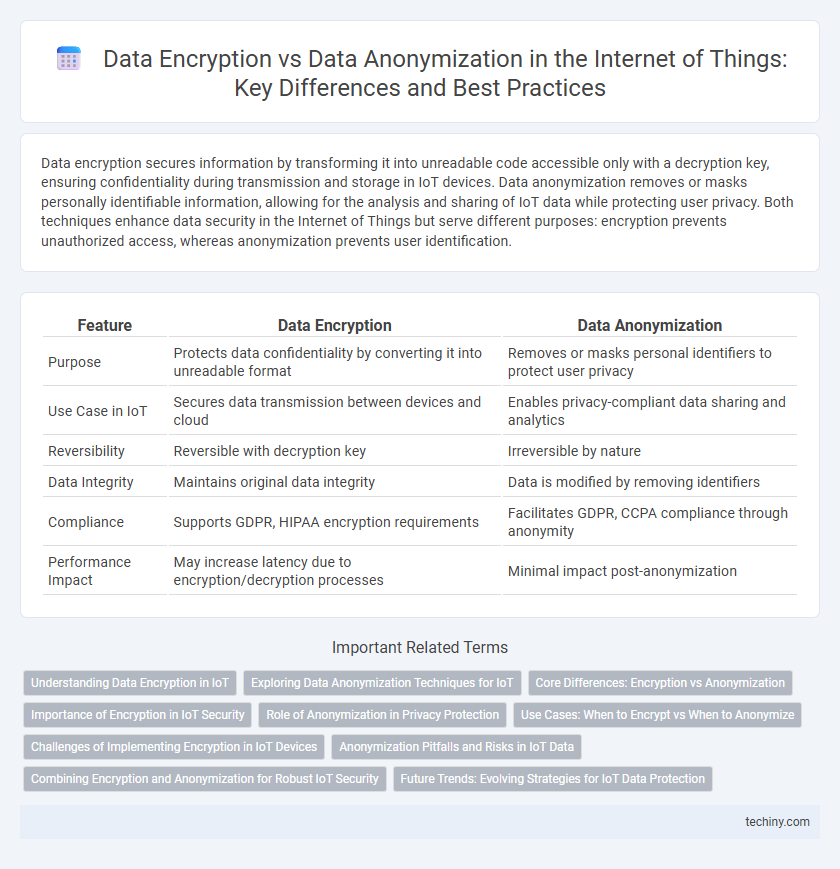
Data encryption secures information by transforming it into unreadable code accessible only with a decryption key, ensuring confidentiality during transmission and storage in IoT devices. Data anonymization removes or masks personally identifiable information, allowing for the analysis and sharing of IoT data while protecting user privacy. Both techniques enhance data security in the Internet of Things but serve different purposes: encryption prevents unauthorized access, whereas anonymization prevents user identification.
Table of Comparison
| Feature | Data Encryption | Data Anonymization |
|---|---|---|
| Purpose | Protects data confidentiality by converting it into unreadable format | Removes or masks personal identifiers to protect user privacy |
| Use Case in IoT | Secures data transmission between devices and cloud | Enables privacy-compliant data sharing and analytics |
| Reversibility | Reversible with decryption key | Irreversible by nature |
| Data Integrity | Maintains original data integrity | Data is modified by removing identifiers |
| Compliance | Supports GDPR, HIPAA encryption requirements | Facilitates GDPR, CCPA compliance through anonymity |
| Performance Impact | May increase latency due to encryption/decryption processes | Minimal impact post-anonymization |
Understanding Data Encryption in IoT
Data encryption in IoT secures sensitive information by converting it into unreadable ciphertext using cryptographic algorithms, ensuring data confidentiality during transmission and storage. Device-level encryption protocols like AES (Advanced Encryption Standard) safeguard data against unauthorized access and cyberattacks in real-time communication between IoT sensors and cloud platforms. Effective encryption is crucial for protecting metrics such as device identity, sensor readings, and user credentials within interconnected IoT ecosystems.
Exploring Data Anonymization Techniques for IoT
Data anonymization techniques for IoT focus on transforming personal or sensitive information into non-identifiable data while retaining its utility for analysis. Methods such as k-anonymity, differential privacy, and data masking obscure individual identities within interconnected devices, enhancing user privacy without compromising system functionality. This approach mitigates risks associated with data breaches and regulatory compliance, making it vital for secure IoT data management.
Core Differences: Encryption vs Anonymization
Data encryption transforms IoT data into unreadable code using cryptographic algorithms, ensuring that only authorized users with decryption keys can access the original information. Data anonymization irreversibly removes or alters personal identifiers from IoT data sets, preventing any possibility of tracing the data back to an individual user while retaining its usefulness for analysis. The core difference lies in encryption safeguarding data confidentiality during transmission and storage, whereas anonymization focuses on protecting user privacy by eliminating identifiable elements before data use.
Importance of Encryption in IoT Security
Data encryption in IoT ensures that sensitive information transmitted between devices remains confidential and protected from unauthorized access, significantly reducing the risk of data breaches. Unlike data anonymization, which removes or masks personally identifiable information, encryption actively secures data by converting it into unreadable code that can only be decrypted with the correct keys. Strong encryption protocols are essential for safeguarding IoT ecosystems, maintaining data integrity, and enabling secure communication across interconnected devices.
Role of Anonymization in Privacy Protection
Data anonymization plays a critical role in privacy protection within the Internet of Things (IoT) by transforming personally identifiable information into irreversible, non-identifiable data sets. Unlike data encryption, which secures data during transmission and storage but can be decrypted, anonymization ensures that even if data is accessed, individual identities remain protected. Effective anonymization techniques minimize privacy risks while enabling IoT systems to analyze aggregated data for insights without compromising user confidentiality.
Use Cases: When to Encrypt vs When to Anonymize
Data encryption is crucial for protecting sensitive IoT data during transmission and storage, especially in use cases involving personal health information or financial transactions, where confidentiality and compliance with regulations like GDPR are mandatory. Data anonymization suits scenarios such as smart city analytics and large-scale sensor data aggregation, enabling insights without exposing individual user identities or compromising privacy. Choosing between encryption and anonymization depends on the need for data usability versus privacy, with encryption preserving data integrity for authorized users and anonymization supporting privacy-preserving data sharing.
Challenges of Implementing Encryption in IoT Devices
Implementing data encryption in IoT devices faces challenges such as limited processing power, which constrains the use of complex cryptographic algorithms, and energy consumption concerns that impact battery-powered devices. The diversity of IoT hardware and communication protocols complicates the standardization and integration of robust encryption methods. Ensuring real-time data security while maintaining device performance and usability remains a critical obstacle in IoT encryption deployment.
Anonymization Pitfalls and Risks in IoT Data
Data anonymization in IoT often faces challenges such as re-identification attacks where attackers correlate anonymized data with external datasets to reveal sensitive information. Incomplete or poorly implemented anonymization techniques can lead to data leakage, compromising user privacy and violating regulatory requirements like GDPR. Effective anonymization requires continuous evaluation and robust techniques like differential privacy to mitigate these risks while enabling secure data sharing.
Combining Encryption and Anonymization for Robust IoT Security
Combining data encryption and anonymization enhances IoT security by protecting sensitive information both in transit and at rest, ensuring confidentiality and privacy against unauthorized access. Encryption safeguards data integrity through cryptographic algorithms, while anonymization removes or masks identifiers, preventing data tracing back to individuals or devices. Integrating these techniques addresses diverse cyber threats, supports regulatory compliance, and fortifies overall IoT ecosystem resilience.
Future Trends: Evolving Strategies for IoT Data Protection
Data encryption remains a cornerstone for IoT data protection by securing information through advanced cryptographic algorithms that evolve with emerging quantum-resistant techniques. Data anonymization is gaining traction, leveraging techniques such as differential privacy and federated learning to protect user identity while enabling data analytics. Future trends indicate a convergence of encryption and anonymization strategies, integrated with edge computing and AI-driven adaptive security protocols to address the increasing volume and sensitivity of IoT-generated data.
Data encryption vs Data anonymization Infographic
 techiny.com
techiny.com