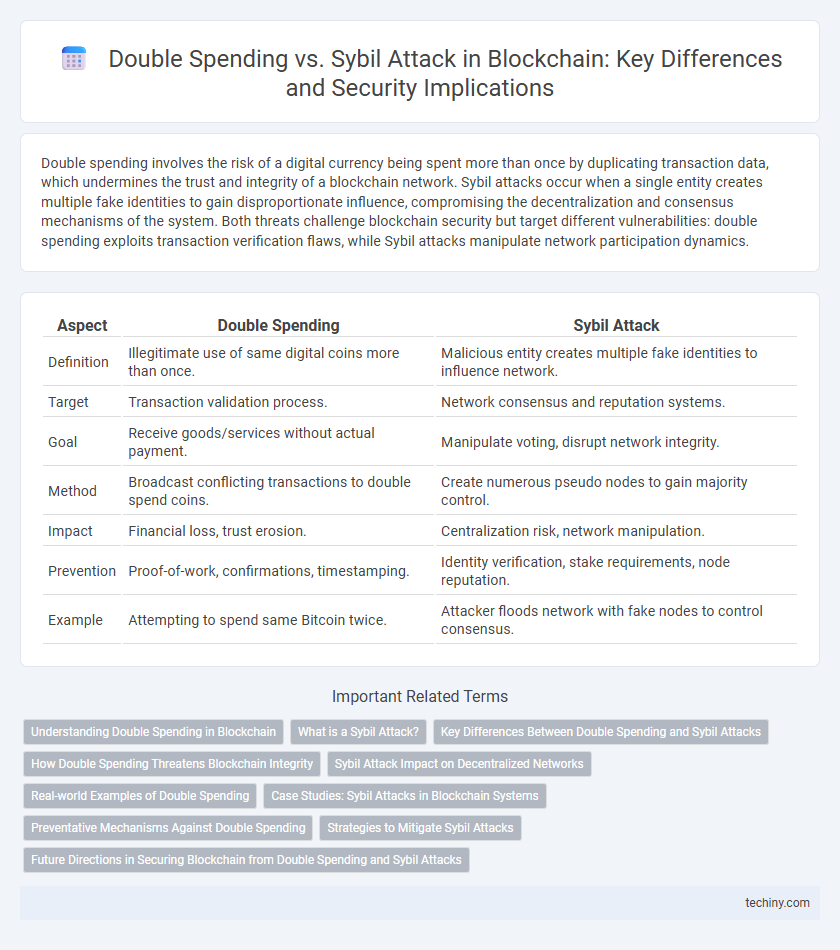
Double spending involves the risk of a digital currency being spent more than once by duplicating transaction data, which undermines the trust and integrity of a blockchain network. Sybil attacks occur when a single entity creates multiple fake identities to gain disproportionate influence, compromising the decentralization and consensus mechanisms of the system. Both threats challenge blockchain security but target different vulnerabilities: double spending exploits transaction verification flaws, while Sybil attacks manipulate network participation dynamics.
Table of Comparison
| Aspect | Double Spending | Sybil Attack |
|---|---|---|
| Definition | Illegitimate use of same digital coins more than once. | Malicious entity creates multiple fake identities to influence network. |
| Target | Transaction validation process. | Network consensus and reputation systems. |
| Goal | Receive goods/services without actual payment. | Manipulate voting, disrupt network integrity. |
| Method | Broadcast conflicting transactions to double spend coins. | Create numerous pseudo nodes to gain majority control. |
| Impact | Financial loss, trust erosion. | Centralization risk, network manipulation. |
| Prevention | Proof-of-work, confirmations, timestamping. | Identity verification, stake requirements, node reputation. |
| Example | Attempting to spend same Bitcoin twice. | Attacker floods network with fake nodes to control consensus. |
Understanding Double Spending in Blockchain
Double spending in blockchain occurs when a malicious actor attempts to spend the same cryptocurrency tokens in multiple transactions, undermining transaction validity. This issue exploits the decentralized nature of blockchain networks, requiring consensus protocols like Proof of Work or Proof of Stake to prevent fraudulent spending. Effective mitigation relies on network confirmations and cryptographic validation to ensure the immutability and security of digital assets.
What is a Sybil Attack?
A Sybil attack in blockchain occurs when a single entity creates multiple fake identities to gain disproportionate influence over the network, compromising its security and decentralization. Unlike double spending, which targets the transaction validation process by spending the same coins twice, a Sybil attack manipulates network consensus by overwhelming honest nodes with counterfeit participants. Effective mitigation requires robust identity verification mechanisms and consensus algorithms designed to resist such identity-based threats.
Key Differences Between Double Spending and Sybil Attacks
Double spending involves the malicious reuse of the same cryptocurrency tokens in multiple transactions, compromising transaction integrity and trust in blockchain networks. Sybil attacks exploit the creation of numerous fake identities or nodes to manipulate consensus mechanisms and overwhelm legitimate participants. The key difference lies in double spending targeting the currency's value, while Sybil attacks aim to control network governance and voting power.
How Double Spending Threatens Blockchain Integrity
Double spending threatens blockchain integrity by allowing malicious actors to spend the same cryptocurrency twice, undermining the trust and security of the ledger. This attack exploits the decentralized consensus mechanism by reversing or invalidating confirmed transactions, causing financial losses and reducing confidence in the network. Unlike Sybil attacks that involve creating multiple fake identities to gain influence, double spending directly targets transactional validity and the immutability of the blockchain.
Sybil Attack Impact on Decentralized Networks
Sybil attacks pose a significant threat to decentralized blockchain networks by enabling a single adversary to create multiple fake identities, undermining network consensus and trust. This attack can disrupt transaction validation processes, leading to potential manipulation or control over the network's governance and decision-making. Unlike double spending, which directly targets transaction integrity, Sybil attacks compromise the network's security model by exploiting its reliance on identity diversity.
Real-world Examples of Double Spending
Double spending occurs when a cryptocurrency user fraudulently spends the same digital token more than once, exploiting vulnerabilities in transaction verification. Notable real-world examples include the 2014 incident on the Bitcoin Gold network, where attackers executed double spending attacks resulting in over $18 million in losses. This contrasts with Sybil attacks, which involve creating multiple fake identities to gain disproportionate influence, emphasizing the importance of robust consensus mechanisms to prevent such exploits.
Case Studies: Sybil Attacks in Blockchain Systems
Sybil attacks in blockchain systems exploit counterfeit identities to disrupt network consensus, undermining trust and security. Case studies highlight vulnerabilities in peer-to-peer networks where attackers create numerous pseudonymous nodes, enabling control over transaction validation and mining processes. These attacks contrast with double spending, which directly targets transaction integrity by spending the same cryptocurrency multiple times.
Preventative Mechanisms Against Double Spending
Double spending prevention in blockchain relies on consensus algorithms like Proof of Work (PoW) and Proof of Stake (PoS) to validate transactions and ensure that digital currency is not spent multiple times. Network nodes verify and confirm transactions through cryptographic proofs and decentralized ledgers, making fraudulent duplications computationally and economically infeasible. Checkpointing mechanisms and transaction confirmations further enhance security by creating irreversible transaction histories that protect against double spending exploits distinct from Sybil attack vulnerabilities.
Strategies to Mitigate Sybil Attacks
Sybil attacks in blockchain exploit fake identities to gain disproportionate influence over the network, undermining consensus mechanisms. Strategies to mitigate Sybil attacks include implementing proof-of-work or proof-of-stake protocols that require resource expenditure, combined with identity verification methods and reputation-based systems to ensure node authenticity. Network-level solutions such as limiting node connections and utilizing social trust graphs enhance resistance to Sybil penetration while maintaining decentralized trust.
Future Directions in Securing Blockchain from Double Spending and Sybil Attacks
Future directions in securing blockchain from double spending and Sybil attacks emphasize the integration of advanced consensus mechanisms such as Proof of Stake (PoS) combined with reputation-based systems to enhance node validation. Leveraging machine learning algorithms for real-time anomaly detection can proactively mitigate fraudulent transactions and identity manipulations. Developing decentralized identity frameworks and cross-chain verification protocols further strengthens security by ensuring authentic participation and transactional integrity across diverse blockchain networks.
Double spending vs Sybil attack Infographic
 techiny.com
techiny.com