Bluejacking involves sending unsolicited messages over Bluetooth to nearby devices, primarily as a harmless prank or communication method, without accessing any data. Bluesnarfing is a malicious attack where hackers exploit Bluetooth connections to steal information such as contacts, messages, and files from a victim's device. Protecting Bluetooth connections with strong authentication and disabling discoverable mode reduces the risk of both bluejacking and bluesnarfing attacks.
Table of Comparison
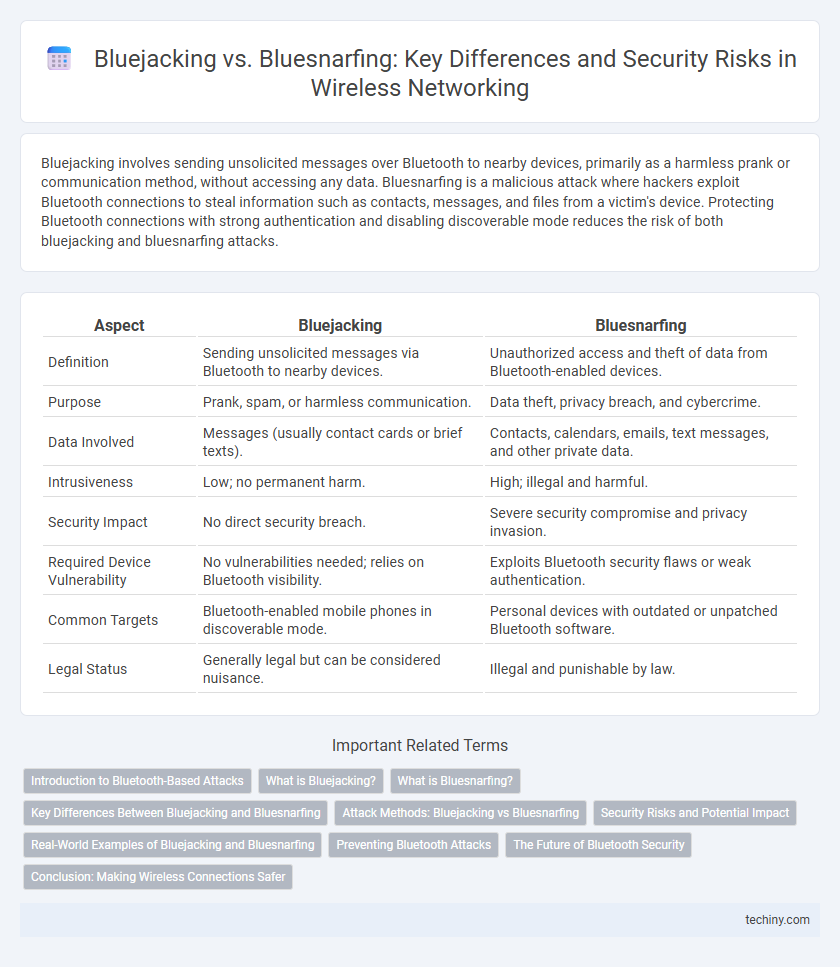
| Aspect | Bluejacking | Bluesnarfing |
|---|---|---|
| Definition | Sending unsolicited messages via Bluetooth to nearby devices. | Unauthorized access and theft of data from Bluetooth-enabled devices. |
| Purpose | Prank, spam, or harmless communication. | Data theft, privacy breach, and cybercrime. |
| Data Involved | Messages (usually contact cards or brief texts). | Contacts, calendars, emails, text messages, and other private data. |
| Intrusiveness | Low; no permanent harm. | High; illegal and harmful. |
| Security Impact | No direct security breach. | Severe security compromise and privacy invasion. |
| Required Device Vulnerability | No vulnerabilities needed; relies on Bluetooth visibility. | Exploits Bluetooth security flaws or weak authentication. |
| Common Targets | Bluetooth-enabled mobile phones in discoverable mode. | Personal devices with outdated or unpatched Bluetooth software. |
| Legal Status | Generally legal but can be considered nuisance. | Illegal and punishable by law. |
Introduction to Bluetooth-Based Attacks
Bluejacking involves sending unsolicited messages to nearby Bluetooth devices, leveraging the device's discoverable mode without requiring authentication, primarily causing nuisance rather than direct harm. Bluesnarfing exploits vulnerabilities in Bluetooth protocols to access and steal private data such as contacts, messages, and files without the user's consent, posing significant security risks. Both attacks highlight the importance of securing Bluetooth connections by disabling discoverable mode and using strong encryption protocols.
What is Bluejacking?
Bluejacking is a Bluetooth-based communication technique that allows users to send anonymous and unsolicited messages to nearby Bluetooth-enabled devices within a limited range, typically up to 10 meters. It exploits the Bluetooth protocol's capability to exchange contact information by sending vCards or short text messages without pairing devices. Unlike Bluesnarfing, Bluejacking does not attempt to access or steal data but serves as a harmless prank or marketing tool by initiating brief, unexpected message exchanges.
What is Bluesnarfing?
Bluesnarfing is an unauthorized Bluetooth attack that allows hackers to access and steal information from a victim's device without their knowledge. It exploits vulnerabilities in Bluetooth connections to gain access to contacts, messages, calendars, and other sensitive data. Unlike Bluejacking, which involves sending unsolicited messages, Bluesnarfing targets data theft and device exploitation.
Key Differences Between Bluejacking and Bluesnarfing
Bluejacking involves sending unsolicited messages to Bluetooth-enabled devices, primarily for harmless communication or pranks, while Bluesnarfing targets unauthorized access to private data stored on these devices, such as contacts and messages. Unlike Bluejacking, which does not compromise device security or data integrity, Bluesnarfing exploits vulnerabilities to extract sensitive information without user consent. The key difference lies in Bluejacking being a benign act of message transmission versus Bluesnarfing representing a serious security breach and privacy threat.
Attack Methods: Bluejacking vs Bluesnarfing
Bluejacking involves sending unsolicited messages over Bluetooth to nearby devices without gaining access to their data, primarily exploiting Bluetooth's contact sharing feature. Bluesnarfing is a more invasive attack method where the attacker exploits Bluetooth vulnerabilities to access or steal sensitive information such as contacts, messages, or files from the targeted device. Unlike Bluejacking, Bluesnarfing uses unauthorized data extraction techniques that compromise device security and privacy.
Security Risks and Potential Impact
Bluejacking involves sending unsolicited messages via Bluetooth to nearby devices, posing minimal security risks but potentially causing annoyance or social engineering exploits. Bluesnarfing represents a serious security threat by enabling unauthorized access to sensitive data such as contacts, messages, and files on a Bluetooth-enabled device. The potential impact of bluesnarfing includes data theft, privacy breaches, and compromised personal or corporate information integrity.
Real-World Examples of Bluejacking and Bluesnarfing
Bluejacking involves sending unsolicited messages via Bluetooth to nearby devices, commonly seen at conferences where marketers promote products through brief pop-up ads on attendees' phones. Bluesnarfing, a more malicious attack, targets vulnerabilities in Bluetooth-enabled devices to steal sensitive data such as contacts, messages, and calendars, with notable incidents including the 2005 Bluetooth exploit targeting early Nokia and Sony Ericsson phones. Real-world cases highlight bluejacking's use for harmless social interactions, whereas bluesnarfing poses serious security threats requiring robust device protection.
Preventing Bluetooth Attacks
Preventing Bluetooth attacks like Bluejacking and Bluesnarfing requires disabling Bluetooth visibility when not in use and using strong pairing codes. Regular firmware updates and avoiding connections from unknown devices minimize the risk of unauthorized data access and unsolicited messages. Implementing Bluetooth security protocols such as Secure Simple Pairing (SSP) enhances protection against these common vulnerabilities.
The Future of Bluetooth Security
The future of Bluetooth security involves advanced encryption protocols and real-time threat detection to combat vulnerabilities exploited by bluejacking and bluesnarfing attacks. Emerging technologies like AI-driven anomaly detection and quantum-resistant algorithms are expected to enhance protection against unauthorized data access and message spoofing. Continuous updates to Bluetooth standards will focus on minimizing attack surfaces and improving device authentication processes to ensure safer wireless communication.
Conclusion: Making Wireless Connections Safer
Bluejacking involves sending unsolicited messages over Bluetooth to nearby devices, posing minimal security risk, while Bluesnarfing entails unauthorized access to information stored on a device, representing a significant privacy threat. Implementing strong Bluetooth security settings, such as device visibility controls and requiring authentication for pairing, mitigates vulnerabilities effectively. Regular software updates and user awareness are critical components in protecting wireless connections against Bluejacking and Bluesnarfing attacks.
Bluejacking vs Bluesnarfing Infographic
 techiny.com
techiny.com