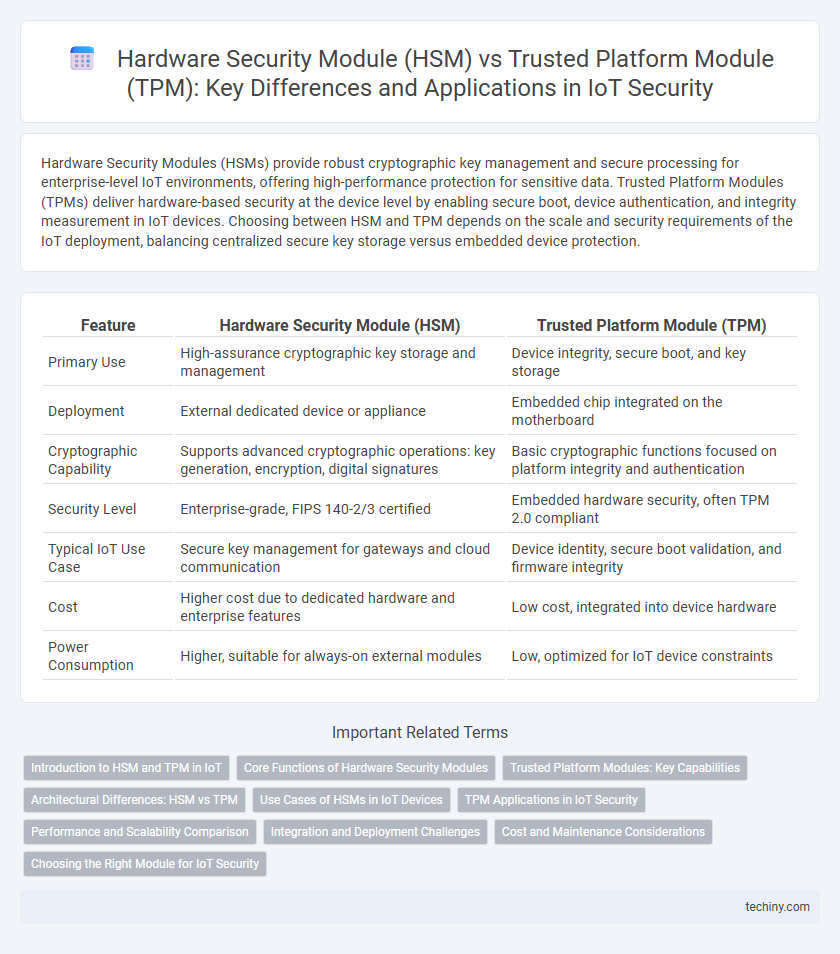
Hardware Security Modules (HSMs) provide robust cryptographic key management and secure processing for enterprise-level IoT environments, offering high-performance protection for sensitive data. Trusted Platform Modules (TPMs) deliver hardware-based security at the device level by enabling secure boot, device authentication, and integrity measurement in IoT devices. Choosing between HSM and TPM depends on the scale and security requirements of the IoT deployment, balancing centralized secure key storage versus embedded device protection.
Table of Comparison
| Feature | Hardware Security Module (HSM) | Trusted Platform Module (TPM) |
|---|---|---|
| Primary Use | High-assurance cryptographic key storage and management | Device integrity, secure boot, and key storage |
| Deployment | External dedicated device or appliance | Embedded chip integrated on the motherboard |
| Cryptographic Capability | Supports advanced cryptographic operations: key generation, encryption, digital signatures | Basic cryptographic functions focused on platform integrity and authentication |
| Security Level | Enterprise-grade, FIPS 140-2/3 certified | Embedded hardware security, often TPM 2.0 compliant |
| Typical IoT Use Case | Secure key management for gateways and cloud communication | Device identity, secure boot validation, and firmware integrity |
| Cost | Higher cost due to dedicated hardware and enterprise features | Low cost, integrated into device hardware |
| Power Consumption | Higher, suitable for always-on external modules | Low, optimized for IoT device constraints |
Introduction to HSM and TPM in IoT
Hardware Security Modules (HSMs) and Trusted Platform Modules (TPMs) serve critical roles in securing IoT devices by providing hardware-based cryptographic functions. HSMs primarily offer robust key management and encryption capabilities for enterprise-level IoT infrastructure, ensuring protection of sensitive data and keys during communication and storage. TPMs are specialized microcontrollers embedded in IoT devices, designed to securely generate, store, and manage cryptographic keys, enabling device authentication and integrity verification at the hardware level.
Core Functions of Hardware Security Modules
Hardware Security Modules (HSMs) provide robust cryptographic processing, including key generation, encryption, decryption, and secure key storage, essential for protecting sensitive data in IoT environments. HSMs are designed to manage high-volume cryptographic operations with tamper-resistant physical security, ensuring the integrity and confidentiality of IoT devices' credentials and transactions. Unlike Trusted Platform Modules (TPMs), which focus on device identity and platform integrity attestation, HSMs deliver scalable and centralized key management crucial for enterprise-level IoT deployments.
Trusted Platform Modules: Key Capabilities
Trusted Platform Modules (TPMs) provide robust hardware-based security for Internet of Things (IoT) devices by generating, storing, and managing cryptographic keys within a tamper-resistant environment. TPMs enable secure boot processes, attestation, and device identity verification, ensuring data integrity and preventing unauthorized access. Their integration supports encryption, authentication, and secure firmware updates, enhancing the overall trustworthiness of IoT ecosystems.
Architectural Differences: HSM vs TPM
HSMs are dedicated, tamper-resistant cryptographic devices designed to securely manage and store encryption keys at a hardware level, typically used in enterprise environments for high-assurance cryptographic operations. TPMs are integrated microcontrollers embedded within IoT devices or computers, providing hardware root of trust by securely storing platform measurements and keys to ensure device integrity and secure boot processes. The architectural difference lies in HSMs being specialized, standalone units with extensive cryptographic functionality, while TPMs offer a compact, cost-effective solution focused primarily on device authentication and integrity verification.
Use Cases of HSMs in IoT Devices
Hardware Security Modules (HSMs) in IoT devices provide robust cryptographic key management, ensuring secure generation, storage, and usage of encryption keys critical for device authentication and data integrity. HSMs are essential in large-scale IoT deployments, such as smart grids and industrial automation systems, where high-speed cryptographic operations and compliance with stringent security standards are required. Their use cases include protecting sensitive telemetry data, enabling secure firmware updates, and facilitating mutual device-to-device and device-to-cloud authentication in complex IoT ecosystems.
TPM Applications in IoT Security
Trusted Platform Module (TPM) enhances IoT security by providing hardware-based cryptographic functions such as secure key storage, device authentication, and platform integrity verification. TPM chips enable robust device identity management and facilitate secure boot processes, preventing unauthorized firmware modifications in IoT devices. Unlike Hardware Security Modules (HSM), TPMs are embedded directly into IoT hardware, making them ideal for resource-constrained environments requiring low-power, tamper-resistant security solutions.
Performance and Scalability Comparison
Hardware Security Modules (HSM) deliver high-performance cryptographic processing with dedicated hardware accelerators, ideal for large-scale IoT deployments requiring rapid encryption and key management. Trusted Platform Modules (TPM) offer moderate performance suitable for individual IoT devices with limited resources, focusing on secure boot and device integrity rather than throughput. Scalability favors HSMs in centralized environments managing thousands of devices, while TPMs excel in distributed IoT endpoints where lightweight, cost-effective security is essential.
Integration and Deployment Challenges
Hardware Security Modules (HSMs) offer robust cryptographic key management but often face complex integration and deployment challenges in IoT environments due to their size, power requirements, and cost. Trusted Platform Modules (TPMs) provide a more compact, cost-effective solution for secure boot and hardware-based authentication but may lack the extensive key management capabilities of HSMs. Selecting between HSM and TPM depends on balancing security needs with the constraints of IoT device form factors, power consumption, and deployment scalability.
Cost and Maintenance Considerations
Hardware Security Modules (HSMs) typically involve higher initial costs and ongoing maintenance expenses due to their advanced cryptographic capabilities and enterprise-grade features, making them suitable for large-scale IoT deployments requiring robust security. Trusted Platform Modules (TPMs) offer a more cost-effective solution with lower maintenance requirements, ideal for IoT devices focused on basic hardware-based security functions and scalability. Evaluating the total cost of ownership, including firmware updates and physical security, is essential for selecting the appropriate module within IoT ecosystems.
Choosing the Right Module for IoT Security
Selecting the optimal security module for IoT devices hinges on understanding the distinct features of Hardware Security Modules (HSM) and Trusted Platform Modules (TPM). HSMs offer high-performance cryptographic processing and key management, ideal for enterprise-level IoT deployments requiring robust, scalable security infrastructures. TPMs provide a cost-effective, hardware-based root of trust tailored for device authentication and secure boot processes in consumer and industrial IoT applications.
Hardware Security Module (HSM) vs Trusted Platform Module (TPM) Infographic
 techiny.com
techiny.com