Quantum cryptography leverages principles of quantum mechanics, such as superposition and entanglement, to enable ultra-secure communication that is theoretically immune to eavesdropping. Classical cryptography relies on mathematical algorithms and computational hardness assumptions, making it vulnerable to attacks from powerful quantum computers in the future. The inherent uncertainty and measurement disturbance in quantum systems provide an unbreakable security layer that classical methods cannot achieve.
Table of Comparison
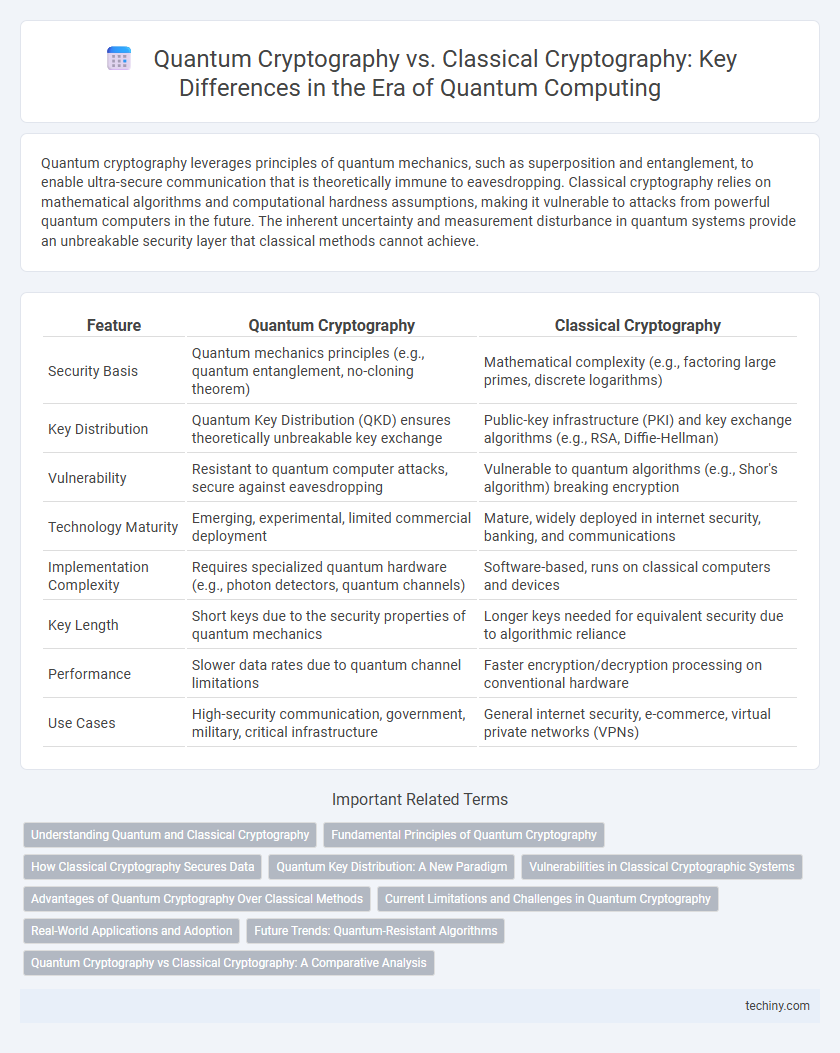
| Feature | Quantum Cryptography | Classical Cryptography |
|---|---|---|
| Security Basis | Quantum mechanics principles (e.g., quantum entanglement, no-cloning theorem) | Mathematical complexity (e.g., factoring large primes, discrete logarithms) |
| Key Distribution | Quantum Key Distribution (QKD) ensures theoretically unbreakable key exchange | Public-key infrastructure (PKI) and key exchange algorithms (e.g., RSA, Diffie-Hellman) |
| Vulnerability | Resistant to quantum computer attacks, secure against eavesdropping | Vulnerable to quantum algorithms (e.g., Shor's algorithm) breaking encryption |
| Technology Maturity | Emerging, experimental, limited commercial deployment | Mature, widely deployed in internet security, banking, and communications |
| Implementation Complexity | Requires specialized quantum hardware (e.g., photon detectors, quantum channels) | Software-based, runs on classical computers and devices |
| Key Length | Short keys due to the security properties of quantum mechanics | Longer keys needed for equivalent security due to algorithmic reliance |
| Performance | Slower data rates due to quantum channel limitations | Faster encryption/decryption processing on conventional hardware |
| Use Cases | High-security communication, government, military, critical infrastructure | General internet security, e-commerce, virtual private networks (VPNs) |
Understanding Quantum and Classical Cryptography
Quantum cryptography leverages principles of quantum mechanics, such as superposition and entanglement, to create secure communication channels that are theoretically immune to eavesdropping. Classical cryptography relies on complex mathematical algorithms like RSA and AES, whose security depends on computational difficulty and key secrecy. Understanding the distinct foundations of these approaches highlights quantum cryptography's potential to revolutionize data security by offering theoretically unbreakable encryption methods.
Fundamental Principles of Quantum Cryptography
Quantum cryptography leverages principles like superposition and quantum entanglement to enable practically unbreakable encryption, fundamentally differing from classical cryptography's reliance on complex mathematical algorithms. The core technique, Quantum Key Distribution (QKD), uses quantum states to detect eavesdropping, ensuring absolute security through the no-cloning theorem and measurement disturbance. Classical cryptography depends on computational hardness assumptions, while quantum cryptography guarantees security grounded in the laws of quantum mechanics.
How Classical Cryptography Secures Data
Classical cryptography secures data through complex mathematical algorithms such as RSA and AES, which rely on computational hardness assumptions like integer factorization and discrete logarithms. It uses symmetric and asymmetric key techniques to encrypt and decrypt information, ensuring confidentiality, integrity, and authenticity in digital communications. The security of classical cryptography depends on the difficulty of solving these mathematical problems within feasible time by current computational technologies.
Quantum Key Distribution: A New Paradigm
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics to enable secure encryption key exchange, providing theoretically unbreakable security unlike classical cryptography which relies on computational complexity. QKD uses quantum states of particles, such as photons, to detect any eavesdropping, ensuring the integrity and confidentiality of the key. This new paradigm in cryptography fundamentally enhances data protection by exploiting quantum phenomena, rendering traditional hacking techniques ineffective.
Vulnerabilities in Classical Cryptographic Systems
Classical cryptographic systems rely on mathematical complexity, making them vulnerable to advances in computational power and algorithmic breakthroughs, such as those seen with quantum algorithms like Shor's algorithm. These vulnerabilities expose encrypted data to potential decryption by quantum computers, threatening the security of widely-used protocols like RSA and ECC. Quantum cryptography leverages principles of quantum mechanics, such as quantum key distribution (QKD), to provide theoretically unbreakable encryption resistant to computational attacks.
Advantages of Quantum Cryptography Over Classical Methods
Quantum cryptography leverages principles of quantum mechanics, such as superposition and entanglement, to provide theoretically unbreakable encryption through quantum key distribution (QKD). Unlike classical cryptography, which relies on computational hardness assumptions vulnerable to advances in algorithms and quantum computing attacks, quantum cryptography ensures security guaranteed by the laws of physics. This inherent security advantage makes quantum cryptography resistant to eavesdropping and future-proof against the threats posed by quantum computers, enabling unprecedented data protection.
Current Limitations and Challenges in Quantum Cryptography
Quantum cryptography faces significant challenges such as the need for highly specialized hardware like quantum key distribution (QKD) devices, which remain expensive and difficult to integrate into existing communication infrastructure. Its practical implementation is hindered by quantum decoherence and photon loss, limiting transmission distances and key generation rates. Despite its promise for theoretically unbreakable security, quantum cryptography currently lacks scalability and standardization compared to classical cryptographic methods.
Real-World Applications and Adoption
Quantum cryptography leverages the principles of quantum mechanics to provide theoretically unbreakable encryption, making it highly suitable for securing critical government communications and financial transactions. Classical cryptography remains widely adopted due to its established infrastructure and compatibility with current digital systems, used extensively in everyday internet security and mobile communications. Industries such as banking and defense are increasingly investing in quantum key distribution (QKD) technologies to future-proof their security against quantum computing threats.
Future Trends: Quantum-Resistant Algorithms
Quantum-resistant algorithms are being developed to secure data against potential quantum computer attacks that can break classical cryptography. Post-quantum cryptography focuses on lattice-based, hash-based, and code-based algorithms, designed to withstand quantum decryption techniques. These advancements will drive the future of secure communications by integrating with existing cryptographic systems to protect sensitive information in the quantum era.
Quantum Cryptography vs Classical Cryptography: A Comparative Analysis
Quantum cryptography leverages principles of quantum mechanics, such as superposition and entanglement, to enable theoretically unbreakable encryption through quantum key distribution (QKD). Classical cryptography relies on mathematical algorithms and computational hardness assumptions, which are vulnerable to attacks by quantum computers capable of solving problems like integer factorization efficiently. The comparative analysis highlights quantum cryptography's potential for enhanced security in the face of emerging quantum threats, while classical cryptography remains widely adopted due to its established infrastructure and efficiency.
Quantum Cryptography vs Classical Cryptography Infographic
 techiny.com
techiny.com