Centralized authentication in the Internet of Things (IoT) relies on a single authority to verify device identities, offering streamlined management but creating potential single points of failure and bottlenecks. Decentralized authentication distributes the verification process across multiple nodes, enhancing security and resilience by eliminating reliance on a central server, which is crucial for large-scale, heterogeneous IoT networks. Choosing between these approaches depends on specific IoT use cases, balancing scalability, security, and complexity requirements.
Table of Comparison
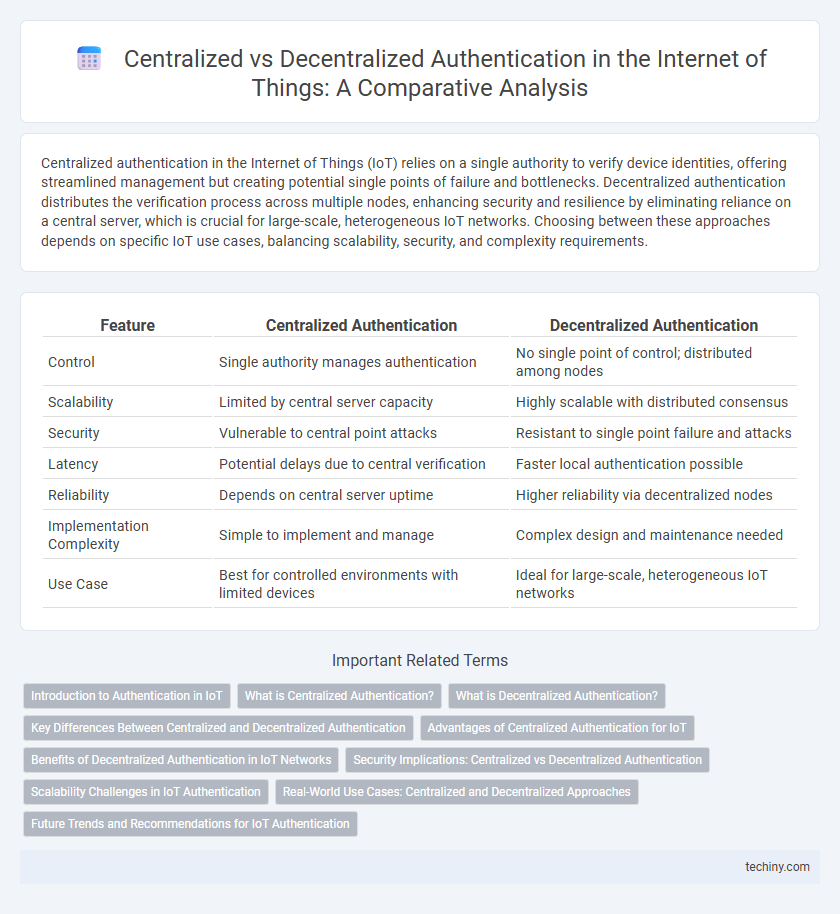
| Feature | Centralized Authentication | Decentralized Authentication |
|---|---|---|
| Control | Single authority manages authentication | No single point of control; distributed among nodes |
| Scalability | Limited by central server capacity | Highly scalable with distributed consensus |
| Security | Vulnerable to central point attacks | Resistant to single point failure and attacks |
| Latency | Potential delays due to central verification | Faster local authentication possible |
| Reliability | Depends on central server uptime | Higher reliability via decentralized nodes |
| Implementation Complexity | Simple to implement and manage | Complex design and maintenance needed |
| Use Case | Best for controlled environments with limited devices | Ideal for large-scale, heterogeneous IoT networks |
Introduction to Authentication in IoT
Authentication in IoT ensures secure device access by verifying identities before data exchange or network entry. Centralized authentication relies on a single trusted authority to validate device credentials, simplifying management but creating potential single points of failure. Decentralized authentication distributes trust among multiple nodes or blockchain systems, enhancing security and resilience in dynamic IoT environments.
What is Centralized Authentication?
Centralized authentication is a security process where a single server or authentication system manages user identity verification and access control for all connected Internet of Things (IoT) devices within a network. This approach simplifies user management by maintaining one central repository of credentials and policies, enabling consistent and streamlined access control across various IoT endpoints. Centralized authentication systems enhance security through unified monitoring and quicker response to unauthorized access attempts in IoT environments.
What is Decentralized Authentication?
Decentralized authentication in the Internet of Things (IoT) leverages blockchain technology or distributed ledger systems to verify device identities without relying on a single central authority. This approach enhances security by reducing single points of failure and enabling devices to authenticate through peer-to-peer consensus mechanisms. Decentralized authentication improves scalability and trust by ensuring data integrity and privacy across interconnected IoT devices.
Key Differences Between Centralized and Decentralized Authentication
Centralized authentication relies on a single authority or server to verify user identities, ensuring streamlined control but creating a single point of failure. Decentralized authentication distributes verification across multiple nodes or devices, enhancing security and resilience by eliminating dependency on a central server. The key differences include scalability, vulnerability to attacks, and control over user data, with decentralized systems offering greater privacy and fault tolerance in Internet of Things environments.
Advantages of Centralized Authentication for IoT
Centralized authentication in IoT enhances security by providing a single point for managing user credentials and access controls, reducing the risk of inconsistencies and unauthorized access. It simplifies device management and scalability, enabling seamless integration and efficient policy enforcement across large networks of connected devices. Centralized systems also facilitate faster incident response and easier auditing, crucial for maintaining robust IoT ecosystem security.
Benefits of Decentralized Authentication in IoT Networks
Decentralized authentication in IoT networks enhances security by reducing single points of failure and minimizing the risks of widespread breaches. It improves scalability by enabling devices to authenticate independently without relying on a central authority, which reduces latency and network congestion. This approach also boosts privacy since user data is not stored in a centralized database, lowering vulnerability to data leaks and unauthorized access.
Security Implications: Centralized vs Decentralized Authentication
Centralized authentication in IoT systems simplifies user management but creates a single point of failure, increasing vulnerability to cyberattacks and data breaches. Decentralized authentication leverages blockchain or distributed ledger technologies, enhancing security by eliminating central points of compromise and enabling tamper-resistant identity verification. The choice impacts overall system resilience, data privacy, and susceptibility to unauthorized access in IoT ecosystems.
Scalability Challenges in IoT Authentication
Centralized authentication systems in IoT face scalability challenges due to single points of failure and increased latency as device numbers grow exponentially, limiting real-time access control. Decentralized authentication leverages blockchain or distributed ledger technologies, enabling scalable, tamper-resistant identity management across vast IoT ecosystems. This distributed approach reduces bottlenecks and enhances resilience, critical for handling billions of interconnected devices.
Real-World Use Cases: Centralized and Decentralized Approaches
In Internet of Things (IoT) environments, centralized authentication systems such as AWS IoT Core enable streamlined device management and consistent security policies across smart home devices and industrial IoT deployments. Decentralized authentication, utilizing blockchain-based identity frameworks like IOTA and Hyperledger Indy, enhances trust and resilience in supply chain tracking and autonomous vehicle networks by eliminating single points of failure. Real-world implementations demonstrate centralized models excel in controlled environments with homogenous devices, while decentralized approaches thrive in large-scale, heterogeneous IoT ecosystems requiring robust data integrity and privacy.
Future Trends and Recommendations for IoT Authentication
Future trends in IoT authentication emphasize a shift from centralized systems, which are vulnerable to single points of failure, towards decentralized authentication leveraging blockchain and distributed ledger technologies for enhanced security and privacy. Implementing decentralized models supports scalable, tamper-resistant identity management, reducing reliance on central authorities and improving resilience against cyberattacks. Experts recommend adopting hybrid authentication frameworks that balance centralized control with decentralized verification to ensure robust, adaptive security suitable for diverse IoT ecosystems.
Centralized authentication vs Decentralized authentication Infographic
 techiny.com
techiny.com