A 51% attack occurs when a single entity gains control over the majority of a blockchain network's mining power, enabling them to manipulate transaction validations and double-spend coins. In contrast, a Sybil attack involves creating numerous fake nodes to gain disproportionate influence over the network's consensus. Both threats undermine blockchain security but target network control through mining power versus node identity proliferation.
Table of Comparison
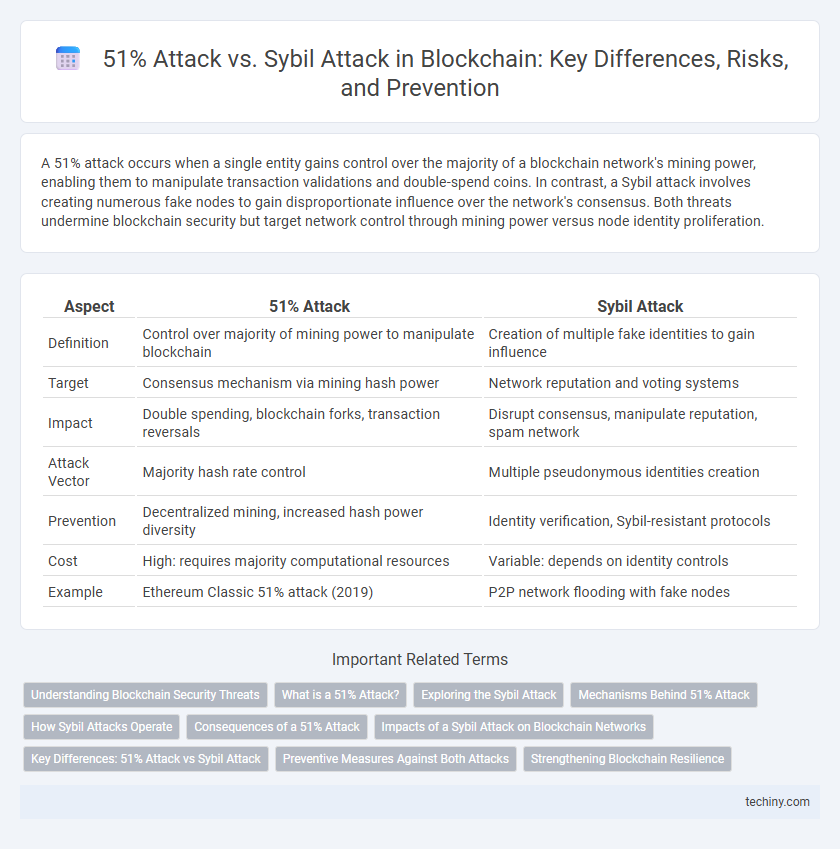
| Aspect | 51% Attack | Sybil Attack |
|---|---|---|
| Definition | Control over majority of mining power to manipulate blockchain | Creation of multiple fake identities to gain influence |
| Target | Consensus mechanism via mining hash power | Network reputation and voting systems |
| Impact | Double spending, blockchain forks, transaction reversals | Disrupt consensus, manipulate reputation, spam network |
| Attack Vector | Majority hash rate control | Multiple pseudonymous identities creation |
| Prevention | Decentralized mining, increased hash power diversity | Identity verification, Sybil-resistant protocols |
| Cost | High: requires majority computational resources | Variable: depends on identity controls |
| Example | Ethereum Classic 51% attack (2019) | P2P network flooding with fake nodes |
Understanding Blockchain Security Threats
A 51% attack occurs when a single entity controls over half of a blockchain network's mining power, enabling manipulation of transaction history and double-spending. Sybil attacks involve creating multiple fake identities to gain disproportionate influence on the network, undermining consensus mechanisms and trust. Understanding these threats highlights the importance of decentralized network design and robust consensus protocols in maintaining blockchain security.
What is a 51% Attack?
A 51% attack occurs when a single miner or group controls over half of a blockchain network's mining hash rate, enabling them to manipulate transaction verification and potentially reverse transactions or double-spend coins. This control breaks the decentralized consensus by overpowering honest miners, undermining network security and trust. Unlike Sybil attacks that flood the network with fake identities, a 51% attack relies on computational dominance to alter the blockchain ledger.
Exploring the Sybil Attack
A Sybil attack in blockchain exploits the creation of numerous fake identities to gain disproportionate influence over the network, undermining its decentralization and trust mechanisms. Unlike the 51% attack, which requires controlling a majority of the mining power to manipulate transactions, a Sybil attack targets the network's peer-to-peer structure by flooding it with dishonest nodes. This form of attack threatens consensus protocols by enabling malicious actors to disrupt voting systems, delay transactions, and partition the network, severely compromising blockchain security.
Mechanisms Behind 51% Attack
A 51% attack occurs when a single entity gains control of the majority of a blockchain network's hash rate, enabling them to manipulate transaction records and double-spend coins. This attack leverages computational power to rewrite transaction history by outpacing the honest miners, disrupting consensus mechanisms such as Proof of Work (PoW). Unlike Sybil attacks that rely on creating numerous fake identities to influence network decisions, 51% attacks exploit actual mining power concentration to compromise blockchain security.
How Sybil Attacks Operate
Sybil attacks operate by creating numerous fake identities to gain disproportionate influence over a blockchain network, enabling the attacker to manipulate consensus processes or disrupt network operations. Unlike 51% attacks that require controlling the majority of computational power, Sybil attacks exploit trust assumptions by overwhelming the system with counterfeit nodes. This method undermines decentralization, allowing attackers to skew transaction validation and propagate false information across the blockchain.
Consequences of a 51% Attack
A 51% attack compromises the integrity of a blockchain by allowing attackers to double-spend coins, censor transactions, and disrupt network consensus, leading to the potential collapse of trust and value in the cryptocurrency. This attack undermines transaction finality, enabling malicious actors to reverse confirmed transactions and execute fraudulent activities. In contrast, a Sybil attack primarily targets network nodes and reputations but does not inherently allow control over blockchain consensus or transaction history.
Impacts of a Sybil Attack on Blockchain Networks
A Sybil attack in blockchain networks undermines the integrity of consensus mechanisms by allowing a single malicious actor to create multiple fake identities, disproportionately influencing network decisions and disrupting transaction validation. This manipulation can lead to double-spending, reduced trustworthiness of the ledger, and delays in block confirmations, severely compromising network security and reliability. Unlike a 51% attack, which requires control over the majority of mining power, Sybil attacks exploit identity verification weaknesses, making decentralized networks vulnerable to infiltration and control without massive computational resources.
Key Differences: 51% Attack vs Sybil Attack
A 51% attack occurs when a single miner or group controls over half of the blockchain's mining power, enabling them to manipulate transactions and double-spend coins. A Sybil attack involves creating numerous fake identities to gain disproportionate influence over the network, often targeting consensus mechanisms relying on node voting. Unlike the resource-intensive 51% attack, the Sybil attack exploits network identity weaknesses but does not require mining power control.
Preventive Measures Against Both Attacks
Preventive measures against 51% attacks include implementing robust consensus algorithms like Proof of Stake (PoS) to reduce the risk of any single entity gaining majority control over the network's hash power. Sybil attack prevention emphasizes identity verification techniques and resource cost imposition, such as using Proof of Work (PoW) or reputation systems, to limit the creation of fake identities in the network. Combining decentralized validation with network monitoring tools enhances overall blockchain security by mitigating vulnerabilities to both 51% and Sybil attacks.
Strengthening Blockchain Resilience
A 51% attack involves a single entity controlling the majority of the blockchain's mining power, enabling double-spending and transaction manipulation, while a Sybil attack floods the network with numerous fake identities to gain influence. Strengthening blockchain resilience requires robust consensus algorithms like Proof of Stake and hybrid models that decentralize control and verify node legitimacy using cryptographic proofs and reputation systems. Enhancing network security also involves continuous monitoring, node authentication, and incentivizing honest participation to mitigate vulnerabilities from both attack vectors.
51% Attack vs Sybil Attack Infographic
 techiny.com
techiny.com