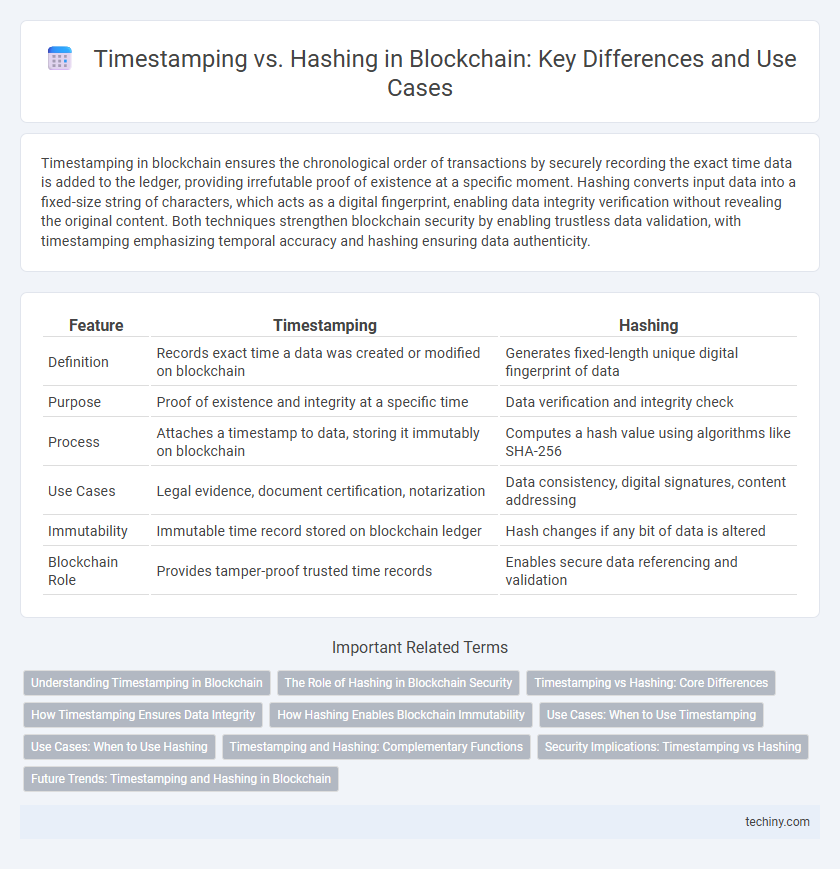
Timestamping in blockchain ensures the chronological order of transactions by securely recording the exact time data is added to the ledger, providing irrefutable proof of existence at a specific moment. Hashing converts input data into a fixed-size string of characters, which acts as a digital fingerprint, enabling data integrity verification without revealing the original content. Both techniques strengthen blockchain security by enabling trustless data validation, with timestamping emphasizing temporal accuracy and hashing ensuring data authenticity.
Table of Comparison
| Feature | Timestamping | Hashing |
|---|---|---|
| Definition | Records exact time a data was created or modified on blockchain | Generates fixed-length unique digital fingerprint of data |
| Purpose | Proof of existence and integrity at a specific time | Data verification and integrity check |
| Process | Attaches a timestamp to data, storing it immutably on blockchain | Computes a hash value using algorithms like SHA-256 |
| Use Cases | Legal evidence, document certification, notarization | Data consistency, digital signatures, content addressing |
| Immutability | Immutable time record stored on blockchain ledger | Hash changes if any bit of data is altered |
| Blockchain Role | Provides tamper-proof trusted time records | Enables secure data referencing and validation |
Understanding Timestamping in Blockchain
Timestamping in blockchain involves recording the exact time a transaction or data entry occurs, ensuring immutability and chronological order within the distributed ledger. By embedding timestamps into blocks, blockchain networks enable verifiable proof of existence and integrity for digital assets without relying on centralized authorities. This process enhances security and traceability by linking each block to a specific moment in time, providing a tamper-proof audit trail.
The Role of Hashing in Blockchain Security
Hashing in blockchain security provides a unique digital fingerprint for each block, ensuring data integrity and immutability by detecting any alterations. It enables the linking of blocks through cryptographic hashes, creating a secure and tamper-evident chain that protects against fraud and unauthorized changes. By transforming input data into fixed-size hash values, hashing underpins consensus mechanisms and maintains trust across decentralized networks.
Timestamping vs Hashing: Core Differences
Timestamping records the exact time a piece of data is created or modified, providing proof of existence at a specific moment. Hashing transforms input data into a fixed-size string of characters, serving as a unique digital fingerprint without revealing the original content. While timestamping establishes data chronology, hashing ensures data integrity and authenticity within blockchain systems.
How Timestamping Ensures Data Integrity
Timestamping in blockchain records the exact time a transaction or data entry is created, embedding this information into the blockchain's immutable ledger. This process verifies that the data existed at a specific moment, preventing backdating or tampering. By linking timestamps with cryptographic hashes, timestamping ensures data integrity through chronological proof and secure validation.
How Hashing Enables Blockchain Immutability
Hashing generates a unique digital fingerprint for each data block, ensuring any alteration changes the hash value, which immediately signals tampering. This cryptographic process secures blockchain immutability by linking each block's hash to the next, creating an unbreakable chain of verified data. Timestamping records the exact time a transaction occurs, but hashing guarantees the integrity and permanence of the blockchain ledger.
Use Cases: When to Use Timestamping
Timestamping is essential for proving the existence of digital data at a specific point in time, making it ideal for applications like intellectual property protection, legal documents verification, and compliance auditing. It creates an immutable record that can validate the chronology of transactions or data creation without revealing the data itself. Use cases include securing digital contracts, certifying academic credentials, and verifying supply chain events where temporal proof is critical.
Use Cases: When to Use Hashing
Hashing is best used for data integrity verification, ensuring that any alterations to information are easily detected by generating unique fixed-size hash values. It is crucial in password storage, file verification, and digital signatures where quick, irreversible data representation is needed. Hashing supports efficient data indexing and lookup in blockchain systems, optimizing transaction validation and block creation.
Timestamping and Hashing: Complementary Functions
Timestamping in blockchain creates immutable proof of data existence at a specific time, while hashing generates unique data fingerprints for integrity verification. Together, timestamping and hashing ensure secure, verifiable records by linking tamper-proof hashes with precise temporal information. These complementary functions enhance trust and transparency in blockchain applications such as digital identity and smart contracts.
Security Implications: Timestamping vs Hashing
Timestamping in blockchain ensures data integrity by recording the exact time a transaction or data entry was created, creating an immutable chronological record that prevents backdating or tampering. Hashing transforms data into a unique fixed-length string, securing information by enabling verification without exposing the original data, thereby safeguarding against alteration and fraud. While timestamping anchors data to a specific moment enhancing transparency, hashing provides cryptographic security crucial for verifying data authenticity and confidentiality in decentralized systems.
Future Trends: Timestamping and Hashing in Blockchain
Future trends in blockchain emphasize enhanced timestamping methods that integrate decentralized verifiable timestamps to increase transaction transparency and authenticity. Advanced hashing algorithms are evolving to improve data security and integrity while reducing computational costs, enabling scalable blockchain solutions. The convergence of AI with timestamping and hashing is expected to automate and optimize verification processes, driving more efficient and trustless blockchain networks.
Timestamping vs Hashing Infographic
 techiny.com
techiny.com