Hashing transforms data into a fixed-size string of characters, serving as a unique digital fingerprint that ensures data integrity and is irreversible. Encryption converts data into a coded format that can be decrypted with the correct key, providing confidentiality and secure communication. In blockchain, hashing secures transaction records by linking blocks, while encryption protects sensitive information from unauthorized access.
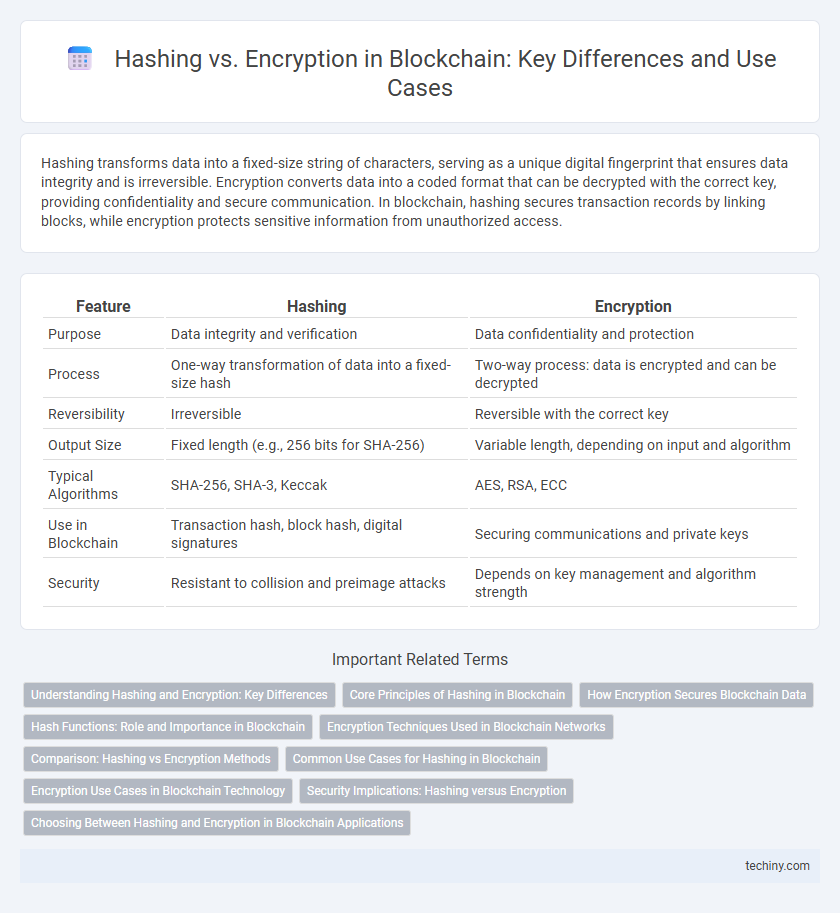
Table of Comparison
| Feature | Hashing | Encryption |
|---|---|---|
| Purpose | Data integrity and verification | Data confidentiality and protection |
| Process | One-way transformation of data into a fixed-size hash | Two-way process: data is encrypted and can be decrypted |
| Reversibility | Irreversible | Reversible with the correct key |
| Output Size | Fixed length (e.g., 256 bits for SHA-256) | Variable length, depending on input and algorithm |
| Typical Algorithms | SHA-256, SHA-3, Keccak | AES, RSA, ECC |
| Use in Blockchain | Transaction hash, block hash, digital signatures | Securing communications and private keys |
| Security | Resistant to collision and preimage attacks | Depends on key management and algorithm strength |
Understanding Hashing and Encryption: Key Differences
Hashing transforms data into a fixed-size string of characters, serving as a unique digital fingerprint for verifying data integrity, while encryption converts data into a coded format to protect confidentiality during transmission or storage. Hash functions in blockchain, such as SHA-256, are one-way and irreversible, ensuring tamper-evidence without revealing original data. Encryption algorithms like AES allow reversible data encoding, enabling authorized parties to decrypt and access sensitive information securely.
Core Principles of Hashing in Blockchain
Hashing in blockchain transforms input data into a fixed-size string of characters, ensuring data integrity through unique hash values that detect even minor alterations. It operates as a one-way cryptographic function, making it computationally infeasible to reverse or retrieve the original input from the hash output. This core principle guarantees the immutability and security of blockchain transactions by linking blocks through their cryptographic hashes.
How Encryption Secures Blockchain Data
Encryption secures blockchain data by converting sensitive information into ciphertext using cryptographic algorithms, ensuring only authorized parties with the correct decryption keys can access the original data. This process protects transaction details and user identities from unauthorized access and tampering, maintaining data confidentiality and integrity across decentralized networks. Strong encryption protocols like AES and RSA are integral to securing blockchain communications, wallet private keys, and smart contract interactions.
Hash Functions: Role and Importance in Blockchain
Hash functions play a critical role in blockchain technology by ensuring data integrity and security through the creation of unique digital fingerprints for each transaction. These cryptographic algorithms transform input data into fixed-length hash values that are irreversible, making tampering detectable and preventing data alteration. By enabling efficient data verification and maintaining the immutability of the blockchain ledger, hash functions underpin trust and transparency in decentralized networks.
Encryption Techniques Used in Blockchain Networks
Encryption techniques used in blockchain networks primarily include asymmetric cryptography (public-key cryptography) and symmetric cryptography. Asymmetric encryption, employing algorithms like RSA and Elliptic Curve Cryptography (ECC), ensures secure key exchange and digital signatures, while symmetric encryption methods such as AES provide data confidentiality within nodes. These encryption techniques maintain transaction privacy, authenticate participants, and protect sensitive blockchain data from unauthorized access.
Comparison: Hashing vs Encryption Methods
Hashing and encryption serve distinct purposes in blockchain security, where hashing generates a fixed-length output from input data, ensuring data integrity through irreversible transformations, while encryption encodes data into a cipher text that can be decrypted with a key, providing confidentiality. Hash functions like SHA-256 produce unique digital fingerprints critical for block identification and transaction verification, whereas encryption algorithms such as AES protect sensitive information from unauthorized access. Blockchain systems rely on hashing for data immutability and encryption for secure transmission and storage of private data within decentralized networks.
Common Use Cases for Hashing in Blockchain
Hashing plays a crucial role in blockchain by ensuring data integrity through the creation of unique digital fingerprints for each block, enabling efficient verification and tamper detection. It supports transaction identification by generating distinct, fixed-length hash codes that represent transaction data, facilitating quick searches and comparisons. Hashing also underpins consensus mechanisms like proof-of-work, where miners solve complex hash puzzles to validate new blocks and secure the network.
Encryption Use Cases in Blockchain Technology
Encryption in blockchain technology ensures data confidentiality by converting plaintext into ciphertext, making sensitive information accessible only to authorized parties. It is extensively used to secure private keys, protect transaction details, and enable secure communication between nodes within the network. Blockchain platforms leverage encryption algorithms like AES and RSA to maintain data integrity, prevent unauthorized access, and uphold privacy standards in decentralized environments.
Security Implications: Hashing versus Encryption
Hashing transforms data into a fixed-size hash, ensuring data integrity by detecting alterations, but it is a one-way process without reversal capability. Encryption secures data confidentiality by converting plaintext into ciphertext, requiring a key for decryption and enabling data recovery. Security implications highlight that hashing prevents tampering detection while encryption protects sensitive information from unauthorized access, making both critical yet complementary in blockchain security protocols.
Choosing Between Hashing and Encryption in Blockchain Applications
Selecting between hashing and encryption in blockchain applications depends on the intended functionality; hashing ensures data integrity by producing unique fixed-size outputs for any input, making it ideal for verifying transaction authenticity. Encryption secures data confidentiality by converting plaintext into ciphertext using keys, essential for protecting sensitive information on the blockchain. Choosing the appropriate method hinges on whether the priority is data verification or privacy, influencing security protocols and performance in decentralized systems.
Hashing vs Encryption Infographic
 techiny.com
techiny.com