Dusting attacks target cryptocurrency wallets by sending tiny amounts of coins to trace and deanonymize users through transaction analysis. Replay attacks exploit the reuse of transaction data across different blockchain networks to fraudulently duplicate transactions. Both attacks pose significant threats by compromising user privacy and asset security within decentralized systems.
Table of Comparison
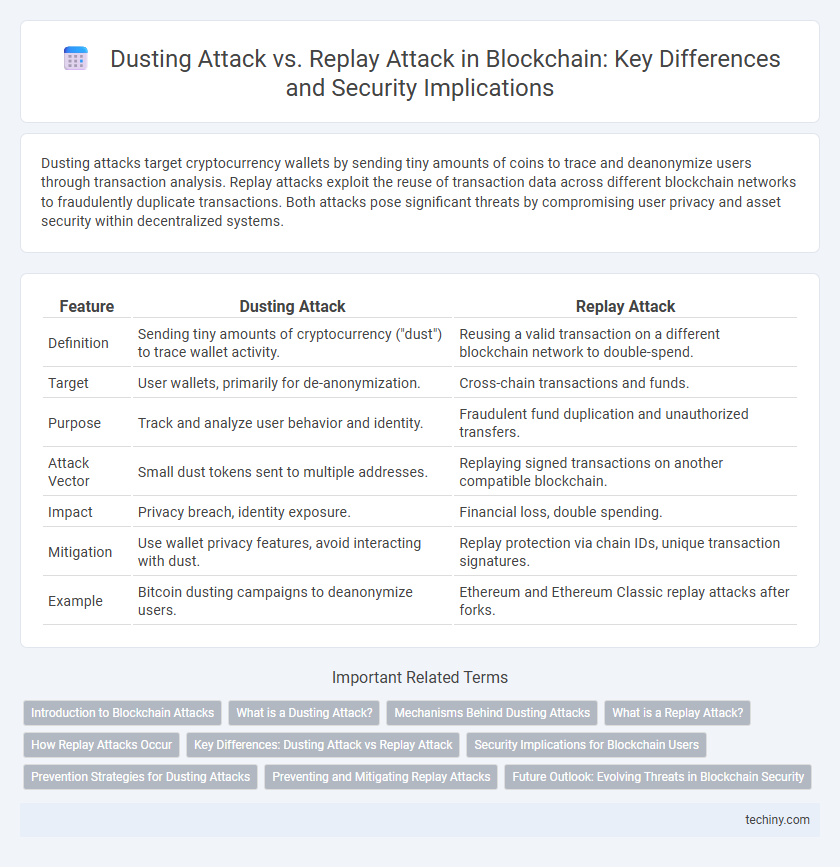
| Feature | Dusting Attack | Replay Attack |
|---|---|---|
| Definition | Sending tiny amounts of cryptocurrency ("dust") to trace wallet activity. | Reusing a valid transaction on a different blockchain network to double-spend. |
| Target | User wallets, primarily for de-anonymization. | Cross-chain transactions and funds. |
| Purpose | Track and analyze user behavior and identity. | Fraudulent fund duplication and unauthorized transfers. |
| Attack Vector | Small dust tokens sent to multiple addresses. | Replaying signed transactions on another compatible blockchain. |
| Impact | Privacy breach, identity exposure. | Financial loss, double spending. |
| Mitigation | Use wallet privacy features, avoid interacting with dust. | Replay protection via chain IDs, unique transaction signatures. |
| Example | Bitcoin dusting campaigns to deanonymize users. | Ethereum and Ethereum Classic replay attacks after forks. |
Introduction to Blockchain Attacks
Dusting attacks in blockchain involve sending tiny amounts of cryptocurrency to users' wallets to trace and deanonymize them, compromising privacy and security. Replay attacks exploit the similarity between transactions on different blockchain networks, allowing malicious actors to duplicate valid transactions and cause unintended transfers. Understanding these attack vectors is crucial for enhancing blockchain security protocols and safeguarding user assets.
What is a Dusting Attack?
A Dusting attack in blockchain targets cryptocurrency wallets by sending tiny amounts of crypto, called dust, to trace transactions and link addresses, compromising user privacy. Attackers analyze these minimal inputs to de-anonymize users and potentially identify their real-world identities. Unlike replay attacks, which duplicate transactions across different chains, dusting attacks focus on surveillance and data harvesting within the same blockchain network.
Mechanisms Behind Dusting Attacks
Dusting attacks manipulate tiny amounts of cryptocurrency called "dust" to trace and deanonymize wallet addresses by analyzing transaction patterns across the blockchain. By sending these negligible funds to multiple addresses, attackers leverage clustering algorithms to link wallets and reveal user identities. This method contrasts with replay attacks, which exploit transaction duplication on forked blockchains rather than privacy through data correlation.
What is a Replay Attack?
A Replay Attack involves an attacker intercepting and retransmitting valid blockchain transactions to fraudulently duplicate actions or gain unauthorized access. This exploit targets transaction immutability by resending transaction data on the same or different blockchain networks. Unlike Dusting attacks, which spread tiny amounts of cryptocurrency to trace wallet identities, Replay Attacks manipulate transaction broadcasts, risking double-spending and integrity breaches in decentralized systems.
How Replay Attacks Occur
Replay attacks occur when an attacker intercepts a valid blockchain transaction and fraudulently repeats or delays it to manipulate the network, exploiting the absence of unique transaction identifiers or insufficient replay protection across chains. These attacks commonly happen during cryptocurrency forks or cross-chain transfers where transaction signatures remain valid, enabling attackers to reuse them on multiple chains to double-spend or drain wallets. Implementing nonces and chain-specific transaction data are crucial methods to prevent replay attacks by ensuring each transaction is unique and valid only on its intended blockchain.
Key Differences: Dusting Attack vs Replay Attack
Dusting attacks involve sending tiny amounts of cryptocurrency to wallets to track and de-anonymize users by analyzing their transaction patterns. Replay attacks exploit transaction data on one blockchain to fraudulently repeat it on another, typically occurring after hard forks without replay protection. The key distinction lies in dusting aiming for privacy breaches, while replay attacks target transaction authenticity across blockchains.
Security Implications for Blockchain Users
Dusting attacks obscure user identities by distributing tiny amounts of cryptocurrency to multiple wallets, enabling attackers to analyze transaction patterns and compromise privacy. Replay attacks exploit blockchain forks by reusing legitimate transaction data on different chains, leading to unauthorized fund transfers and potential double-spending. Both attacks threaten blockchain users' security by undermining transaction confidentiality and integrity, emphasizing the need for robust wallet protocols and network safeguards.
Prevention Strategies for Dusting Attacks
Effective prevention strategies for dusting attacks in blockchain involve enhancing wallet privacy through the use of address rotation and coin mixing techniques. Implementing strong transaction monitoring tools helps detect and block suspicious, small-value inputs characteristic of dusting attempts. Educating users to avoid interacting with unrecognized micro-transactions further reduces the risk of privacy compromise from dusting attacks.
Preventing and Mitigating Replay Attacks
Replay attacks exploit the reuse of valid data transmissions within blockchain networks, enabling unauthorized transactions on duplicate chains or forks. Preventing replay attacks involves implementing replay protection mechanisms such as unique transaction identifiers, chain-specific signatures, and transaction versioning. Mitigating risks also requires network-level solutions like consensus protocol enhancements and user education on verifying transaction authenticity before signing to protect assets.
Future Outlook: Evolving Threats in Blockchain Security
Dusting attacks, which stealthily track user wallets through minimal token transfers, are expected to grow more sophisticated with advancements in blockchain analytics and AI-driven tracking tools. Replay attacks pose increasing risks as cross-chain interoperability and multi-chain ecosystems expand, making transaction validation challenges more complex. Future blockchain security will require adaptive cryptographic techniques and enhanced multi-layer defense mechanisms to counteract these evolving threats.
Dusting attack vs Replay attack Infographic
 techiny.com
techiny.com