Tenant isolation ensures that each user's data and applications remain secure and separate within a shared cloud environment, preventing unauthorized access and data leakage. Resource pooling optimizes cloud infrastructure by dynamically allocating computing resources among multiple tenants, increasing efficiency and cost-effectiveness. Balancing tenant isolation with resource pooling is critical to maintaining security while maximizing the scalability and utilization of cloud services.
Table of Comparison
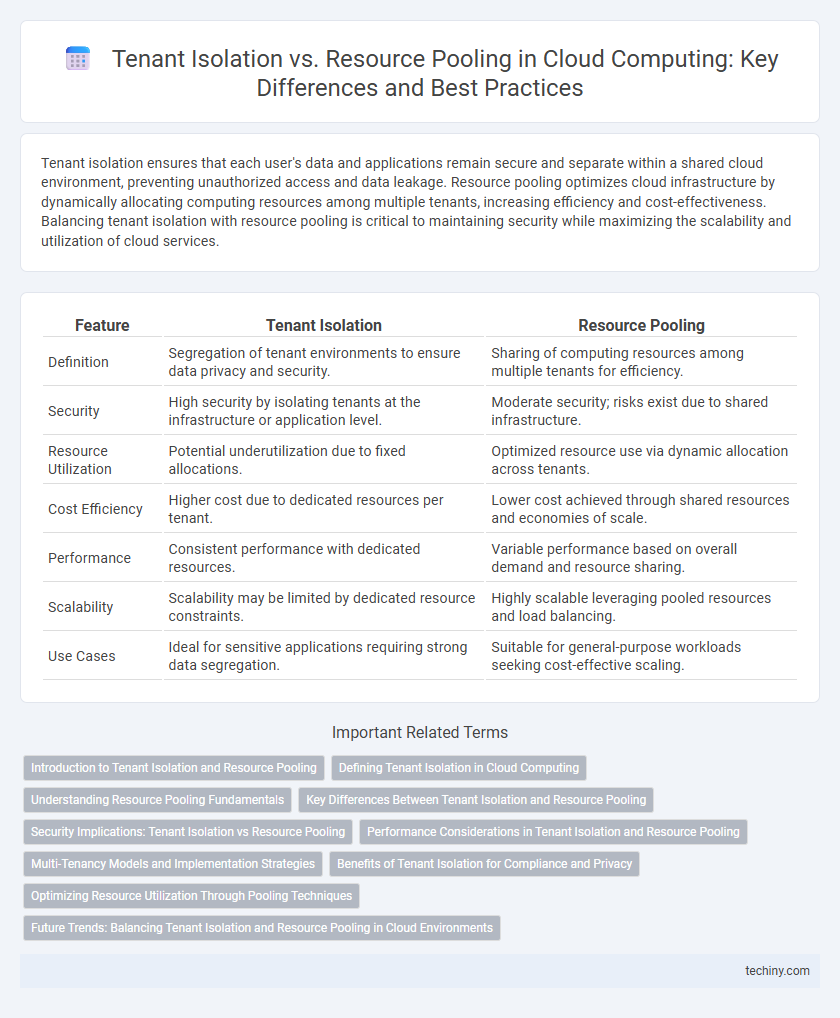
| Feature | Tenant Isolation | Resource Pooling |
|---|---|---|
| Definition | Segregation of tenant environments to ensure data privacy and security. | Sharing of computing resources among multiple tenants for efficiency. |
| Security | High security by isolating tenants at the infrastructure or application level. | Moderate security; risks exist due to shared infrastructure. |
| Resource Utilization | Potential underutilization due to fixed allocations. | Optimized resource use via dynamic allocation across tenants. |
| Cost Efficiency | Higher cost due to dedicated resources per tenant. | Lower cost achieved through shared resources and economies of scale. |
| Performance | Consistent performance with dedicated resources. | Variable performance based on overall demand and resource sharing. |
| Scalability | Scalability may be limited by dedicated resource constraints. | Highly scalable leveraging pooled resources and load balancing. |
| Use Cases | Ideal for sensitive applications requiring strong data segregation. | Suitable for general-purpose workloads seeking cost-effective scaling. |
Introduction to Tenant Isolation and Resource Pooling
Tenant isolation ensures that each customer's data and applications remain separate and secure within a multi-tenant cloud environment, preventing unauthorized access and data leakage. Resource pooling allows cloud providers to allocate and manage computing resources dynamically across multiple tenants, optimizing utilization and scalability. Both concepts are fundamental for delivering efficient, secure, and cost-effective cloud services.
Defining Tenant Isolation in Cloud Computing
Tenant isolation in cloud computing ensures that multiple customers, or tenants, securely share the same physical infrastructure without interference or data leakage. This segregation protects each tenant's applications, data, and configurations by employing virtual machines, containers, or strict access controls. Tenant isolation enhances security, privacy, and performance consistency within multi-tenant cloud environments.
Understanding Resource Pooling Fundamentals
Resource pooling in cloud computing involves allocating and managing a shared pool of configurable computing resources to serve multiple tenants dynamically. This approach maximizes efficiency by abstracting and virtualizing hardware, enabling scalable resource allocation based on real-time demand. Understanding resource pooling fundamentals is essential for balancing performance optimization with robust tenant isolation, ensuring secure multi-tenant environments.
Key Differences Between Tenant Isolation and Resource Pooling
Tenant isolation ensures that each customer's data and applications operate in a segregated environment, preventing interference and enhancing security. Resource pooling consolidates computing resources like CPU, memory, and storage to be dynamically allocated among multiple users, maximizing efficiency and cost-effectiveness. The key difference lies in tenant isolation prioritizing security and data privacy, while resource pooling emphasizes optimal utilization and scalability of shared infrastructure.
Security Implications: Tenant Isolation vs Resource Pooling
Tenant isolation enhances cloud security by segregating resources and data, minimizing risks of cross-tenant data breaches and unauthorized access. Resource pooling improves efficiency and scalability but introduces potential vulnerabilities where shared resources could be exploited, increasing the attack surface. Implementing robust access controls and encryption is critical to mitigate security risks inherent in resource pooling environments.
Performance Considerations in Tenant Isolation and Resource Pooling
Tenant isolation in cloud computing ensures dedicated resources for each user, minimizing latency and reducing performance variability caused by noisy neighbors. Resource pooling maximizes overall infrastructure utilization by dynamically allocating shared resources, but can introduce contention impacting application responsiveness under high demand. Balancing tenant isolation for predictable performance with resource pooling for cost efficiency requires sophisticated workload management and intelligent resource allocation strategies.
Multi-Tenancy Models and Implementation Strategies
Tenant isolation in multi-tenancy models ensures data security and privacy by segregating each tenant's resources, preventing unauthorized access and interference. Resource pooling optimizes cloud infrastructure by dynamically allocating shared resources such as CPU, memory, and storage among multiple tenants to maximize efficiency and reduce costs. Implementation strategies often combine virtualization, containerization, and strict access controls to balance tenant isolation with resource pooling, enhancing scalability and performance in cloud environments.
Benefits of Tenant Isolation for Compliance and Privacy
Tenant isolation in cloud computing ensures data segregation, significantly enhancing compliance with regulations such as GDPR and HIPAA by preventing unauthorized access across tenants. This strict separation safeguards sensitive information, reducing the risk of data breaches and enabling organizations to maintain stringent privacy standards. Isolated environments also support auditability and control, essential for meeting industry-specific compliance requirements.
Optimizing Resource Utilization Through Pooling Techniques
Resource pooling in cloud computing consolidates physical and virtual resources to serve multiple tenants efficiently, maximizing overall resource utilization and reducing costs. Tenant isolation techniques ensure security and privacy by logically separating data and processes, preventing unauthorized access while maintaining performance. Optimizing resource allocation through intelligent pooling algorithms enhances scalability and fault tolerance, providing balanced computing power without sacrificing tenant-specific controls.
Future Trends: Balancing Tenant Isolation and Resource Pooling in Cloud Environments
Future trends in cloud computing emphasize advanced tenant isolation techniques combined with dynamic resource pooling to enhance security while optimizing resource utilization. Innovations like zero-trust architectures and machine learning-driven resource management enable precise allocation without compromising data privacy. These developments facilitate scalable multi-tenant environments, supporting both compliance requirements and operational efficiency in evolving cloud ecosystems.
Tenant Isolation vs Resource Pooling Infographic
 techiny.com
techiny.com