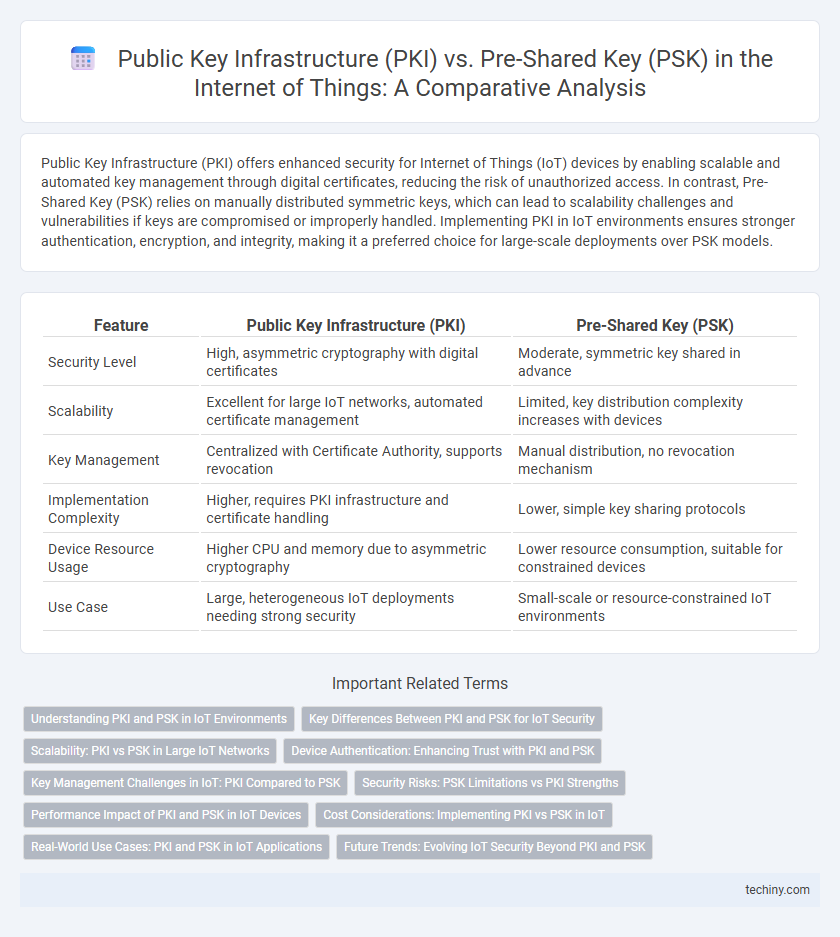
Public Key Infrastructure (PKI) offers enhanced security for Internet of Things (IoT) devices by enabling scalable and automated key management through digital certificates, reducing the risk of unauthorized access. In contrast, Pre-Shared Key (PSK) relies on manually distributed symmetric keys, which can lead to scalability challenges and vulnerabilities if keys are compromised or improperly handled. Implementing PKI in IoT environments ensures stronger authentication, encryption, and integrity, making it a preferred choice for large-scale deployments over PSK models.
Table of Comparison
| Feature | Public Key Infrastructure (PKI) | Pre-Shared Key (PSK) |
|---|---|---|
| Security Level | High, asymmetric cryptography with digital certificates | Moderate, symmetric key shared in advance |
| Scalability | Excellent for large IoT networks, automated certificate management | Limited, key distribution complexity increases with devices |
| Key Management | Centralized with Certificate Authority, supports revocation | Manual distribution, no revocation mechanism |
| Implementation Complexity | Higher, requires PKI infrastructure and certificate handling | Lower, simple key sharing protocols |
| Device Resource Usage | Higher CPU and memory due to asymmetric cryptography | Lower resource consumption, suitable for constrained devices |
| Use Case | Large, heterogeneous IoT deployments needing strong security | Small-scale or resource-constrained IoT environments |
Understanding PKI and PSK in IoT Environments
Public Key Infrastructure (PKI) in IoT environments provides robust security by using asymmetric encryption, enabling devices to authenticate each other with unique digital certificates. In contrast, Pre-Shared Key (PSK) relies on symmetric encryption, where devices share a common secret key, simplifying deployment but increasing vulnerability risks if the key is compromised. PKI offers enhanced scalability and dynamic key management, essential for large IoT networks, while PSK is suited for smaller, resource-constrained IoT devices with limited computational power.
Key Differences Between PKI and PSK for IoT Security
Public Key Infrastructure (PKI) uses asymmetric cryptography with a pair of public and private keys, enabling scalable and secure key management for IoT devices, while Pre-Shared Key (PSK) relies on a single symmetric key shared between devices, limiting scalability and increasing vulnerability to key compromise. PKI supports dynamic certificate-based authentication, allowing automated and flexible device onboarding in large-scale IoT networks, whereas PSK requires manual key distribution, making it less suitable for extensive, heterogeneous IoT environments. The enhanced security, non-repudiation, and easier key revocation in PKI provide a robust framework for protecting sensitive IoT communications compared to the simpler but more vulnerable PSK approach.
Scalability: PKI vs PSK in Large IoT Networks
Public Key Infrastructure (PKI) offers superior scalability in large IoT networks by enabling secure, automated key management and device authentication across millions of endpoints. Pre-Shared Key (PSK) systems struggle with scalability due to the complexity of manually distributing and updating unique keys for each device, increasing the risk of security breaches. PKI's hierarchical trust model supports dynamic device onboarding and efficient cryptographic operations, making it the preferred choice for expansive IoT deployments.
Device Authentication: Enhancing Trust with PKI and PSK
Device authentication in Internet of Things (IoT) environments relies heavily on robust security mechanisms such as Public Key Infrastructure (PKI) and Pre-Shared Key (PSK) systems. PKI enhances trust through asymmetric cryptography, enabling scalable and secure identification with unique digital certificates for each device, while PSK uses symmetric keys that are simpler but less scalable and more vulnerable to key compromise. Implementing PKI in IoT networks significantly reduces the risk of unauthorized access by providing dynamic key management and non-repudiation, which are critical for maintaining device integrity and secure communication.
Key Management Challenges in IoT: PKI Compared to PSK
Key management challenges in IoT highlight the scalability and security advantages of Public Key Infrastructure (PKI) over Pre-Shared Key (PSK) systems. PKI facilitates dynamic key distribution and automated certificate management, significantly reducing risks associated with key compromise and manual key provisioning inherent in PSK. The decentralized nature of IoT devices demands PKI's robust trust model and lifecycle management to handle millions of unique identities securely, whereas PSK struggles with scalability and vulnerability to key exhaustion attacks.
Security Risks: PSK Limitations vs PKI Strengths
Pre-Shared Key (PSK) systems carry significant security risks due to key exposure and distribution challenges, making them vulnerable to unauthorized access and replay attacks in IoT networks. Public Key Infrastructure (PKI) offers robust security through asymmetric encryption and scalable key management, enabling secure device authentication and data integrity even in large-scale IoT deployments. PKI's strengths reduce risks associated with key compromise and support dynamic, automated trust establishment among IoT devices, surpassing the inherent limitations of PSK.
Performance Impact of PKI and PSK in IoT Devices
Public Key Infrastructure (PKI) in IoT devices offers robust security through asymmetric cryptography but imposes significant computational overhead, leading to increased latency and higher energy consumption. Pre-Shared Key (PSK) methods provide faster authentication with lower processing demands, making them more suitable for resource-constrained IoT devices. However, PSK's scalability and key management issues can limit its effectiveness in large, dynamic IoT ecosystems.
Cost Considerations: Implementing PKI vs PSK in IoT
Implementing Public Key Infrastructure (PKI) in IoT typically incurs higher initial costs due to the need for certificate authorities, key management systems, and computational resources for encryption and decryption processes. Pre-Shared Key (PSK) systems offer lower upfront expenses by utilizing simpler symmetric key algorithms, but scalability issues and potential security risks may lead to increased long-term costs. Budget allocation for IoT security must weigh PKI's robust scalability and automated key distribution against PSK's limited flexibility and potential vulnerabilities.
Real-World Use Cases: PKI and PSK in IoT Applications
In IoT applications, Public Key Infrastructure (PKI) is widely used for high-security environments such as smart grids and industrial automation, where scalable and robust authentication is critical to protect sensitive data. Pre-Shared Key (PSK) is often preferred in simpler, resource-constrained devices like home automation and consumer wearables due to its low computational overhead and ease of implementation. Real-world deployments demonstrate PKI's superiority in managing large device networks with dynamic access control, while PSK remains effective for smaller, static networks with minimal security requirements.
Future Trends: Evolving IoT Security Beyond PKI and PSK
Emerging IoT security trends emphasize decentralized authentication methods such as blockchain-based identity management and quantum-resistant cryptographic algorithms to overcome the limitations of traditional Public Key Infrastructure (PKI) and Pre-Shared Key (PSK) systems. Machine learning-driven anomaly detection enhances real-time threat mitigation by adapting to evolving attack patterns beyond static key-based mechanisms. Integration of hardware-based root of trust components facilitates tamper-resistant authentication, paving the way for scalable and resilient IoT ecosystems beyond conventional PKI and PSK frameworks.
Public Key Infrastructure (PKI) vs Pre-Shared Key (PSK) Infographic
 techiny.com
techiny.com