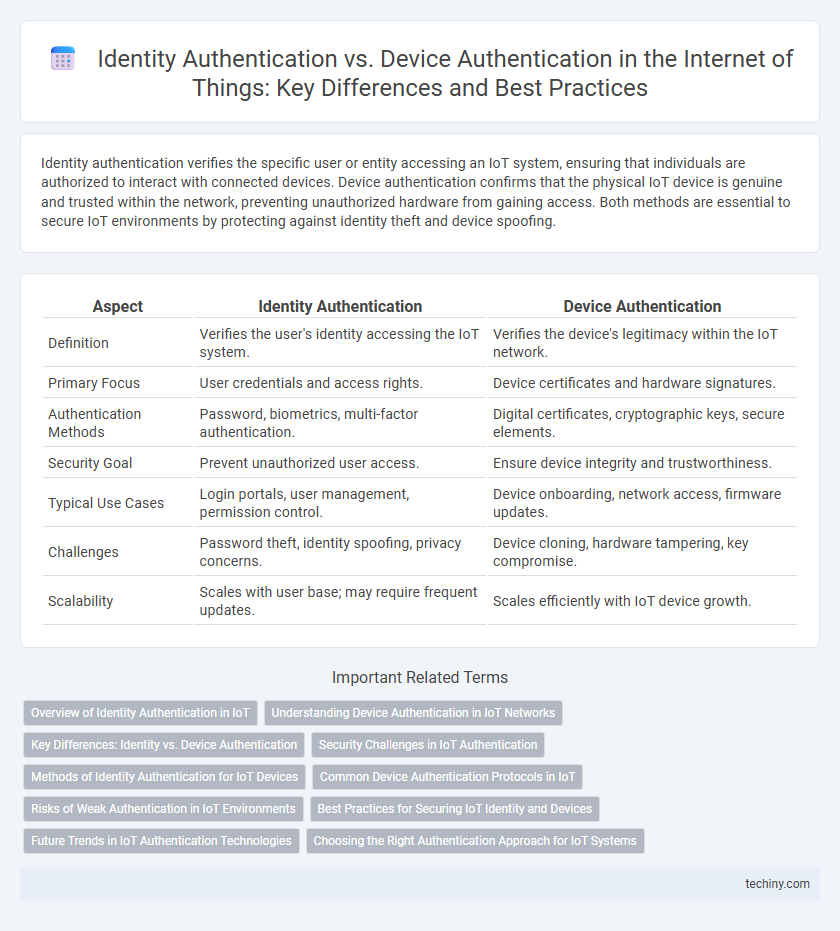
Identity authentication verifies the specific user or entity accessing an IoT system, ensuring that individuals are authorized to interact with connected devices. Device authentication confirms that the physical IoT device is genuine and trusted within the network, preventing unauthorized hardware from gaining access. Both methods are essential to secure IoT environments by protecting against identity theft and device spoofing.
Table of Comparison
| Aspect | Identity Authentication | Device Authentication |
|---|---|---|
| Definition | Verifies the user's identity accessing the IoT system. | Verifies the device's legitimacy within the IoT network. |
| Primary Focus | User credentials and access rights. | Device certificates and hardware signatures. |
| Authentication Methods | Password, biometrics, multi-factor authentication. | Digital certificates, cryptographic keys, secure elements. |
| Security Goal | Prevent unauthorized user access. | Ensure device integrity and trustworthiness. |
| Typical Use Cases | Login portals, user management, permission control. | Device onboarding, network access, firmware updates. |
| Challenges | Password theft, identity spoofing, privacy concerns. | Device cloning, hardware tampering, key compromise. |
| Scalability | Scales with user base; may require frequent updates. | Scales efficiently with IoT device growth. |
Overview of Identity Authentication in IoT
Identity authentication in IoT verifies the legitimacy of users or entities accessing the network, relying on methods like biometrics, passwords, or multi-factor authentication to ensure secure access. This process contrasts with device authentication, which validates the hardware devices themselves through digital certificates or cryptographic keys. Effective identity authentication prevents unauthorized access and protects sensitive IoT data by confirming that only verified identities can interact with connected systems.
Understanding Device Authentication in IoT Networks
Device authentication in IoT networks ensures that each connected device is verified before accessing the system, preventing unauthorized entry and maintaining network integrity. Unlike identity authentication, which verifies users, device authentication relies on cryptographic methods such as digital certificates, secure keys, and hardware tokens to confirm the legitimacy of devices. Effective device authentication reduces security risks, enhances trust, and supports scalable management of IoT ecosystems.
Key Differences: Identity vs. Device Authentication
Identity authentication in the Internet of Things (IoT) verifies the user's credentials to grant access, focusing on who is interacting with the system. Device authentication ensures the legitimacy of the IoT device itself by validating hardware identifiers or cryptographic keys, emphasizing what is connecting to the network. Key differences include identity authentication relying on user-centric data like passwords or biometrics, while device authentication depends on unique device IDs or digital certificates to prevent unauthorized hardware access.
Security Challenges in IoT Authentication
Identity authentication verifies the legitimacy of users accessing IoT systems, while device authentication ensures that only authorized devices connect within the network, both critical in mitigating unauthorized access. Security challenges in IoT authentication include resource constraints, susceptibility to spoofing attacks, and the complexity of managing diverse and heterogeneous devices. Robust authentication protocols and lightweight cryptographic algorithms are essential to address these vulnerabilities and enhance overall IoT security.
Methods of Identity Authentication for IoT Devices
Methods of identity authentication for IoT devices include multifactor authentication, biometric verification, and cryptographic techniques such as digital certificates and public key infrastructure (PKI). Device identity authentication often leverages device fingerprinting and hardware-based security modules like Trusted Platform Module (TPM) to ensure trusted access. Implementing robust identity authentication methods enhances security by preventing unauthorized access and ensuring data integrity across IoT networks.
Common Device Authentication Protocols in IoT
Common device authentication protocols in IoT include MQTT with TLS, DTLS for constrained devices, and OAuth 2.0 for delegated authorization. These protocols ensure device identity verification through cryptographic methods like digital certificates and token-based authentication, preventing unauthorized access within IoT networks. Device authentication focuses on the legitimacy of the device itself, whereas identity authentication involves verifying the actual user or entity behind the device.
Risks of Weak Authentication in IoT Environments
Weak identity authentication in IoT environments exposes sensitive user information to cybercriminals, resulting in privacy breaches and unauthorized access. Insufficient device authentication increases the risk of rogue devices infiltrating networks, leading to data manipulation and service disruption. These vulnerabilities undermine overall system integrity and can cause significant operational and financial damage.
Best Practices for Securing IoT Identity and Devices
Effective IoT security requires distinct strategies for identity authentication, which verifies user credentials, and device authentication, ensuring IoT devices are legitimate before network access. Best practices include employing multi-factor authentication (MFA) for user identities and utilizing cryptographic certificates or hardware security modules (HSM) to authenticate devices. Implementing continuous monitoring and automated anomaly detection enhances protection against identity spoofing and unauthorized device access in IoT ecosystems.
Future Trends in IoT Authentication Technologies
Future trends in IoT authentication technologies emphasize the integration of decentralized identity authentication methods alongside device authentication to enhance security and privacy. Advances include blockchain-based identity frameworks that ensure immutable user credentials while leveraging hardware-based device authentication techniques such as Trusted Platform Modules (TPM) and Physically Unclonable Functions (PUFs) to validate device integrity. Combining these technologies supports scalable, multi-factor authentication systems vital for addressing the growing complexity and volume of interconnected IoT devices.
Choosing the Right Authentication Approach for IoT Systems
Choosing the right authentication approach for IoT systems hinges on the distinction between identity authentication and device authentication. Identity authentication verifies the user's credentials, ensuring authorized access to IoT services, while device authentication confirms the legitimacy of the hardware itself, preventing unauthorized or compromised devices from joining the network. Effective IoT security often demands a balanced integration of both methods to safeguard sensitive data and maintain system integrity across diverse connected environments.
identity authentication vs device authentication Infographic
 techiny.com
techiny.com