Data encryption at rest secures stored data by converting it into unreadable code, protecting it from unauthorized access and breaches while it resides on servers or storage devices. Data encryption in transit safeguards data as it travels across networks, ensuring confidentiality and integrity by preventing interception and tampering during transmission. Both encryption methods play critical roles in comprehensive cloud security strategies, addressing different vulnerabilities within data lifecycle protection.
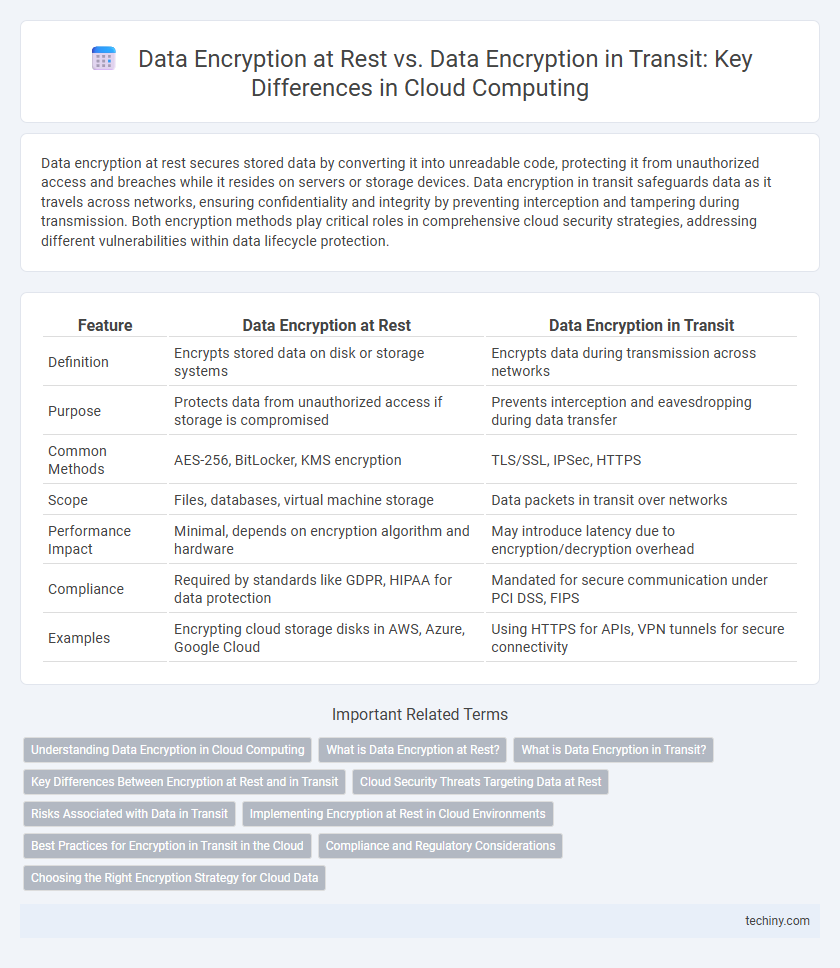
Table of Comparison
| Feature | Data Encryption at Rest | Data Encryption in Transit |
|---|---|---|
| Definition | Encrypts stored data on disk or storage systems | Encrypts data during transmission across networks |
| Purpose | Protects data from unauthorized access if storage is compromised | Prevents interception and eavesdropping during data transfer |
| Common Methods | AES-256, BitLocker, KMS encryption | TLS/SSL, IPSec, HTTPS |
| Scope | Files, databases, virtual machine storage | Data packets in transit over networks |
| Performance Impact | Minimal, depends on encryption algorithm and hardware | May introduce latency due to encryption/decryption overhead |
| Compliance | Required by standards like GDPR, HIPAA for data protection | Mandated for secure communication under PCI DSS, FIPS |
| Examples | Encrypting cloud storage disks in AWS, Azure, Google Cloud | Using HTTPS for APIs, VPN tunnels for secure connectivity |
Understanding Data Encryption in Cloud Computing
Data encryption in cloud computing secures sensitive information by converting data into unreadable formats, protecting it both at rest and in transit. Encryption at rest safeguards stored data on physical or virtual storage devices, preventing unauthorized access even if the storage medium is compromised. Encryption in transit protects data moving across networks by using protocols like TLS or SSL, ensuring confidentiality and integrity during transmission between cloud services and end-users.
What is Data Encryption at Rest?
Data encryption at rest secures stored data by converting it into an unreadable format using cryptographic algorithms, making it inaccessible without the appropriate decryption keys. This method protects sensitive information within cloud storage systems, databases, and backups from unauthorized access and potential breaches. Employing encryption at rest is essential for compliance with data protection regulations such as GDPR and HIPAA in cloud computing environments.
What is Data Encryption in Transit?
Data encryption in transit secures data as it travels across networks, preventing unauthorized access during transmission between devices or systems. This type of encryption typically uses protocols like TLS (Transport Layer Security) or SSL (Secure Sockets Layer) to protect the integrity and confidentiality of data moving through cloud environments. Ensuring encryption in transit is crucial for safeguarding sensitive information against interception or eavesdropping in cloud computing infrastructures.
Key Differences Between Encryption at Rest and in Transit
Data encryption at rest secures stored data on physical or virtual storage devices, protecting it from unauthorized access or breaches during periods of inactivity. In contrast, data encryption in transit safeguards data as it moves across networks, preventing interception or eavesdropping between endpoints. Key differences include encryption scope--static vs. dynamic data protection--and application layers, with at-rest encryption typically operating at the storage layer and in-transit encryption functioning at the communication layer, such as TLS for web traffic.
Cloud Security Threats Targeting Data at Rest
Data encryption at rest protects sensitive information stored on cloud servers from unauthorized access caused by physical theft, insider threats, or cyberattacks exploiting storage vulnerabilities. Cloud security threats targeting data at rest include ransomware attacks, data breaches through misconfigured storage buckets, and advanced persistent threats (APTs) that aim to exfiltrate or manipulate stored data. Implementing robust encryption algorithms such as AES-256, combined with strict access controls and key management protocols, strengthens defense against these attacks and ensures data confidentiality in cloud environments.
Risks Associated with Data in Transit
Data encryption in transit mitigates risks such as interception, man-in-the-middle attacks, and eavesdropping during data transmission across networks. Unlike encryption at rest, which secures data stored on devices or servers, encryption in transit protects data flowing through public or private communication channels vulnerable to unauthorized access. Implementing protocols like TLS and VPN ensures data confidentiality and integrity against external threats during transmission.
Implementing Encryption at Rest in Cloud Environments
Implementing encryption at rest in cloud environments involves securing stored data through encryption algorithms like AES-256, ensuring data remains protected on physical drives and cloud storage services. Cloud providers such as AWS, Azure, and Google Cloud offer native encryption solutions, including customer-managed keys (CMK) via services like AWS KMS and Azure Key Vault, enabling granular access control and compliance with standards like GDPR and HIPAA. Proper key management, combined with strong encryption protocols, minimizes risks of unauthorized data access while enabling seamless integration with cloud-based applications and services.
Best Practices for Encryption in Transit in the Cloud
Encrypting data in transit within cloud environments requires using strong protocols such as TLS 1.2 or higher to protect data from interception and tampering during transmission. Implementing mutual authentication and certificate pinning enhances the security of encrypted connections between clients and cloud services. Regularly updating encryption libraries and enforcing strict key management policies further ensure robust protection against emerging threats.
Compliance and Regulatory Considerations
Data encryption at rest ensures sensitive information stored on cloud servers complies with regulatory frameworks like GDPR, HIPAA, and PCI DSS by protecting data from unauthorized access during storage. Encryption in transit safeguards data moving across networks using protocols such as TLS, meeting compliance mandates for data integrity and confidentiality during transmission. Organizations must implement both encryption methods to fulfill legal requirements and avoid penalties associated with data breaches and non-compliance.
Choosing the Right Encryption Strategy for Cloud Data
Data encryption at rest secures stored cloud data by converting it into unreadable formats, protecting against unauthorized access during storage, while encryption in transit safeguards data as it moves between devices and cloud services, preventing interception or eavesdropping. Choosing the right encryption strategy involves assessing the sensitivity of the data, compliance requirements, and potential threat vectors, ensuring robust protection both during storage and transmission. Implementing combined encryption methods enhances overall cloud security by addressing vulnerabilities in both data storage and data transfer processes.
Data Encryption at Rest vs Data Encryption in Transit Infographic
 techiny.com
techiny.com