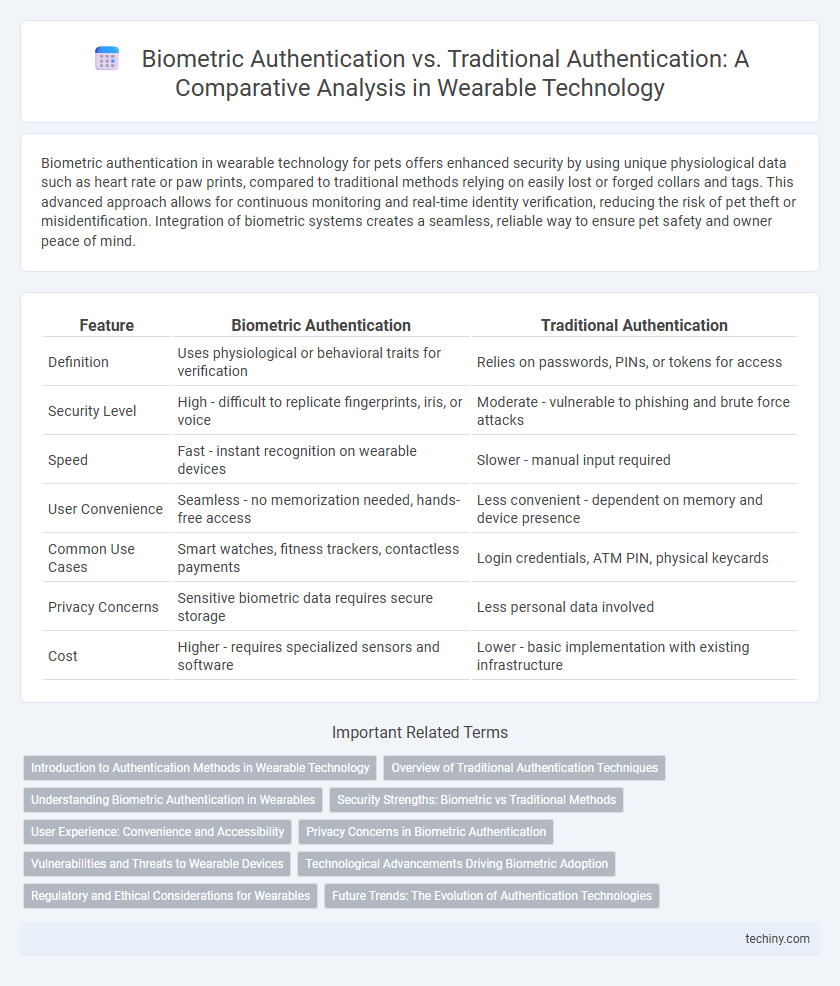
Biometric authentication in wearable technology for pets offers enhanced security by using unique physiological data such as heart rate or paw prints, compared to traditional methods relying on easily lost or forged collars and tags. This advanced approach allows for continuous monitoring and real-time identity verification, reducing the risk of pet theft or misidentification. Integration of biometric systems creates a seamless, reliable way to ensure pet safety and owner peace of mind.
Table of Comparison
| Feature | Biometric Authentication | Traditional Authentication |
|---|---|---|
| Definition | Uses physiological or behavioral traits for verification | Relies on passwords, PINs, or tokens for access |
| Security Level | High - difficult to replicate fingerprints, iris, or voice | Moderate - vulnerable to phishing and brute force attacks |
| Speed | Fast - instant recognition on wearable devices | Slower - manual input required |
| User Convenience | Seamless - no memorization needed, hands-free access | Less convenient - dependent on memory and device presence |
| Common Use Cases | Smart watches, fitness trackers, contactless payments | Login credentials, ATM PIN, physical keycards |
| Privacy Concerns | Sensitive biometric data requires secure storage | Less personal data involved |
| Cost | Higher - requires specialized sensors and software | Lower - basic implementation with existing infrastructure |
Introduction to Authentication Methods in Wearable Technology
Biometric authentication in wearable technology leverages unique physiological traits such as fingerprints, heart rate patterns, and facial recognition to verify user identity with high accuracy and convenience. Traditional authentication methods, including passwords and PINs, rely on knowledge-based security, which can be vulnerable to theft and user error. The integration of biometric sensors in wearable devices enhances security by providing continuous, seamless authentication tailored to individual users.
Overview of Traditional Authentication Techniques
Traditional authentication techniques primarily include passwords, PINs, and security questions, which rely on knowledge-based factors that can be forgotten or stolen. Physical tokens such as key cards and hardware tokens provide possession-based security but are susceptible to loss or duplication. These methods lack continuous user verification and are vulnerable to phishing attacks and unauthorized access, highlighting limitations in security compared to biometric authentication systems.
Understanding Biometric Authentication in Wearables
Biometric authentication in wearables leverages unique physiological traits such as fingerprints, heart rate patterns, or iris scans to provide secure and seamless access, surpassing traditional methods like passwords or PINs that are prone to theft and forgetfulness. Advanced sensors integrated into devices like smartwatches and fitness trackers collect real-time biometric data, enabling continuous and non-intrusive user verification. This method enhances security by reducing the risk of unauthorized access and improving user convenience through instant, contactless authentication.
Security Strengths: Biometric vs Traditional Methods
Biometric authentication leverages unique physiological traits such as fingerprints, iris patterns, and facial recognition, offering a higher security level compared to traditional methods like passwords and PINs that are vulnerable to hacking and theft. Wearable technology equipped with biometric sensors provides continuous and passive authentication, reducing the risk of unauthorized access by ensuring the user's identity is verified in real-time. The integration of multi-factor biometric verification in wearables enhances security strength by combining behavioral and physiological data, making it significantly harder for attackers to bypass compared to single-factor traditional authentication.
User Experience: Convenience and Accessibility
Biometric authentication in wearable technology enhances user experience by offering seamless and quick access without the need for passwords or PIN codes, significantly improving convenience. Traditional authentication methods often require manual input, which can be cumbersome and less accessible, especially during physical activities or on-the-go scenarios. Wearables leveraging fingerprint, facial, or heart rate recognition provide a more intuitive and accessible interface, reducing friction and enabling real-time authentication.
Privacy Concerns in Biometric Authentication
Biometric authentication in wearable technology raises significant privacy concerns due to the storage and potential misuse of sensitive personal data such as fingerprints, facial recognition, and heart rate patterns. Unlike traditional authentication methods like passwords or PINs, biometric data is immutable and uniquely linked to an individual, making breaches more impactful and harder to mitigate. Ensuring secure encryption and strict data access controls is critical to protect users' biometric information from unauthorized access and identity theft.
Vulnerabilities and Threats to Wearable Devices
Biometric authentication in wearable technology offers enhanced security by using unique physiological traits, yet it remains vulnerable to threats like spoofing, sensor hacking, and data interception during transmission. Traditional authentication methods, such as passwords or PINs, face risks including brute force attacks, shoulder surfing, and data breaches, making them less secure in dynamic wearable environments. Both authentication types require robust encryption and multi-factor strategies to mitigate vulnerabilities and protect sensitive biometric and personal data on wearable devices.
Technological Advancements Driving Biometric Adoption
Biometric authentication harnesses advanced sensor technologies such as fingerprint scanners, facial recognition, and iris scanners, offering superior security compared to traditional passwords and PINs vulnerable to theft or hacking. Innovations in artificial intelligence and machine learning enable real-time analysis and adaptive learning, significantly enhancing the accuracy and speed of biometric systems in wearable devices. The integration of secure enclaves and encryption algorithms within wearables ensures biometric data privacy, driving widespread adoption in cybersecurity-sensitive sectors like finance, healthcare, and government.
Regulatory and Ethical Considerations for Wearables
Biometric authentication in wearable technology presents unique regulatory challenges due to the sensitive nature of personal physiological data, requiring compliance with data protection laws such as GDPR and HIPAA. Ethical considerations emphasize user consent, data privacy, and the potential risks of biometric data breaches, highlighting the need for transparent policies and robust encryption standards. Traditional authentication methods lack the granularity of biometric data but face fewer regulatory constraints, making biometric solutions both a powerful and complex choice for wearable security.
Future Trends: The Evolution of Authentication Technologies
Biometric authentication methods, leveraging fingerprint, facial recognition, and iris scans, are rapidly advancing with AI integration to enhance accuracy and security in wearable technology. Future trends indicate a shift from traditional passwords and PINs towards continuous authentication systems that monitor physiological signals in real-time, reducing vulnerability to breaches. The evolution emphasizes seamless user experience combined with heightened privacy protections through decentralized data storage and blockchain-based identity verification.
Biometric Authentication vs Traditional Authentication Infographic
 techiny.com
techiny.com