Symmetric key encryption uses a single shared secret key for both encryption and decryption, offering faster processing ideal for real-time IoT applications with resource constraints. Asymmetric key encryption employs a pair of public and private keys, enhancing security by eliminating the need to share secret keys but demanding more computational power. Selecting between symmetric and asymmetric encryption depends on balancing IoT device capabilities, communication speed requirements, and the level of security needed.
Table of Comparison
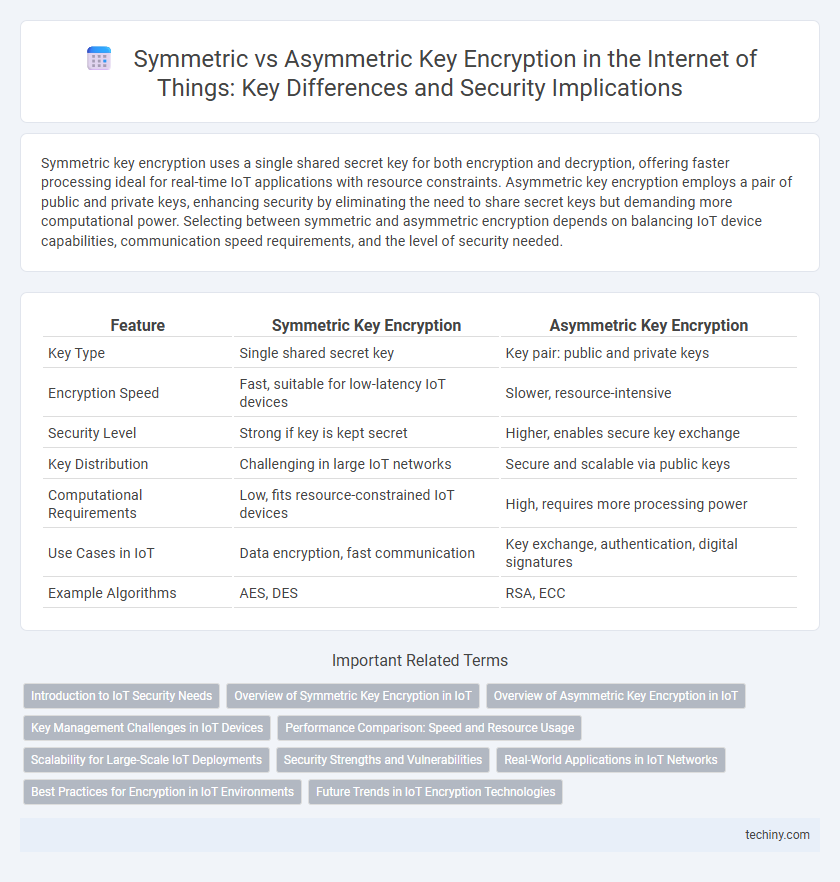
| Feature | Symmetric Key Encryption | Asymmetric Key Encryption |
|---|---|---|
| Key Type | Single shared secret key | Key pair: public and private keys |
| Encryption Speed | Fast, suitable for low-latency IoT devices | Slower, resource-intensive |
| Security Level | Strong if key is kept secret | Higher, enables secure key exchange |
| Key Distribution | Challenging in large IoT networks | Secure and scalable via public keys |
| Computational Requirements | Low, fits resource-constrained IoT devices | High, requires more processing power |
| Use Cases in IoT | Data encryption, fast communication | Key exchange, authentication, digital signatures |
| Example Algorithms | AES, DES | RSA, ECC |
Introduction to IoT Security Needs
Symmetric key encryption uses a single shared key for both encryption and decryption, offering faster processing suitable for resource-constrained IoT devices but posing risks in secure key distribution. Asymmetric key encryption employs paired public and private keys, enhancing security in IoT communications by facilitating secure key exchange and authentication despite higher computational demands. Effective IoT security strategies balance these encryption methods to protect data integrity, confidentiality, and device authentication within diverse and resource-limited IoT networks.
Overview of Symmetric Key Encryption in IoT
Symmetric key encryption in IoT uses a single secret key for both encryption and decryption, providing fast and efficient data protection ideal for resource-constrained devices. This method enhances real-time communication security by minimizing computational overhead, which is critical for battery-powered sensors and low-power networks. However, key distribution and management present challenges in large-scale IoT deployments, necessitating robust protocols to maintain secure and scalable environments.
Overview of Asymmetric Key Encryption in IoT
Asymmetric key encryption in IoT utilizes a pair of mathematically linked keys--public and private--to secure data transmission and device authentication without sharing secret keys, enhancing scalability and security in decentralized networks. This method supports key distribution and management challenges inherent to IoT ecosystems with numerous interconnected devices. Asymmetric encryption algorithms such as RSA and ECC are widely adopted for their ability to provide robust confidentiality and integrity while enabling secure communication across resource-constrained IoT devices.
Key Management Challenges in IoT Devices
Symmetric key encryption in IoT devices demands secure key distribution and storage, posing risks due to limited device resources and scalability requirements. Asymmetric key encryption offers improved key management through public-private key pairs, but introduces computational overhead that can strain constrained IoT devices. Efficient key management solutions must balance security, resource limitations, and scalability to ensure robust protection of sensitive IoT data.
Performance Comparison: Speed and Resource Usage
Symmetric key encryption in Internet of Things (IoT) devices offers faster data processing and lower computational overhead compared to asymmetric key encryption, making it ideal for resource-constrained environments. Asymmetric encryption demands significantly more CPU cycles and memory, resulting in slower performance and increased energy consumption, which can hinder real-time IoT applications. Consequently, symmetric encryption's efficiency in speed and resource usage makes it the preferred choice for secure communication in IoT networks with limited hardware capabilities.
Scalability for Large-Scale IoT Deployments
Symmetric key encryption offers high-speed processing suitable for large-scale IoT deployments but faces challenges in scalability due to complex key management and distribution across numerous devices. Asymmetric key encryption simplifies key distribution by using public and private key pairs, enhancing scalability for extensive IoT networks despite higher computational overhead. Efficiently balancing these encryption methods is critical for ensuring secure and scalable IoT ecosystems with millions of connected devices.
Security Strengths and Vulnerabilities
Symmetric key encryption offers faster processing and lower computational overhead, making it suitable for resource-constrained IoT devices but poses challenges in secure key distribution and management. Asymmetric key encryption enhances security through public-private key pairs, enabling secure key exchange and authentication, yet it requires higher computational power and increased latency. IoT environments benefit from a hybrid approach that leverages the efficiency of symmetric encryption for data transmission and the robust key management capabilities of asymmetric encryption to mitigate vulnerabilities.
Real-World Applications in IoT Networks
Symmetric key encryption, widely used in IoT networks, offers fast and efficient data protection suitable for resource-constrained devices such as sensors and smart home appliances. Asymmetric key encryption, essential for secure device authentication and key exchange, supports complex IoT ecosystems like industrial automation and smart city infrastructure by enabling secure communication between heterogeneous devices. Combining both methods enhances overall IoT security by leveraging symmetric encryption for bulk data transmission and asymmetric encryption for initial key distribution and identity verification.
Best Practices for Encryption in IoT Environments
Symmetric key encryption in IoT environments offers faster processing and lower resource consumption, making it ideal for devices with limited computational power. Asymmetric key encryption provides stronger security through public-private key pairs but requires more processing power, suitable for secure key exchange and authentication. Best practices recommend combining both methods: using asymmetric encryption for initial key exchange and symmetric encryption for ongoing data transmission to balance security and efficiency.
Future Trends in IoT Encryption Technologies
Future trends in IoT encryption technologies emphasize the integration of lightweight symmetric key algorithms to address resource constraints in connected devices, while advancing post-quantum asymmetric cryptographic methods to enhance security against emerging cyber threats. Hybrid encryption models combining symmetric speed and asymmetric security are gaining traction to optimize performance and robustness in large-scale IoT ecosystems. Research in blockchain-based key management systems further supports scalable and decentralized encryption frameworks critical for the expanding Internet of Things landscape.
Symmetric Key Encryption vs Asymmetric Key Encryption Infographic
 techiny.com
techiny.com