Cloud Security Posture Management (CSPM) focuses on continuously monitoring and managing cloud infrastructure configurations to prevent misconfigurations and ensure compliance with security policies. Cloud Workload Protection Platforms (CWPP) provide real-time threat detection and defense for individual cloud workloads, including applications, containers, and virtual machines. Both solutions complement each other by addressing different layers of cloud security: CSPM secures the cloud environment, while CWPP protects the workloads running within it.
Table of Comparison
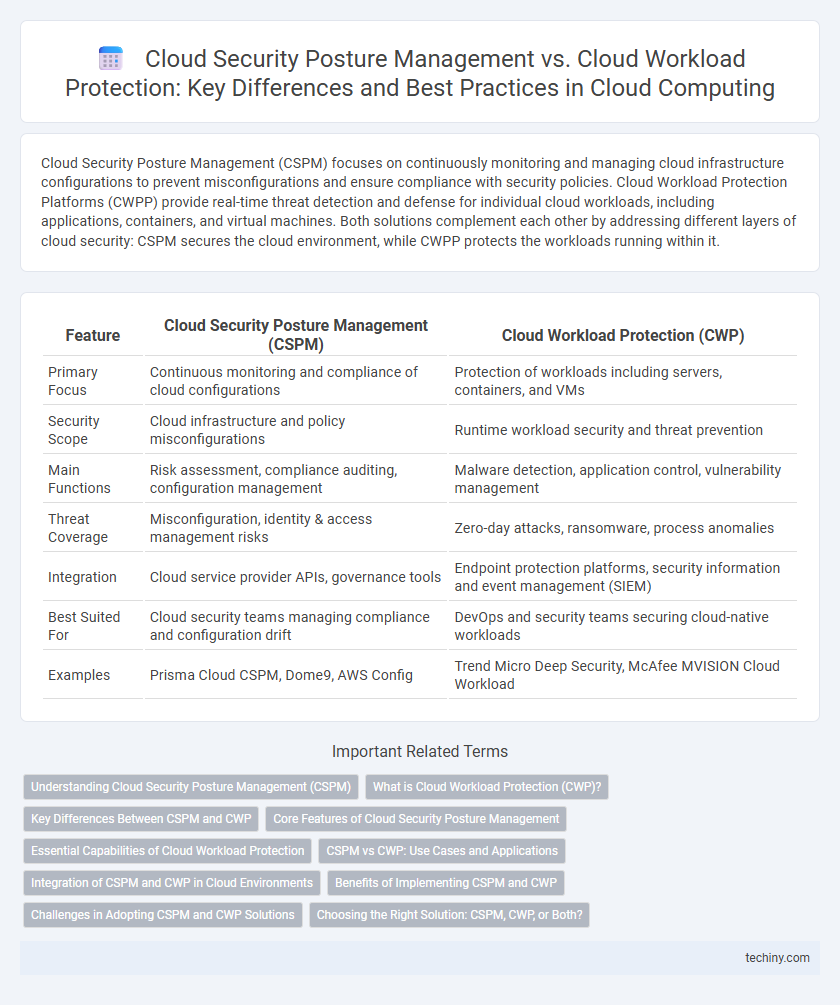
| Feature | Cloud Security Posture Management (CSPM) | Cloud Workload Protection (CWP) |
|---|---|---|
| Primary Focus | Continuous monitoring and compliance of cloud configurations | Protection of workloads including servers, containers, and VMs |
| Security Scope | Cloud infrastructure and policy misconfigurations | Runtime workload security and threat prevention |
| Main Functions | Risk assessment, compliance auditing, configuration management | Malware detection, application control, vulnerability management |
| Threat Coverage | Misconfiguration, identity & access management risks | Zero-day attacks, ransomware, process anomalies |
| Integration | Cloud service provider APIs, governance tools | Endpoint protection platforms, security information and event management (SIEM) |
| Best Suited For | Cloud security teams managing compliance and configuration drift | DevOps and security teams securing cloud-native workloads |
| Examples | Prisma Cloud CSPM, Dome9, AWS Config | Trend Micro Deep Security, McAfee MVISION Cloud Workload |
Understanding Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM) continuously monitors cloud environments to identify misconfigurations and compliance risks, ensuring security policies are enforced across multi-cloud infrastructures. CSPM integrates automated remediation workflows and real-time risk assessments to maintain a secure and compliant cloud posture. This enables organizations to reduce vulnerabilities by proactively addressing configuration drift and enforcing best practices in cloud security governance.
What is Cloud Workload Protection (CWP)?
Cloud Workload Protection (CWP) is a security solution designed to safeguard workloads running across hybrid, multi-cloud, and on-premises environments by providing real-time threat detection, vulnerability management, and compliance monitoring. CWP integrates runtime protection, behavioral analysis, and automated response capabilities to secure applications, containers, virtual machines, and serverless functions. This approach ensures consistent workload protection throughout the entire lifecycle, reducing risk and enhancing overall cloud security posture.
Key Differences Between CSPM and CWP
Cloud Security Posture Management (CSPM) primarily focuses on identifying and remediating misconfigurations and compliance risks across cloud infrastructure, ensuring alignment with security frameworks and policies. Cloud Workload Protection (CWP) centers on real-time protection of cloud workloads, including virtual machines, containers, and serverless functions, by detecting threats, vulnerabilities, and anomalous activities. The key difference lies in CSPM's broader cloud environment oversight versus CWP's granular, workload-specific threat prevention and response capabilities.
Core Features of Cloud Security Posture Management
Cloud Security Posture Management (CSPM) focuses on continuous monitoring, automated compliance enforcement, and risk assessment to identify misconfigurations and security vulnerabilities across cloud environments. It enhances visibility into cloud assets, enforces security policies, and provides real-time threat detection to prevent breaches. Core features include policy compliance checks, configuration auditing, and remediation workflows designed to maintain a secure cloud infrastructure.
Essential Capabilities of Cloud Workload Protection
Cloud Workload Protection (CWP) offers essential capabilities such as real-time threat detection, vulnerability management, and automated compliance enforcement tailored to dynamic cloud environments. It secures workloads across virtual machines, containers, and serverless functions by integrating runtime protection and behavior monitoring. Its proactive defense mechanisms safeguard against malware, unauthorized access, and configuration drift, ensuring robust workload resilience in multi-cloud infrastructures.
CSPM vs CWP: Use Cases and Applications
Cloud Security Posture Management (CSPM) automates the identification and remediation of risks across cloud infrastructures by continuously assessing configurations to comply with security policies and regulatory standards. Cloud Workload Protection (CWP) focuses on securing individual cloud workloads, such as virtual machines, containers, and serverless functions, by providing runtime protection, vulnerability management, and threat detection. CSPM is essential for preventing misconfigurations and ensuring compliance at the cloud environment level, while CWP is critical for real-time workload defense and safeguarding application-level assets.
Integration of CSPM and CWP in Cloud Environments
Integrating Cloud Security Posture Management (CSPM) with Cloud Workload Protection (CWP) enhances comprehensive cloud security by combining continuous compliance monitoring and real-time workload threat detection. CSPM ensures configuration and policy adherence across cloud infrastructures, while CWP offers in-depth protection for running workloads through vulnerability management and behavioral analysis. This integration enables automated risk remediation and unified security visibility, streamlining threat response in dynamic cloud environments.
Benefits of Implementing CSPM and CWP
Implementing Cloud Security Posture Management (CSPM) enhances continuous monitoring and automated compliance enforcement, reducing misconfigurations and security risks across cloud environments. Cloud Workload Protection (CWP) provides runtime defense and threat detection for cloud-based workloads, ensuring real-time protection against vulnerabilities and attacks. Combining CSPM and CWP enables comprehensive cloud security by addressing both configuration vulnerabilities and active workload threats, improving overall risk management and operational resilience.
Challenges in Adopting CSPM and CWP Solutions
Challenges in adopting Cloud Security Posture Management (CSPM) and Cloud Workload Protection (CWP) solutions include the complexity of integrating diverse cloud environments and the difficulty of maintaining continuous compliance with evolving security policies. Organizations often struggle with managing extensive data sets and real-time threat detection while minimizing performance impacts on cloud workloads. Ensuring comprehensive visibility across multi-cloud platforms and aligning security tools with dynamic workloads remain major obstacles in effective cloud security management.
Choosing the Right Solution: CSPM, CWP, or Both?
Choosing the right cloud security approach depends on organizational needs and risk profile, as Cloud Security Posture Management (CSPM) continuously monitors cloud configurations for compliance violations and misconfigurations, while Cloud Workload Protection (CWP) secures individual workloads with runtime protection and threat prevention. Enterprises with complex cloud environments may benefit from integrating both CSPM and CWP to ensure comprehensive visibility and protection across cloud infrastructure and application workloads. Evaluating workload sensitivity, regulatory requirements, and security automation capabilities guides the decision between implementing CSPM, CWP, or a combined solution for robust cloud defense.
Cloud Security Posture Management vs Cloud Workload Protection Infographic
 techiny.com
techiny.com