabilities such as spoofing and sensor tampering. Physiological authentication uses dynamic signals like heart rate variability or electroencephalogram (EEG) patterns, presenting challenges in consistency and susceptibility to environmental noise. Both methods require robust encryption and anti-spoofing techniques to address privacy concerns and prevent unauthorized access in wearable technology.
Privacy Concerns in Wearable Authentication Technologies
Biometric authentication in wearable technology relies on unique biological traits such as fingerprints or facial recognition, raising significant privacy concerns due to potential data breaches and unauthorized access to sensitive personal information. Physiological authentication, utilizing continuous monitoring of heart rate patterns or electroencephalogram signals, presents an alternative with inherent variability that complicates data storage and protection protocols. Both approaches demand robust encryption standards and user consent frameworks to address privacy risks and ensure secure, ethical deployment of wearable authentication systems.
User Experience: Convenience and Adoption Barriers
Biometric authentication in wearable technology offers faster access and higher accuracy by using fingerprint or facial recognition, enhancing user convenience and appeal. Physiological authentication relies on continuous monitoring of heart rate, skin conductance, or body temperature, which provides seamless security but may face adoption barriers due to sensor comfort and data privacy concerns. User experience improves when devices balance security and unobtrusiveness, minimizing authentication friction to promote widespread adoption.
Future Trends in Wearable Authentication Systems
Advancements in wearable technology are driving the integration of biometric authentication methods like fingerprint, facial recognition, and iris scanning with physiological authentication techniques such as heart rate variability and electroencephalography (EEG). Future trends indicate a shift towards multi-modal authentication systems leveraging AI and machine learning to enhance accuracy, security, and user convenience. Emerging sensors and continuous monitoring capabilities will enable real-time adaptive authentication, reducing fraud and improving the seamlessness of wearable device interactions.
Choosing the Right Authentication for Wearable Devices
Biometric authentication in wearable devices relies on unique physiological features such as fingerprints and facial recognition, offering high security but requiring advanced sensor integration. Physiological authentication utilizes dynamic traits like heart rate patterns and gait analysis, providing continuous verification without interrupting user experience. Choosing the right authentication method depends on balancing security needs, device capabilities, and user convenience in wearable technology applications.
Biometric Authentication vs Physiological Authentication Infographic
 techiny.com
techiny.com