Sessions store user state on the server, providing secure and centralized control over authentication, while tokens enable stateless and scalable client-side management, often used in RESTful APIs. Tokens, such as JWTs, contain encoded user information and expire after a set time, reducing server memory usage compared to session storage. Choosing between sessions and tokens depends on the application's scalability needs, security requirements, and client-server architecture.
Table of Comparison
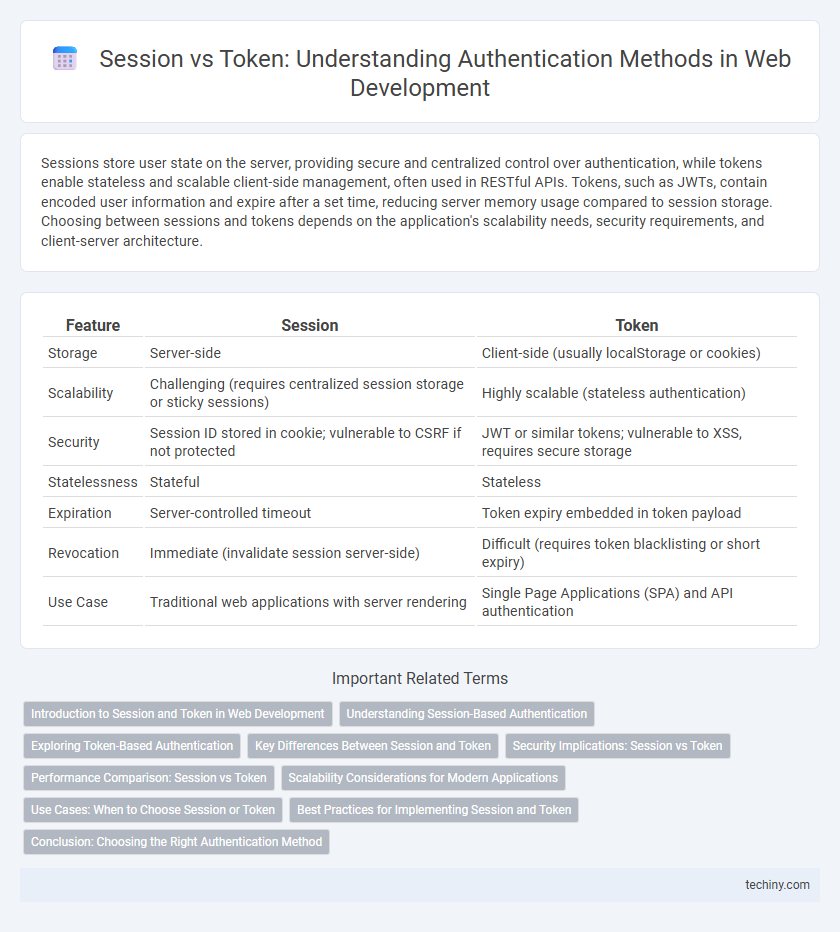
| Feature | Session | Token |
|---|---|---|
| Storage | Server-side | Client-side (usually localStorage or cookies) |
| Scalability | Challenging (requires centralized session storage or sticky sessions) | Highly scalable (stateless authentication) |
| Security | Session ID stored in cookie; vulnerable to CSRF if not protected | JWT or similar tokens; vulnerable to XSS, requires secure storage |
| Statelessness | Stateful | Stateless |
| Expiration | Server-controlled timeout | Token expiry embedded in token payload |
| Revocation | Immediate (invalidate session server-side) | Difficult (requires token blacklisting or short expiry) |
| Use Case | Traditional web applications with server rendering | Single Page Applications (SPA) and API authentication |
Introduction to Session and Token in Web Development
Sessions in web development store user data on the server to maintain stateful interactions across multiple requests, enhancing security by keeping sensitive information off the client side. Tokens, such as JSON Web Tokens (JWT), encode user credentials and are stored client-side, enabling stateless, scalable authentication by transmitting the token with each request. Understanding the distinct mechanisms and security implications of sessions and tokens is crucial for designing effective authentication systems.
Understanding Session-Based Authentication
Session-based authentication stores user data and login status on the server, linking each session to a unique session ID saved in a cookie on the client side. It relies on server memory or a distributed cache like Redis to manage session state, ensuring secure control over user access and easier invalidation of sessions. This method simplifies session management but may face scalability challenges compared to stateless token-based authentication.
Exploring Token-Based Authentication
Token-based authentication enhances security by enabling stateless, scalable user verification through digitally signed tokens such as JWTs, which encapsulate user identity and permissions. Unlike traditional session-based methods that store authentication data on the server, tokens reside on the client side and are included in each request header, reducing server memory usage and improving performance. This approach facilitates cross-origin resource sharing (CORS) and mobile-friendly API access, making it ideal for modern web applications requiring distributed and decoupled architectures.
Key Differences Between Session and Token
Sessions store user data on the server side and rely on a unique session ID sent via cookies to maintain state, offering centralized control and easier revocation. Tokens, such as JSON Web Tokens (JWT), contain user information encoded and signed, enabling stateless authentication by being stored client-side and included in each request. Sessions require server memory and are vulnerable to CSRF attacks, while tokens allow scalability across distributed systems but risk exposure if improperly stored.
Security Implications: Session vs Token
Session-based authentication stores user data on the server, reducing the risk of token interception but increasing vulnerability to session hijacking if cookies are stolen. Token-based authentication, particularly using JWTs, provides stateless scalability and can include encrypted claims, yet poses risks such as token replay attacks and requires secure token storage on the client side. Implementing secure cookie flags like HttpOnly and SameSite for sessions and short token expiration times with refresh mechanisms for tokens enhances overall web application security.
Performance Comparison: Session vs Token
Session-based authentication stores user data on the server, leading to increased memory usage and potential bottlenecks as concurrent users grow, impacting overall performance. Token-based authentication, such as JWT, offloads storage to the client side, reducing server load and enabling faster scalability and response times. This stateless approach improves performance in distributed architectures by eliminating server-side session lookups.
Scalability Considerations for Modern Applications
Session-based authentication stores user data on the server, which can limit scalability due to increased memory usage and state management across distributed systems. Token-based authentication, often using JWTs, enables stateless, scalable architectures by embedding user session data within the token itself, minimizing server-side storage. Modern applications prefer tokens for microservices and cloud environments to streamline horizontal scaling and reduce infrastructure overhead.
Use Cases: When to Choose Session or Token
Sessions are ideal for traditional web applications requiring server-side state management and secure, short-lived user authentication, especially when sensitive information must be protected within the server. Tokens, particularly JSON Web Tokens (JWT), are better suited for stateless, distributed systems like RESTful APIs and mobile applications where scalability and cross-origin resource sharing (CORS) are critical. Choosing sessions works best for applications with tightly controlled domains, while tokens excel in scenarios demanding decentralized authentication and seamless integration across multiple services.
Best Practices for Implementing Session and Token
Implement best practices for session management by using secure, HTTP-only cookies with proper expiration and regeneration policies to prevent session fixation and hijacking. For token-based authentication, utilize JSON Web Tokens (JWT) with short-lived access tokens, refresh tokens stored securely, and implement token revocation mechanisms to enhance security. Always enforce HTTPS, validate tokens thoroughly, and regularly audit authentication flows to maintain robust web application security.
Conclusion: Choosing the Right Authentication Method
Session-based authentication offers robust security through server-side session storage, ideal for traditional web applications requiring persistent user state management. Token-based authentication, especially using JWTs, provides scalability and statelessness, making it suitable for single-page applications and APIs with distributed architectures. Selecting the right method depends on application architecture, security requirements, and scalability needs, with token-based solutions favored for mobile and RESTful services, while sessions excel in server-rendered environments.
Session vs Token Infographic
 techiny.com
techiny.com