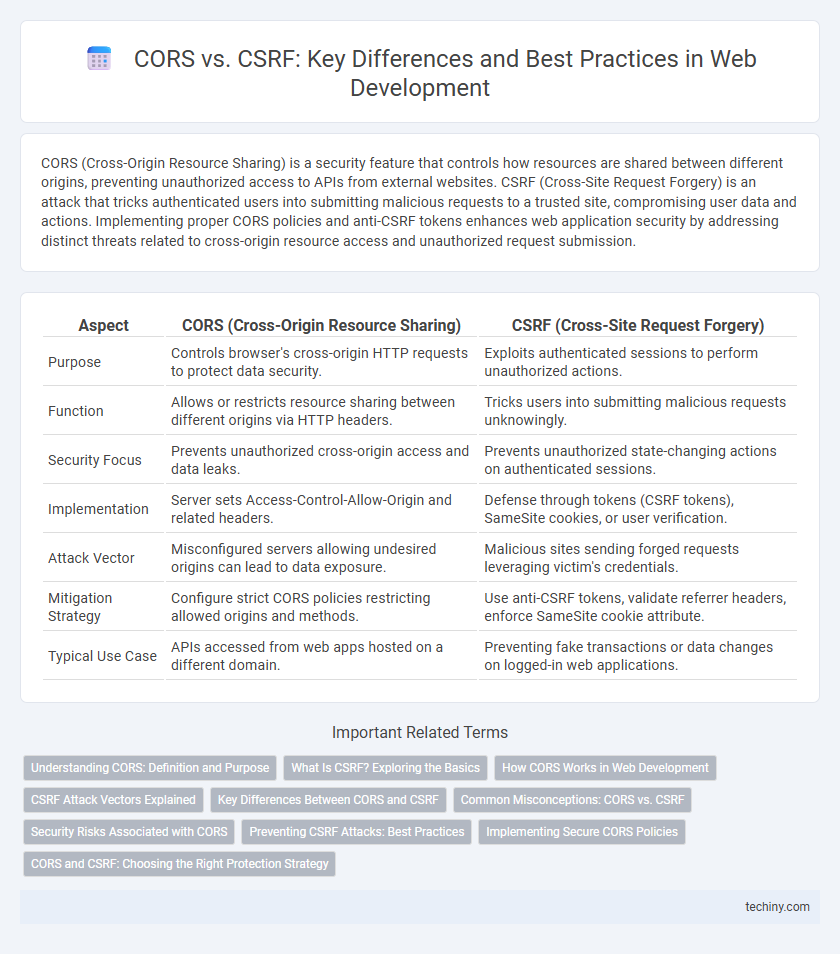
CORS (Cross-Origin Resource Sharing) is a security feature that controls how resources are shared between different origins, preventing unauthorized access to APIs from external websites. CSRF (Cross-Site Request Forgery) is an attack that tricks authenticated users into submitting malicious requests to a trusted site, compromising user data and actions. Implementing proper CORS policies and anti-CSRF tokens enhances web application security by addressing distinct threats related to cross-origin resource access and unauthorized request submission.
Table of Comparison
| Aspect | CORS (Cross-Origin Resource Sharing) | CSRF (Cross-Site Request Forgery) |
|---|---|---|
| Purpose | Controls browser's cross-origin HTTP requests to protect data security. | Exploits authenticated sessions to perform unauthorized actions. |
| Function | Allows or restricts resource sharing between different origins via HTTP headers. | Tricks users into submitting malicious requests unknowingly. |
| Security Focus | Prevents unauthorized cross-origin access and data leaks. | Prevents unauthorized state-changing actions on authenticated sessions. |
| Implementation | Server sets Access-Control-Allow-Origin and related headers. | Defense through tokens (CSRF tokens), SameSite cookies, or user verification. |
| Attack Vector | Misconfigured servers allowing undesired origins can lead to data exposure. | Malicious sites sending forged requests leveraging victim's credentials. |
| Mitigation Strategy | Configure strict CORS policies restricting allowed origins and methods. | Use anti-CSRF tokens, validate referrer headers, enforce SameSite cookie attribute. |
| Typical Use Case | APIs accessed from web apps hosted on a different domain. | Preventing fake transactions or data changes on logged-in web applications. |
Understanding CORS: Definition and Purpose
Cross-Origin Resource Sharing (CORS) is a security feature implemented by web browsers that allows controlled access to resources located outside the domain from which a web page is served. It helps prevent malicious web applications from requesting unauthorized data by enforcing server-defined policies through HTTP headers like Access-Control-Allow-Origin. Understanding CORS is essential for developers to enable secure cross-domain communication while protecting user data from cross-site attacks.
What Is CSRF? Exploring the Basics
CSRF (Cross-Site Request Forgery) is a security vulnerability where an attacker tricks a user into executing unwanted actions on a web application in which they are authenticated. This exploit relies on the victim's browser sending trusted credentials automatically, such as cookies or session tokens, making unauthorized requests appear legitimate. Preventing CSRF attacks involves implementing anti-CSRF tokens, same-site cookies, and validating the origin of incoming requests in web applications.
How CORS Works in Web Development
CORS (Cross-Origin Resource Sharing) works by allowing web servers to specify trusted origins through HTTP headers like Access-Control-Allow-Origin, enabling secure cross-domain resource sharing. Browsers enforce these policies by sending preflight OPTIONS requests to verify permitted methods and headers before making actual requests, ensuring that unauthorized domains cannot access sensitive resources. This mechanism helps prevent security vulnerabilities by restricting web page scripts on one origin from interacting with resources from a different origin without explicit permission.
CSRF Attack Vectors Explained
CSRF attack vectors exploit the trust a web application has in a user's browser by forging unauthorized requests on their behalf, often leveraging stored credentials or session cookies without user consent. Attackers commonly use techniques such as hidden forms, malicious links, or scripted requests embedded in third-party sites to trigger state-changing operations on vulnerable web applications. Effective mitigation includes implementing anti-CSRF tokens, same-site cookies, and strict origin checking to prevent unauthorized request execution.
Key Differences Between CORS and CSRF
CORS (Cross-Origin Resource Sharing) is a security feature implemented by browsers to control how resources from one origin can be requested by another origin, primarily protecting users from unauthorized cross-origin requests. CSRF (Cross-Site Request Forgery) is an attack that tricks a user's browser into making unwanted requests to a different site where the user is authenticated, exploiting trust between the browser and the target site. The key difference lies in their purpose: CORS manages cross-origin communication policies, while CSRF targets the exploitation of authenticated sessions to perform malicious actions without user consent.
Common Misconceptions: CORS vs. CSRF
CORS (Cross-Origin Resource Sharing) is often misunderstood as a security feature to prevent CSRF (Cross-Site Request Forgery) attacks, but it primarily controls browser-based access to resources across different origins rather than preventing unauthorized actions. CSRF exploits the trust a website has in a user's browser by tricking it into sending unwanted requests, which requires specific protections like anti-CSRF tokens or SameSite cookies. Confusing CORS policies with CSRF protections can lead to incomplete security implementations and expose web applications to forgery vulnerabilities.
Security Risks Associated with CORS
Cross-Origin Resource Sharing (CORS) introduces security risks by potentially allowing malicious websites to access sensitive resources on another domain if improperly configured. Misconfigured CORS policies can enable attackers to bypass same-origin policy restrictions, leading to data theft or unauthorized actions. Strict validation of origins, methods, and headers is essential to mitigate vulnerabilities and protect web applications from cross-origin attacks.
Preventing CSRF Attacks: Best Practices
Preventing CSRF attacks involves implementing anti-CSRF tokens, which are unique, unpredictable values included in HTTP requests to verify user legitimacy. Configuring SameSite cookie attributes restricts cookies from being sent with cross-site requests, reducing the risk of unauthorized actions. Employing user authentication mechanisms such as multi-factor authentication (MFA) further strengthens defense against CSRF exploits in web applications.
Implementing Secure CORS Policies
Implementing secure CORS policies involves defining strict Access-Control-Allow-Origin headers to restrict resource sharing to trusted domains, preventing unauthorized cross-origin requests. Configuring appropriate Access-Control-Allow-Methods and Access-Control-Allow-Headers limits the types of requests and headers accepted, reducing potential attack vectors. Monitoring preflight request responses and avoiding wildcard origins enhances protection against cross-site request forgery (CSRF) by ensuring that only legitimate domains can interact with sensitive APIs.
CORS and CSRF: Choosing the Right Protection Strategy
CORS (Cross-Origin Resource Sharing) and CSRF (Cross-Site Request Forgery) address different security challenges in web development; CORS manages resource sharing policies across origins, preventing unauthorized cross-origin requests, while CSRF protects against malicious state-changing actions initiated from trusted users' browsers. Selecting the right protection strategy involves evaluating whether the threat stems from unauthorized data access (CORS) or forged user requests (CSRF), and implementing corresponding mechanisms such as CORS headers for access control and anti-CSRF tokens for request validation. Effective security architecture integrates both CORS policies and CSRF defenses to ensure secure, controlled interactions between clients and servers.
CORS vs CSRF Infographic
 techiny.com
techiny.com