Hash functions generate a fixed-size string of characters from input data, ensuring data integrity by detecting any alterations. Digital signatures use cryptographic algorithms to verify the authenticity and origin of a message or document, providing non-repudiation. While hash functions alone confirm data integrity, digital signatures combine hashing with encryption to validate identity and secure transactions on the blockchain.
Table of Comparison
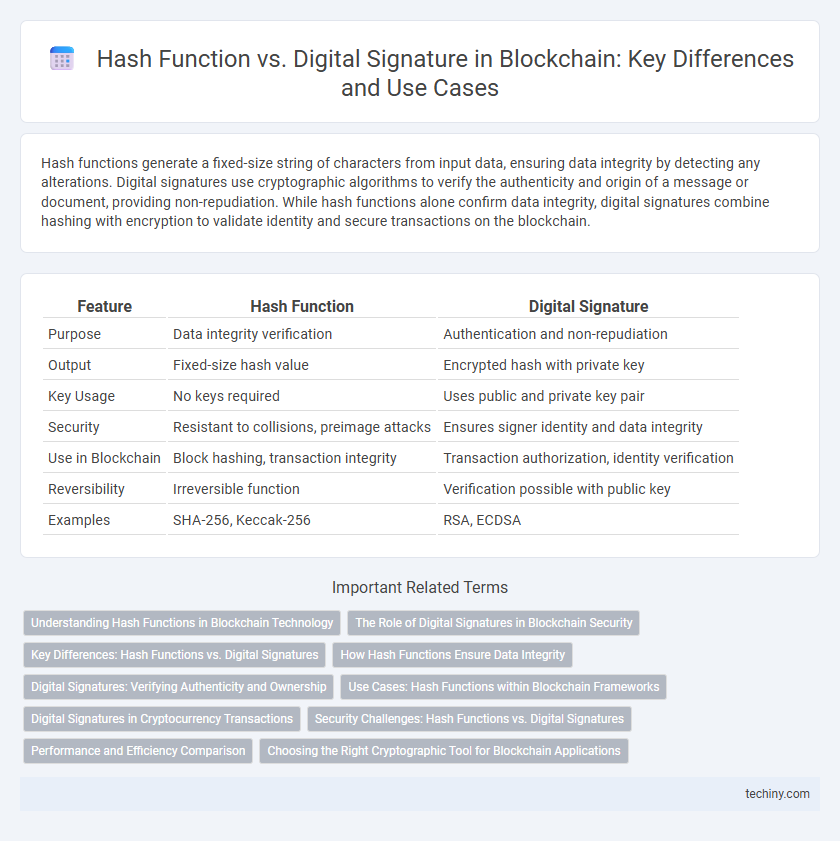
| Feature | Hash Function | Digital Signature |
|---|---|---|
| Purpose | Data integrity verification | Authentication and non-repudiation |
| Output | Fixed-size hash value | Encrypted hash with private key |
| Key Usage | No keys required | Uses public and private key pair |
| Security | Resistant to collisions, preimage attacks | Ensures signer identity and data integrity |
| Use in Blockchain | Block hashing, transaction integrity | Transaction authorization, identity verification |
| Reversibility | Irreversible function | Verification possible with public key |
| Examples | SHA-256, Keccak-256 | RSA, ECDSA |
Understanding Hash Functions in Blockchain Technology
Hash functions in blockchain technology generate fixed-size outputs from variable-length inputs, ensuring data integrity and immutability by producing unique hash values for each transaction or block. Unlike digital signatures that provide authentication and non-repudiation through asymmetric cryptography, hash functions serve primarily to verify data consistency and detect alterations. The efficiency and collision resistance of these hash algorithms, such as SHA-256, are critical for maintaining blockchain security and trust.
The Role of Digital Signatures in Blockchain Security
Digital signatures in blockchain security provide authentication and non-repudiation by using asymmetric cryptography to verify the identity of transaction creators, ensuring data integrity and preventing unauthorized modifications. Unlike hash functions that generate fixed-size outputs for data verification, digital signatures bind a transaction to a specific user with a private key, enabling trustless verification across decentralized networks. This cryptographic mechanism underpins blockchain's immutability and trust by enabling secure validation of transactions without revealing private keys.
Key Differences: Hash Functions vs. Digital Signatures
Hash functions generate a fixed-size output from input data, ensuring data integrity by detecting any changes but do not provide authentication or non-repudiation. Digital signatures use asymmetric cryptography involving private and public keys to authenticate the sender and guarantee data origin, offering non-repudiation and integrity verification simultaneously. Unlike hash functions, digital signatures provide proof of origin and enable verification without exposing the private key.
How Hash Functions Ensure Data Integrity
Hash functions ensure data integrity by generating a fixed-size hash value unique to the input data, allowing quick detection of any changes or tampering. This cryptographic process enables verification of data authenticity without revealing the original content, maintaining confidentiality while detecting modifications. Unlike digital signatures, hash functions alone do not provide authentication but serve as a crucial component in validating data consistency across distributed blockchain networks.
Digital Signatures: Verifying Authenticity and Ownership
Digital signatures play a crucial role in blockchain by verifying the authenticity and ownership of transactions. They use asymmetric cryptography to create a unique signature with a private key, which can be validated by others using the corresponding public key, ensuring data integrity and non-repudiation. This mechanism guarantees that only the rightful owner can authorize transactions, enhancing trust and security in decentralized networks.
Use Cases: Hash Functions within Blockchain Frameworks
Hash functions are integral to blockchain frameworks, enabling data integrity verification by converting input data into fixed-length hash values that uniquely represent the original content. They facilitate efficient transaction validation, secure block linking, and tamper detection by ensuring any alteration in data produces a different hash. Unlike digital signatures, which provide authentication and non-repudiation through asymmetric cryptography, hash functions are primarily used for ensuring immutability and consistency within the blockchain ledger.
Digital Signatures in Cryptocurrency Transactions
Digital signatures play a crucial role in cryptocurrency transactions by ensuring authenticity and integrity through unique cryptographic keys tied to user identities. Unlike hash functions that generate fixed-size outputs from data, digital signatures verify the origin and prevent tampering by linking transaction data with the sender's private key. This cryptographic mechanism empowers secure peer-to-peer transfers and bolsters trust within decentralized blockchain networks.
Security Challenges: Hash Functions vs. Digital Signatures
Hash functions provide data integrity by generating unique fixed-size outputs for variable inputs, but they lack authentication and non-repudiation, making them vulnerable to collision and preimage attacks. Digital signatures enhance security by combining hash functions with asymmetric cryptography, offering authentication, non-repudiation, and integrity verification, yet they face challenges related to key management and quantum computing threats. Ensuring robust security in blockchain systems requires addressing these vulnerabilities through advanced cryptographic algorithms and continuous protocol updates.
Performance and Efficiency Comparison
Hash functions offer superior performance and efficiency due to their ability to quickly produce fixed-size outputs from variable-length inputs using low computational power. Digital signatures, while crucial for authentication and non-repudiation, involve more complex algorithms like RSA or ECDSA that require higher processing time and energy consumption. In blockchain applications, hash functions enable fast data integrity checks, whereas digital signatures ensure secure user identity verification despite their relatively slower performance.
Choosing the Right Cryptographic Tool for Blockchain Applications
Hash functions provide fixed-size outputs that uniquely represent input data, ensuring data integrity and fast verification within blockchain systems. Digital signatures use asymmetric cryptography to authenticate identity and authorize transactions, offering non-repudiation and enhanced security. Selecting the appropriate cryptographic tool depends on whether the primary need is data integrity verification, for which hash functions suffice, or identity authentication and transaction authorization, which require digital signatures.
Hash function vs Digital signature Infographic
 techiny.com
techiny.com