SHA-256 and Keccak-256 are cryptographic hash functions widely used in blockchain technology, each offering distinct security features and performance characteristics. SHA-256, adopted by Bitcoin, provides robust collision resistance and a fixed 256-bit output length, ensuring data integrity and security across decentralized networks. Keccak-256, the basis for Ethereum's SHA-3 standard, utilizes a sponge construction that enhances resistance against length-extension attacks and improves efficiency in various cryptographic applications.
Table of Comparison
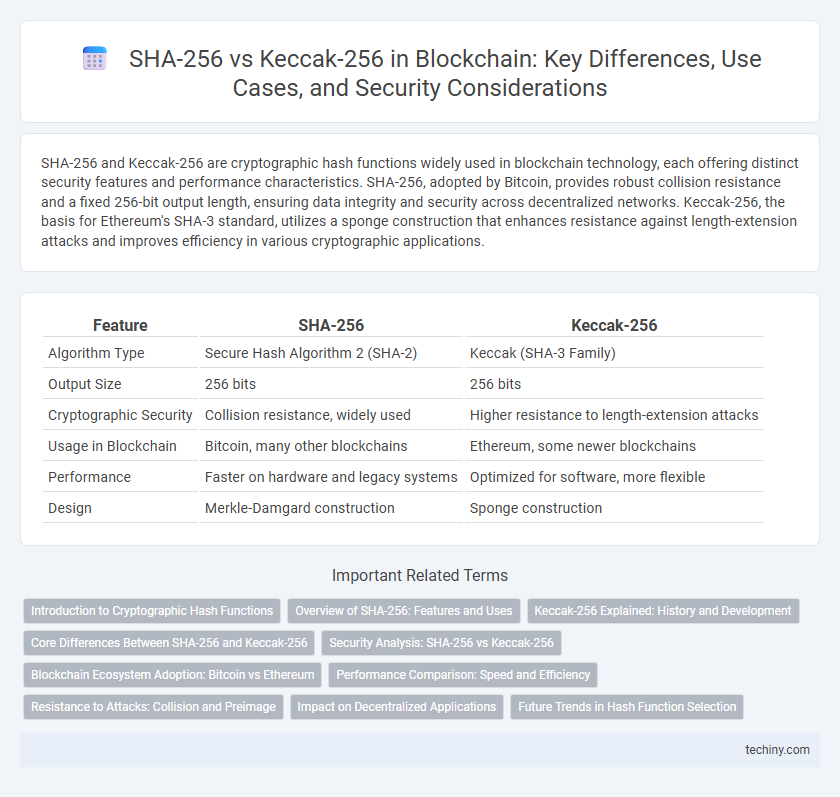
| Feature | SHA-256 | Keccak-256 |
|---|---|---|
| Algorithm Type | Secure Hash Algorithm 2 (SHA-2) | Keccak (SHA-3 Family) |
| Output Size | 256 bits | 256 bits |
| Cryptographic Security | Collision resistance, widely used | Higher resistance to length-extension attacks |
| Usage in Blockchain | Bitcoin, many other blockchains | Ethereum, some newer blockchains |
| Performance | Faster on hardware and legacy systems | Optimized for software, more flexible |
| Design | Merkle-Damgard construction | Sponge construction |
Introduction to Cryptographic Hash Functions
Cryptographic hash functions like SHA-256 and Keccak-256 serve as fundamental components in blockchain technology, ensuring data integrity and security. SHA-256, part of the SHA-2 family, operates with a 256-bit output and is widely used in Bitcoin, providing collision resistance and pre-image resistance. Keccak-256, the basis for SHA-3, employs a sponge construction that enhances security and flexibility, making it popular in Ethereum and other blockchain platforms.
Overview of SHA-256: Features and Uses
SHA-256 is a cryptographic hash function belonging to the SHA-2 family, producing a fixed 256-bit output from input data, ensuring data integrity and security. Its widespread adoption includes Bitcoin blockchain for mining and transaction verification, as well as digital signatures and certificates in cybersecurity. SHA-256's strong collision resistance and preimage resistance make it reliable for tamper-proof ledger entries and secure cryptographic applications.
Keccak-256 Explained: History and Development
Keccak-256, the underlying hash function of the SHA-3 standard, was developed through a rigorous competition organized by NIST to enhance cryptographic security beyond the SHA-2 family. Its sponge construction design offers strong resistance against collision, preimage, and length extension attacks, making it optimized for blockchain applications requiring robust integrity and security. Keccak-256's development emphasized flexibility and efficiency in secure hashing, leading to its adoption in Ethereum for transaction validation and smart contract verification.
Core Differences Between SHA-256 and Keccak-256
SHA-256 uses the Merkle-Damgard construction producing a fixed 256-bit hash with high collision resistance, while Keccak-256 employs the sponge construction enabling variable output length and increased security against length extension attacks. SHA-256 is widely utilized in Bitcoin's Proof of Work consensus, whereas Keccak-256 underpins Ethereum's hashing through its improved absorption and squeezing phases. The internal permutations and state sizes differ significantly, with SHA-256 operating on 512-bit blocks and Keccak-256 on 1600-bit state arrays, contributing to their distinct cryptographic profiles.
Security Analysis: SHA-256 vs Keccak-256
SHA-256 and Keccak-256 are cryptographic hash functions integral to blockchain security, with SHA-256 being widely used in Bitcoin and Keccak-256 serving as the foundation for Ethereum. SHA-256 provides collision resistance and preimage resistance based on its Merkle-Damgard structure, but Keccak-256's sponge construction offers enhanced security margins against length extension attacks and improved resilience to quantum computing threats. Security analyses reveal Keccak-256's superior resistance to differential and linear cryptanalysis, making it more robust for evolving blockchain applications requiring advanced cryptographic strength.
Blockchain Ecosystem Adoption: Bitcoin vs Ethereum
SHA-256 is the cryptographic hash function used by Bitcoin, providing a secure and efficient method for transaction verification and mining through its double-hashing process. Keccak-256, utilized by Ethereum as its underlying hash function, supports Ethereum's smart contract execution and decentralized applications with its resilience to length-extension attacks and better resistance to quantum attacks. The blockchain ecosystem adoption reflects these functions' alignment with network goals: Bitcoin prioritizes immutability and trustless monetary transfers, while Ethereum emphasizes programmable transactions and versatile dApp development.
Performance Comparison: Speed and Efficiency
SHA-256 processes data blocks at a speed of approximately 124 MB/s on modern CPUs, offering robust security with moderate computational overhead, while Keccak-256 (used in Ethereum's SHA-3) has a more complex sponge construction that results in slightly slower throughput, around 90 MB/s, but excels in hardware efficiency and resistance to certain attack vectors. Keccak-256's design allows better parallelism and flexibility for hardware implementations, making it more efficient in specialized environments despite being slower in pure software benchmarks compared to SHA-256. For applications prioritizing raw speed on general-purpose processors, SHA-256 generally outperforms Keccak-256, whereas Keccak-256 is favored for cryptographic flexibility and future-proof security in blockchain protocols.
Resistance to Attacks: Collision and Preimage
SHA-256 demonstrates strong collision resistance, making it computationally infeasible to find two distinct inputs that produce the same hash output, which is critical for blockchain security. Keccak-256, the basis for SHA-3, offers enhanced resistance to preimage attacks due to its sponge construction, improving security against attempts to reverse-engineer input from hash values. Both algorithms provide robust cryptographic strength, but Keccak-256's design offers improved resilience against certain attack vectors relevant for decentralized ledger technologies.
Impact on Decentralized Applications
SHA-256, the cryptographic hash function used in Bitcoin, offers strong collision resistance and widespread industry adoption, enabling secure transaction verification and miner consensus in decentralized applications. Keccak-256, chosen for Ethereum's smart contract platform, provides enhanced resistance to length extension attacks and better performance in keyed hashing, optimizing contract security and state integrity. The choice between SHA-256 and Keccak-256 significantly influences transaction throughput, security models, and interoperability within blockchain ecosystems.
Future Trends in Hash Function Selection
SHA-256 remains a cornerstone in blockchain security due to its widespread adoption and proven resistance to collision attacks. Keccak-256, underpinning Ethereum's shift to SHA-3 standards, offers enhanced security features like resistance to length-extension attacks, making it a strong contender for future-proof blockchains. Emerging trends indicate a gradual migration towards Keccak-based hashes as blockchain platforms seek higher security and performance in post-quantum cryptographic landscapes.
SHA-256 vs Keccak-256 Infographic
 techiny.com
techiny.com