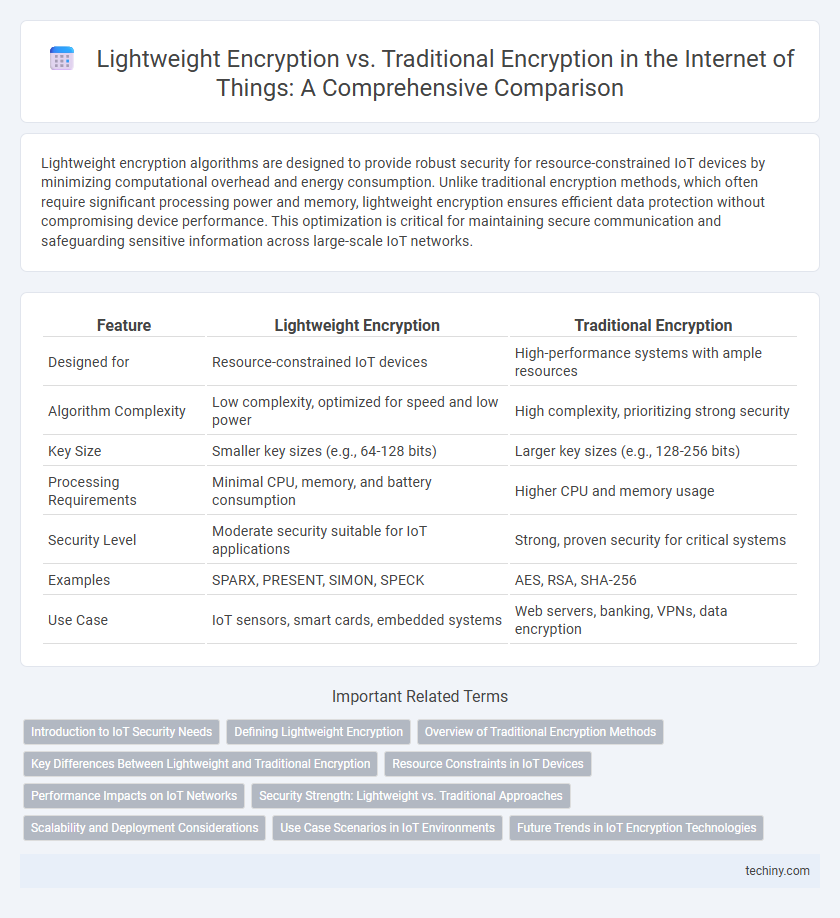
Lightweight encryption algorithms are designed to provide robust security for resource-constrained IoT devices by minimizing computational overhead and energy consumption. Unlike traditional encryption methods, which often require significant processing power and memory, lightweight encryption ensures efficient data protection without compromising device performance. This optimization is critical for maintaining secure communication and safeguarding sensitive information across large-scale IoT networks.
Table of Comparison
| Feature | Lightweight Encryption | Traditional Encryption |
|---|---|---|
| Designed for | Resource-constrained IoT devices | High-performance systems with ample resources |
| Algorithm Complexity | Low complexity, optimized for speed and low power | High complexity, prioritizing strong security |
| Key Size | Smaller key sizes (e.g., 64-128 bits) | Larger key sizes (e.g., 128-256 bits) |
| Processing Requirements | Minimal CPU, memory, and battery consumption | Higher CPU and memory usage |
| Security Level | Moderate security suitable for IoT applications | Strong, proven security for critical systems |
| Examples | SPARX, PRESENT, SIMON, SPECK | AES, RSA, SHA-256 |
| Use Case | IoT sensors, smart cards, embedded systems | Web servers, banking, VPNs, data encryption |
Introduction to IoT Security Needs
Lightweight encryption is essential for IoT security due to the limited processing power, memory, and energy resources of connected devices. Traditional encryption algorithms like AES and RSA offer strong security but often require higher computational capacity, making them less suitable for low-power IoT environments. Ensuring data confidentiality, integrity, and authentication in IoT ecosystems demands encryption solutions optimized for efficiency without compromising robust protection.
Defining Lightweight Encryption
Lightweight encryption is a specialized cryptographic approach designed for resource-constrained devices in the Internet of Things (IoT) ecosystem, offering robust security with minimal computational power, memory, and energy consumption. Unlike traditional encryption algorithms such as AES or RSA, lightweight encryption emphasizes efficiency and speed while maintaining cryptographic strength suitable for low-power IoT sensors and embedded systems. Protocols like SPECK, PRESENT, and SIMON exemplify lightweight encryption methods tailored to secure data transmission in pervasive IoT environments without compromising device performance.
Overview of Traditional Encryption Methods
Traditional encryption methods like AES and RSA rely on complex algorithms designed to offer strong security through extensive computational processes. These methods typically require significant processing power and energy consumption, making them less suitable for resource-constrained Internet of Things (IoT) devices. Despite their robustness, traditional encryption schemes often introduce latency and are challenging to implement efficiently in IoT environments with limited hardware capabilities.
Key Differences Between Lightweight and Traditional Encryption
Lightweight encryption algorithms are specifically designed for resource-constrained Internet of Things (IoT) devices, offering reduced computational overhead and lower power consumption compared to traditional encryption methods. These algorithms use smaller key sizes and simpler operations to maintain security while optimizing performance in environments with limited memory and processing capabilities. Traditional encryption standards like AES or RSA provide robust security but often require significant computational resources, making them less suitable for IoT applications demanding efficient, low-latency encryption.
Resource Constraints in IoT Devices
Lightweight encryption algorithms are specifically designed to address the severe resource constraints of IoT devices, such as limited processing power, memory, and energy supply, which traditional encryption methods struggle to accommodate efficiently. These optimized cryptographic solutions enable secure communication without overburdening the device's CPU and battery, ensuring longer operational life and faster data processing. Implementing lightweight encryption enhances overall IoT security while maintaining device performance within the constraints of low-cost and compact hardware architectures.
Performance Impacts on IoT Networks
Lightweight encryption significantly enhances performance in IoT networks by reducing computational overhead and power consumption, critical for resource-constrained devices. Traditional encryption algorithms, while more secure, often introduce latency and increase processing time, hindering real-time data transmission in IoT ecosystems. Optimizing encryption for IoT ensures faster data security without compromising device efficiency or network responsiveness.
Security Strength: Lightweight vs. Traditional Approaches
Lightweight encryption algorithms, designed for resource-constrained Internet of Things (IoT) devices, offer a balance between security strength and computational efficiency but may present vulnerabilities compared to traditional encryption standards like AES. Traditional encryption methods provide robust security through well-established cryptographic principles and longer key lengths, making them more resistant to sophisticated attacks but less suitable for low-power IoT environments. The trade-off between these approaches hinges on deploying lightweight encryption for efficient IoT communication while ensuring adequate protection against emerging cyber threats.
Scalability and Deployment Considerations
Lightweight encryption algorithms in the Internet of Things (IoT) offer enhanced scalability by requiring minimal computational resources, enabling seamless deployment across large networks of resource-constrained devices. Traditional encryption methods, while robust, often face challenges in IoT environments due to their heavy processing demands and energy consumption, limiting widespread adoption. Prioritizing lightweight cryptography ensures efficient scalability and flexible deployment, crucial for diverse IoT ecosystems with varying device capabilities.
Use Case Scenarios in IoT Environments
Lightweight encryption algorithms are specifically designed for resource-constrained IoT devices, enabling efficient data protection in scenarios like smart home automation and wearable health monitors where low power and limited processing capabilities are critical. Traditional encryption methods, such as AES and RSA, are more suitable for IoT gateways and cloud services that possess higher computational resources and require robust security for data aggregation and analytics. Selecting the appropriate encryption approach depends on balancing security requirements with the device's hardware limitations and the sensitivity of transmitted data within diverse IoT deployment environments.
Future Trends in IoT Encryption Technologies
Lightweight encryption protocols are increasingly favored in IoT environments due to their ability to provide robust security while minimizing computational overhead and power consumption, essential for resource-constrained devices. Emerging trends emphasize the integration of post-quantum cryptographic algorithms with lightweight encryption to future-proof IoT networks against quantum attacks. Advances in hardware acceleration and adaptive encryption schemes aim to balance security and performance, enabling scalable and efficient protection across diverse IoT ecosystems.
Lightweight encryption vs Traditional encryption Infographic
 techiny.com
techiny.com