Data encryption transforms IoT data into a secure format that is unreadable without the correct decryption key, ensuring confidentiality during transmission and storage. Data obfuscation, on the other hand, masks sensitive information to hide its true meaning while allowing limited usability, often used to protect data in less critical scenarios. Choosing between encryption and obfuscation depends on the required level of security and system performance constraints in IoT environments.
Table of Comparison
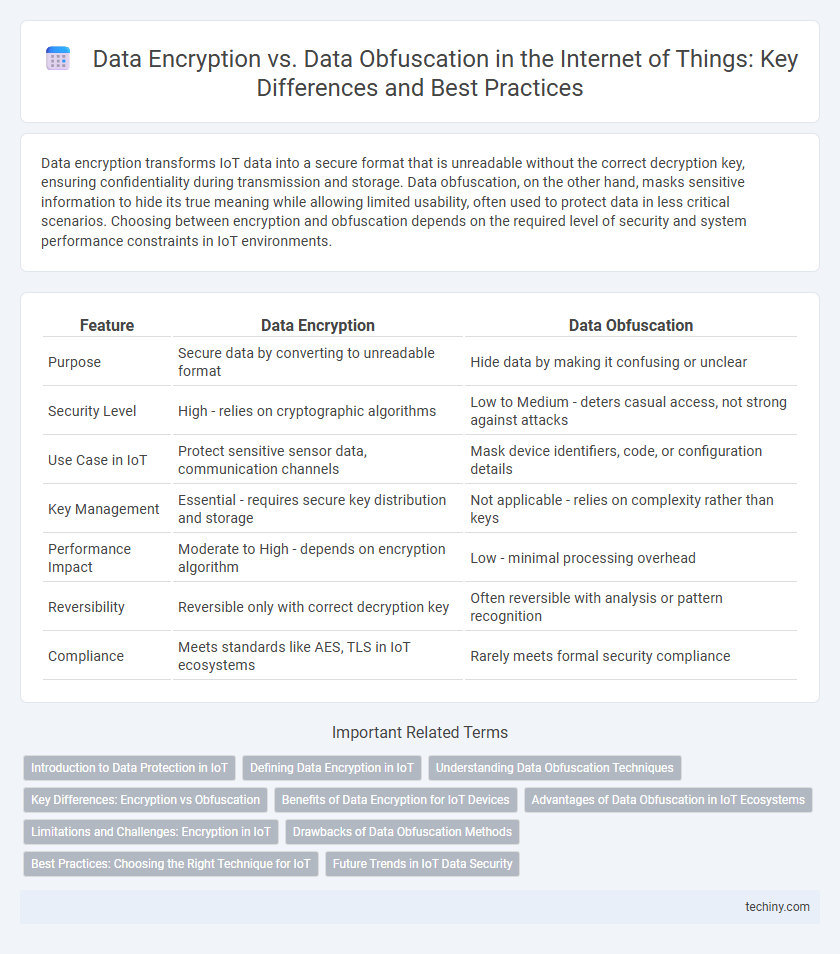
| Feature | Data Encryption | Data Obfuscation |
|---|---|---|
| Purpose | Secure data by converting to unreadable format | Hide data by making it confusing or unclear |
| Security Level | High - relies on cryptographic algorithms | Low to Medium - deters casual access, not strong against attacks |
| Use Case in IoT | Protect sensitive sensor data, communication channels | Mask device identifiers, code, or configuration details |
| Key Management | Essential - requires secure key distribution and storage | Not applicable - relies on complexity rather than keys |
| Performance Impact | Moderate to High - depends on encryption algorithm | Low - minimal processing overhead |
| Reversibility | Reversible only with correct decryption key | Often reversible with analysis or pattern recognition |
| Compliance | Meets standards like AES, TLS in IoT ecosystems | Rarely meets formal security compliance |
Introduction to Data Protection in IoT
Data encryption in IoT involves converting sensitive information into unreadable code to protect it from unauthorized access, ensuring confidentiality and integrity across connected devices. Data obfuscation masks data to make it less comprehensible, providing a layer of security while maintaining functionality in resource-constrained IoT environments. Both techniques play crucial roles in safeguarding IoT ecosystems, addressing vulnerabilities inherent in wireless communication and heterogeneous device networks.
Defining Data Encryption in IoT
Data encryption in IoT involves converting sensitive information collected by devices into coded formats to prevent unauthorized access during transmission and storage. This process uses cryptographic algorithms such as AES or RSA to ensure data integrity, confidentiality, and authentication across IoT networks. Effective encryption safeguards IoT ecosystems from cyber threats by protecting data exchanged between sensors, gateways, and cloud services.
Understanding Data Obfuscation Techniques
Data obfuscation techniques in the Internet of Things (IoT) involve methods such as tokenization, masking, and data perturbation to obscure sensitive information without fully encrypting it. These techniques help maintain data usability for analytics while reducing the risk of exposing personally identifiable information (PII) or critical device data during transmission. Understanding the balance between effective obfuscation and preserving data integrity is crucial for enhancing IoT security frameworks.
Key Differences: Encryption vs Obfuscation
Data encryption in the Internet of Things (IoT) secures information by converting plaintext into ciphertext using cryptographic keys, ensuring confidentiality and preventing unauthorized access. Data obfuscation, in contrast, disguises data by altering its appearance or structure without necessarily using cryptographic methods, primarily aiming to deter casual snooping rather than provide robust security. Encryption offers mathematically provable protection essential for sensitive IoT data, while obfuscation is often employed as a lightweight technique to hinder reverse engineering or data leakage in resource-constrained IoT devices.
Benefits of Data Encryption for IoT Devices
Data encryption in IoT devices ensures secure communication by converting sensitive information into unreadable code, preventing unauthorized access and cyberattacks. It enhances data privacy and integrity, protecting critical systems from interception and tampering during transmission. Strong encryption protocols like AES and TLS support compliance with industry regulations, safeguarding user data and maintaining trust in interconnected environments.
Advantages of Data Obfuscation in IoT Ecosystems
Data obfuscation in IoT ecosystems enhances security by making sensitive information unintelligible to unauthorized users without altering its original format, thereby maintaining system functionality. It offers lightweight protection suitable for resource-constrained IoT devices, reducing computational overhead compared to complex encryption algorithms. This approach supports real-time data processing and seamless interoperability among diverse IoT applications while mitigating risks of data breaches and unauthorized access.
Limitations and Challenges: Encryption in IoT
Encryption in IoT faces significant challenges due to limited processing power and battery life of connected devices, which constrain the use of computationally intensive algorithms. Key management, including secure key distribution and storage, remains a critical limitation in large-scale IoT deployments. Furthermore, encryption solutions must balance security with latency requirements, as delayed communication can impact real-time IoT applications.
Drawbacks of Data Obfuscation Methods
Data obfuscation methods in the Internet of Things often introduce significant performance overhead, resulting in slower data processing and increased energy consumption on resource-constrained devices. The lack of standardized protocols for obfuscation techniques leads to inconsistent protection levels and potential vulnerabilities against advanced cyber threats. Furthermore, obfuscated data can complicate legitimate data analytics and troubleshooting, diminishing operational efficiency and reliability in IoT ecosystems.
Best Practices: Choosing the Right Technique for IoT
Data encryption offers robust protection by converting IoT data into unreadable ciphertext, ensuring confidentiality during transmission and storage. Data obfuscation masks sensitive information through techniques like tokenization or anonymization, useful for safeguarding data in less critical environments or during development. Best practices dictate employing encryption for high-risk IoT data, while obfuscation complements security by reducing exposure of non-critical data, balancing performance and privacy in IoT systems.
Future Trends in IoT Data Security
Future trends in IoT data security emphasize advances in data encryption techniques such as homomorphic encryption and quantum-resistant algorithms to safeguard sensitive information against evolving cyber threats. Data obfuscation methods, including dynamic tokenization and AI-driven anonymization, will complement encryption by enhancing privacy and reducing attack surfaces. Emerging IoT frameworks are expected to integrate hybrid security models combining encryption and obfuscation to ensure resilient, scalable protection for billions of connected devices.
Data Encryption vs Data Obfuscation Infographic
 techiny.com
techiny.com