Permissioned ledgers restrict access to known participants, enhancing privacy and control while ensuring faster transaction validation through trusted nodes. Permissionless ledgers allow open participation, promoting decentralization and censorship resistance but often face scalability challenges due to consensus mechanisms like proof-of-work. Choosing between these ledgers depends on priorities such as transparency, security, and transaction speed in blockchain applications.
Table of Comparison
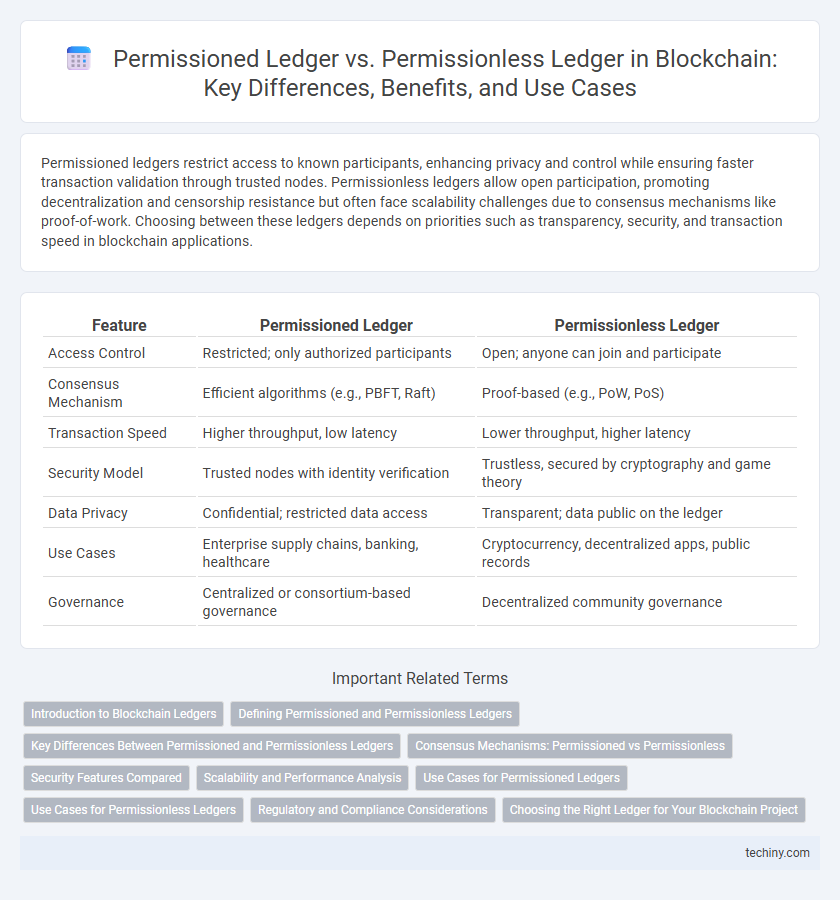
| Feature | Permissioned Ledger | Permissionless Ledger |
|---|---|---|
| Access Control | Restricted; only authorized participants | Open; anyone can join and participate |
| Consensus Mechanism | Efficient algorithms (e.g., PBFT, Raft) | Proof-based (e.g., PoW, PoS) |
| Transaction Speed | Higher throughput, low latency | Lower throughput, higher latency |
| Security Model | Trusted nodes with identity verification | Trustless, secured by cryptography and game theory |
| Data Privacy | Confidential; restricted data access | Transparent; data public on the ledger |
| Use Cases | Enterprise supply chains, banking, healthcare | Cryptocurrency, decentralized apps, public records |
| Governance | Centralized or consortium-based governance | Decentralized community governance |
Introduction to Blockchain Ledgers
Permissioned ledgers restrict access to authorized participants, ensuring enhanced security and control suited for enterprise applications, while permissionless ledgers allow open participation, promoting decentralization and transparency on public blockchains. Permissioned blockchain platforms like Hyperledger Fabric offer customizable access controls, enabling efficient transaction validation among trusted nodes. In contrast, permissionless systems such as Bitcoin and Ethereum rely on consensus algorithms like Proof of Work or Proof of Stake to maintain trust and immutability across distributed, anonymous participants.
Defining Permissioned and Permissionless Ledgers
Permissioned ledgers restrict access to selected participants, allowing only authorized entities to validate transactions and maintain the blockchain, enhancing privacy and control. Permissionless ledgers enable anyone to join, participate in consensus, and contribute to transaction validation, fostering decentralization and transparency. These distinctions influence security models, governance frameworks, and use cases across industries such as finance, supply chain, and healthcare.
Key Differences Between Permissioned and Permissionless Ledgers
Permissioned ledgers restrict access to authorized participants, enhancing privacy and control, whereas permissionless ledgers allow anyone to join and validate transactions, promoting decentralization and transparency. Consensus mechanisms in permissioned ledgers often rely on practical Byzantine Fault Tolerance (PBFT) or other voting algorithms, while permissionless ledgers typically use Proof of Work (PoW) or Proof of Stake (PoS) to secure the network. Data immutability and auditability are core features of both, but permissioned ledgers offer faster transaction speeds and scalability due to controlled access.
Consensus Mechanisms: Permissioned vs Permissionless
Permissioned ledgers utilize consensus mechanisms like Practical Byzantine Fault Tolerance (PBFT) and Raft that rely on a fixed set of known validators, enabling faster transaction finality and lower energy consumption. Permissionless ledgers depend on consensus protocols such as Proof of Work (PoW) and Proof of Stake (PoS), which allow anonymous participants to validate transactions but require significant computational power or stake, resulting in higher decentralization and security trade-offs. The selection between these consensus mechanisms impacts scalability, trust model, and network governance in blockchain implementations.
Security Features Compared
Permissioned ledgers enhance security by restricting network access to verified participants, ensuring controlled data visibility and streamlined consensus mechanisms such as Practical Byzantine Fault Tolerance (PBFT). Permissionless ledgers rely on cryptographic proofs and decentralized consensus algorithms like Proof of Work (PoW) or Proof of Stake (PoS) to secure transactions, enabling open participation but increasing exposure to potential Sybil attacks. The choice between permissioned and permissionless ledgers impacts security trade-offs including trust assumptions, transaction throughput, and vulnerability to network-based threats.
Scalability and Performance Analysis
Permissioned ledgers offer enhanced scalability and performance due to controlled access, enabling faster consensus mechanisms like Practical Byzantine Fault Tolerance (PBFT), which reduces transaction latency compared to permissionless ledgers. Permissionless ledgers, such as Bitcoin and Ethereum, rely on decentralized consensus protocols like Proof of Work (PoW), resulting in higher computational costs and limited throughput. Enterprise blockchain applications typically favor permissioned ledgers for their ability to handle large volumes of transactions efficiently while maintaining security and compliance.
Use Cases for Permissioned Ledgers
Permissioned ledgers offer enhanced security and control, making them ideal for enterprise use cases such as supply chain management, financial services, and healthcare data sharing where access privacy and regulatory compliance are crucial. Organizations leverage permissioned blockchains like Hyperledger Fabric and R3 Corda to enable trusted transactions among known participants while maintaining data confidentiality. These ledgers streamline complex multi-party processes by providing transparency and auditability without exposing sensitive information to the public.
Use Cases for Permissionless Ledgers
Permissionless ledgers enable decentralized applications such as cryptocurrencies, where open access and trustless transactions are essential. These ledgers facilitate public voting systems, decentralized finance (DeFi) platforms, and supply chain transparency, leveraging broad participant consensus without centralized control. Their open nature supports innovation in peer-to-peer exchanges and digital asset management, making them ideal for ecosystems requiring censorship resistance and public verifiability.
Regulatory and Compliance Considerations
Permissioned ledgers offer enhanced regulatory compliance by restricting access to verified participants, facilitating adherence to Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations. Permissionless ledgers, while promoting transparency and decentralization, face challenges in regulatory oversight due to anonymous participation and the difficulty of enforcing legal standards. Regulatory frameworks often favor permissioned blockchains for enterprise applications requiring strict compliance and auditability.
Choosing the Right Ledger for Your Blockchain Project
Permissioned ledgers offer controlled access where only authorized participants validate transactions, enhancing security and compliance for enterprise blockchain projects. In contrast, permissionless ledgers provide open participation and decentralization, ideal for public applications requiring transparency and censorship resistance. Selecting the right ledger depends on project requirements such as trust model, access control, scalability, and regulatory considerations.
Permissioned Ledger vs Permissionless Ledger Infographic
 techiny.com
techiny.com