JWT and sessions are two common methods for maintaining user authentication in web development, with JWT offering a stateless approach by storing encoded user information on the client side. Sessions rely on server-side storage to keep track of user state, often requiring database or memory management. Choosing between JWT and sessions depends on the scalability needs, security requirements, and client-server architecture of the application.
Table of Comparison
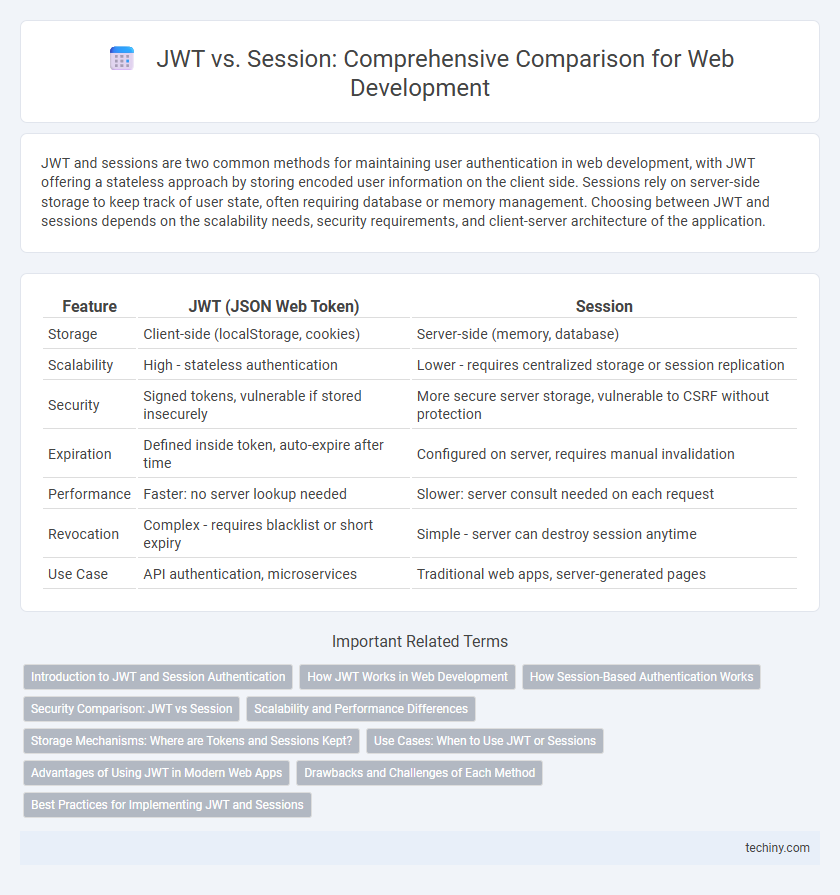
| Feature | JWT (JSON Web Token) | Session |
|---|---|---|
| Storage | Client-side (localStorage, cookies) | Server-side (memory, database) |
| Scalability | High - stateless authentication | Lower - requires centralized storage or session replication |
| Security | Signed tokens, vulnerable if stored insecurely | More secure server storage, vulnerable to CSRF without protection |
| Expiration | Defined inside token, auto-expire after time | Configured on server, requires manual invalidation |
| Performance | Faster: no server lookup needed | Slower: server consult needed on each request |
| Revocation | Complex - requires blacklist or short expiry | Simple - server can destroy session anytime |
| Use Case | API authentication, microservices | Traditional web apps, server-generated pages |
Introduction to JWT and Session Authentication
JWT (JSON Web Token) authentication uses a compact, URL-safe token that securely transmits information between parties as a JSON object, enabling stateless, scalable web applications. Session authentication stores user data on the server side, tracking active sessions with unique session IDs, which are sent to the client via cookies and verified on subsequent requests. JWT is preferred for APIs and distributed systems due to its stateless nature, while session authentication offers straightforward server-managed control ideal for traditional web applications.
How JWT Works in Web Development
JWT (JSON Web Token) works in web development by securely transmitting information between parties as a JSON object, signed with a secret or a public/private key pair to ensure data integrity and authenticity. Upon user authentication, the server generates a JWT containing user claims, which the client stores (typically in localStorage or cookies) and includes in the Authorization header of subsequent HTTP requests. This stateless authentication method enables scalable and efficient user session management without relying on server-side session storage.
How Session-Based Authentication Works
Session-based authentication works by storing user-specific data on the server after a successful login, linking it to a unique session ID sent to the client's browser as a cookie. Each subsequent request from the client includes this session ID, allowing the server to validate the user's identity and access rights by retrieving the session data. This method ensures that sensitive information is kept on the server side, reducing exposure risk compared to token-based authentication.
Security Comparison: JWT vs Session
JWT offers stateless authentication by embedding user data directly within the token, reducing server-side storage but increasing exposure to token theft and replay attacks if not properly secured with strong encryption and short expiration. In contrast, session-based authentication stores user state on the server, enabling easier invalidation and protection against token reuse, but requires robust server security and can introduce scalability challenges. Both methods require implementing HTTPS, secure cookie flags, and CSRF protection to mitigate common web vulnerabilities effectively.
Scalability and Performance Differences
JWT tokens enhance scalability by enabling stateless authentication, eliminating the need for server-side session storage and allowing seamless load balancing across distributed systems. Sessions require server memory to store user data, which can cause performance bottlenecks as user count increases, especially in clustered environments needing session replication. JWT reduces database queries for session validation, improving response times and overall application performance under high traffic conditions.
Storage Mechanisms: Where are Tokens and Sessions Kept?
JWTs are typically stored on the client side, most commonly in localStorage or cookies, allowing stateless authentication without server memory usage. Sessions are stored on the server, often in memory, databases, or cache systems like Redis, requiring server resources to maintain user state. Client-side JWT storage enables scalability, while server-side session storage offers tighter control over user data and session invalidation.
Use Cases: When to Use JWT or Sessions
JWT is ideal for stateless authentication in distributed systems and single-page applications where scalability and cross-domain support are essential. Sessions are better suited for traditional web applications requiring server-side control, immediate revocation, and secure storage of user data. Choose JWT for mobile app APIs or microservices, whereas sessions work well for applications prioritizing security and ease of server-side session management.
Advantages of Using JWT in Modern Web Apps
JWT (JSON Web Tokens) offer stateless authentication, reducing server load by eliminating the need to store session data. Their compact, URL-safe format enhances performance and scalability across distributed systems and microservices architectures. Built-in payload integrity and signature verification improve security while enabling seamless cross-domain authentication in modern web applications.
Drawbacks and Challenges of Each Method
JWTs often suffer from token size overhead and lack of straightforward invalidation mechanisms, making them vulnerable to security risks if tokens are compromised. Sessions rely on server-side storage, which can lead to scalability issues and increased memory usage under heavy traffic. Both methods face challenges in balancing security, performance, and user experience during web authentication.
Best Practices for Implementing JWT and Sessions
Secure storage of JWTs in HTTP-only cookies prevents XSS attacks, while regular token rotation enhances security and limits exposure from token theft. Sessions benefit from server-side management with properly configured expiration, secure cookies, and frequent session ID regeneration to reduce fixation risks. Combining JWT statelessness with session server validation can optimize scalability and security in distributed web applications.
JWT vs Session Infographic
 techiny.com
techiny.com