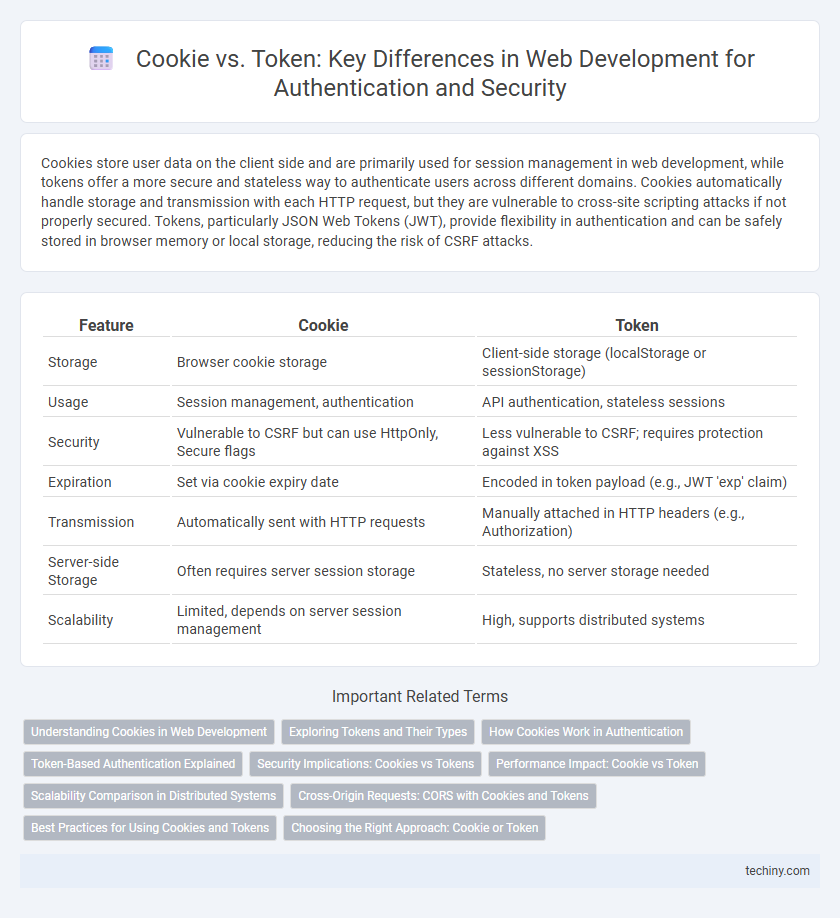
Cookies store user data on the client side and are primarily used for session management in web development, while tokens offer a more secure and stateless way to authenticate users across different domains. Cookies automatically handle storage and transmission with each HTTP request, but they are vulnerable to cross-site scripting attacks if not properly secured. Tokens, particularly JSON Web Tokens (JWT), provide flexibility in authentication and can be safely stored in browser memory or local storage, reducing the risk of CSRF attacks.
Table of Comparison
| Feature | Cookie | Token |
|---|---|---|
| Storage | Browser cookie storage | Client-side storage (localStorage or sessionStorage) |
| Usage | Session management, authentication | API authentication, stateless sessions |
| Security | Vulnerable to CSRF but can use HttpOnly, Secure flags | Less vulnerable to CSRF; requires protection against XSS |
| Expiration | Set via cookie expiry date | Encoded in token payload (e.g., JWT 'exp' claim) |
| Transmission | Automatically sent with HTTP requests | Manually attached in HTTP headers (e.g., Authorization) |
| Server-side Storage | Often requires server session storage | Stateless, no server storage needed |
| Scalability | Limited, depends on server session management | High, supports distributed systems |
Understanding Cookies in Web Development
Cookies in web development are small pieces of data stored on the client's browser, primarily used for session management, personalization, and tracking user activity. They enable servers to recognize returning users and maintain stateful interactions across multiple requests, essential for login persistence and user preferences. Security concerns include susceptibility to cross-site scripting (XSS) and cross-site request forgery (CSRF) attacks, making HttpOnly and Secure flags crucial for safeguarding cookie data.
Exploring Tokens and Their Types
Tokens serve as secure, stateless authentication credentials in web development, enabling seamless user verification across distributed systems. Common token types include JWT (JSON Web Token), which encodes claims in a compact, URL-safe format, and OAuth tokens, used for delegated access authorization. These tokens improve scalability and security by minimizing server-side session storage and supporting granular access control.
How Cookies Work in Authentication
Cookies store authentication data directly in the user's browser, sending this information with each HTTP request to maintain session state and verify user identity. They enable persistent login sessions by securely holding session identifiers or tokens that the server validates. This mechanism helps web applications manage user access without repeatedly prompting for credentials.
Token-Based Authentication Explained
Token-based authentication enhances web development security by issuing a digitally signed token after user login, enabling stateless, scalable sessions without storing credentials on the server. JSON Web Tokens (JWT) serve as a popular format, encapsulating user data and expiration times for secure, efficient verification across API requests. This method reduces vulnerabilities like cross-site request forgery and simplifies mobile app integration compared to traditional cookie-based authentication.
Security Implications: Cookies vs Tokens
Cookies store session data directly on the client side and are vulnerable to cross-site scripting (XSS) and cross-site request forgery (CSRF) attacks if not properly secured with HttpOnly and SameSite flags. Tokens, such as JSON Web Tokens (JWTs), are stateless and stored in browser storage or transmitted via headers, reducing CSRF risks but increasing exposure to XSS if localStorage is used. Implementing secure token storage and employing short token lifetimes with refresh mechanisms enhances security compared to traditional cookie-based sessions.
Performance Impact: Cookie vs Token
Cookies can introduce latency as they are automatically sent with each HTTP request, increasing the request size and potentially slowing down web page loading times. Tokens, especially JSON Web Tokens (JWT), optimize performance by being stored client-side and included only in API calls, reducing unnecessary data transmission. This selective inclusion helps improve server response times and overall application efficiency.
Scalability Comparison in Distributed Systems
Tokens offer superior scalability in distributed systems by enabling stateless authentication, reducing server-side storage and synchronization overhead compared to cookies that require centralized session management. Cookies rely on maintaining session state on the server, which can become a bottleneck as the number of users grows, whereas tokens, especially JWTs, contain user information within themselves and facilitate horizontal scaling. This stateless nature of tokens simplifies load balancing and improves performance in microservices architectures, making them more suitable for large-scale web applications.
Cross-Origin Requests: CORS with Cookies and Tokens
Cross-Origin Resource Sharing (CORS) policies impact how cookies and tokens manage authentication in web development. Cookies rely on browser-managed headers and require proper SameSite and Secure attributes to be sent with cross-origin requests, often necessitating server configurations for credentials support. Tokens, typically included in Authorization headers, bypass some CORS cookie restrictions by being explicitly appended to requests, offering more flexibility in cross-origin API authentication.
Best Practices for Using Cookies and Tokens
For secure web development, use HttpOnly and Secure flags when setting cookies to prevent XSS and ensure data transmission over HTTPS. Implement token-based authentication with short-lived JWTs stored in memory to minimize exposure to CSRF and XSS attacks. Regularly rotate tokens and enforce SameSite cookie attributes to enhance security and maintain user session integrity.
Choosing the Right Approach: Cookie or Token
Selecting between cookies and tokens for web development hinges on security needs and application architecture. Cookies, managed by browsers, excel in handling session-based authentication and are vulnerable to Cross-Site Scripting (XSS) but can be protected with HTTPOnly and Secure flags. Tokens, such as JSON Web Tokens (JWT), are stateless, suitable for RESTful APIs, and offer scalability, with enhanced control over authentication and authorization across distributed systems.
Cookie vs Token Infographic
 techiny.com
techiny.com