Public key cryptography in the Internet of Things enables secure data transmission by using a pair of keys: a publicly shared key for encryption and a private key for decryption, ensuring authenticity and confidentiality. Private keys must remain confidential to protect device identity and prevent unauthorized access within IoT networks. Compared to symmetric key systems, the use of public and private keys enhances scalability and security in diverse IoT environments.
Table of Comparison
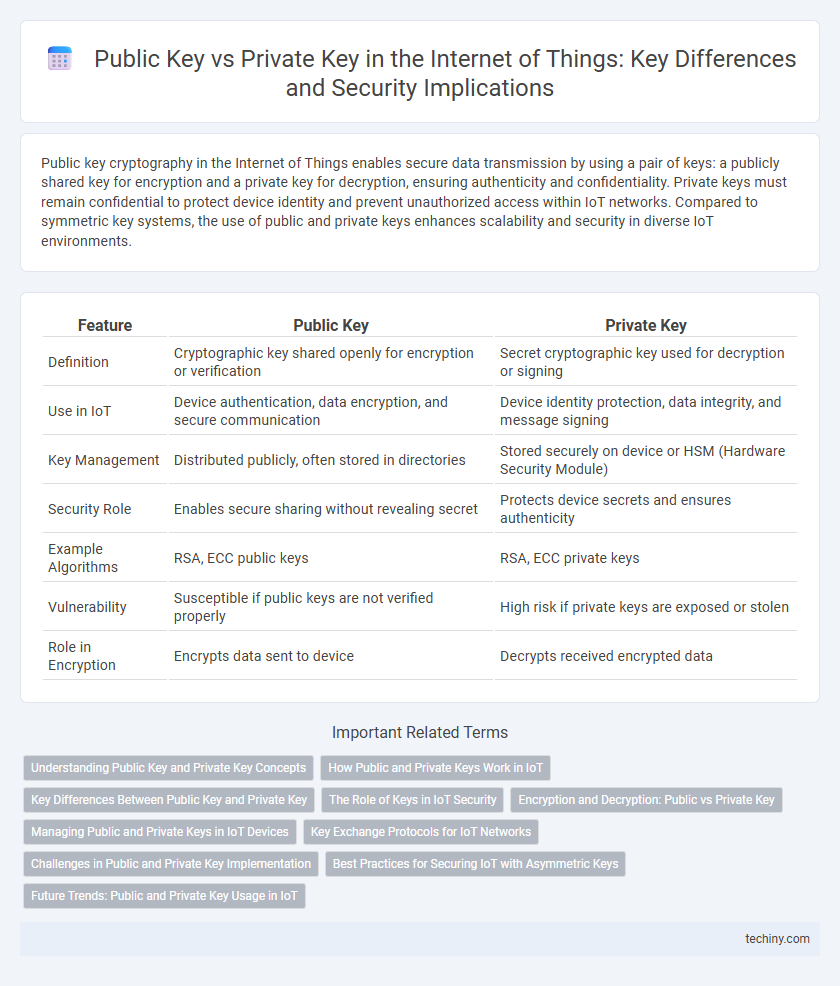
| Feature | Public Key | Private Key |
|---|---|---|
| Definition | Cryptographic key shared openly for encryption or verification | Secret cryptographic key used for decryption or signing |
| Use in IoT | Device authentication, data encryption, and secure communication | Device identity protection, data integrity, and message signing |
| Key Management | Distributed publicly, often stored in directories | Stored securely on device or HSM (Hardware Security Module) |
| Security Role | Enables secure sharing without revealing secret | Protects device secrets and ensures authenticity |
| Example Algorithms | RSA, ECC public keys | RSA, ECC private keys |
| Vulnerability | Susceptible if public keys are not verified properly | High risk if private keys are exposed or stolen |
| Role in Encryption | Encrypts data sent to device | Decrypts received encrypted data |
Understanding Public Key and Private Key Concepts
Public key and private key are fundamental components of asymmetric cryptography used in Internet of Things (IoT) security. The public key, accessible to anyone, encrypts data or verifies digital signatures, while the private key remains confidential to decrypt data or create signatures. This dual-key mechanism ensures secure communication, device authentication, and data integrity across IoT networks.
How Public and Private Keys Work in IoT
Public and private keys in IoT utilize asymmetric cryptography to secure device communication and data exchange. The public key encrypts data sent to IoT devices, while the private key, stored securely on the device, decrypts the data to ensure confidentiality and authenticity. This key pair mechanism enables secure device identity verification, message integrity, and prevents unauthorized access in IoT networks.
Key Differences Between Public Key and Private Key
Public key cryptography in the Internet of Things (IoT) involves a pair of keys: a publicly shared key for encrypting data and a private key kept secret for decryption, ensuring secure communication between devices. Public keys enable secure data transmission across untrusted networks, while private keys authenticate the identity of IoT devices and prevent unauthorized access. The fundamental difference lies in their usage--public keys distribute openly for encryption or signature verification, whereas private keys remain confidential to decrypt messages or create digital signatures.
The Role of Keys in IoT Security
Public key cryptography enables secure communication in IoT by using a pair of mathematically linked keys: a public key for encryption and a private key for decryption, ensuring data confidentiality and integrity. In IoT environments, private keys remain securely stored on devices to authenticate identity and authorize access, preventing unauthorized intrusions. Robust key management protocols and hardware security modules are essential in IoT to protect private keys from compromise and maintain end-to-end secure data transmission.
Encryption and Decryption: Public vs Private Key
Public key encryption uses a pair of cryptographic keys where the public key encrypts data, ensuring secure transmission in IoT networks, while the corresponding private key decrypts the information, maintaining confidentiality. Private key encryption employs a single secret key for both encryption and decryption, which requires secure key distribution among IoT devices to prevent unauthorized access. In IoT security, public key cryptography enhances scalability and trust through asymmetric encryption, whereas private key systems offer faster encryption processes but demand robust key management.
Managing Public and Private Keys in IoT Devices
Managing public and private keys in IoT devices is crucial for ensuring secure communication and authentication within connected networks. Public key infrastructure (PKI) enables encryption and digital signatures by distributing public keys openly while safeguarding private keys on each device to prevent unauthorized access. Implementing robust key management protocols, such as hardware security modules (HSMs) or secure elements, protects private keys from compromise and maintains the integrity of IoT ecosystems.
Key Exchange Protocols for IoT Networks
Key exchange protocols in IoT networks leverage public and private keys to establish secure communication channels, ensuring data confidentiality and authentication between devices. Public key cryptography enables devices to share encrypted messages without exposing private keys, while private keys remain confidential to decrypt received messages securely. Efficient key exchange methods, such as Elliptic Curve Diffie-Hellman (ECDH), optimize resource-constrained IoT devices by minimizing computational overhead and enhancing security in dynamic network environments.
Challenges in Public and Private Key Implementation
Implementing public and private key cryptography in Internet of Things (IoT) devices faces significant challenges due to resource constraints such as limited processing power, memory, and battery life. Ensuring secure key storage and management is critical, as IoT devices often operate in physically exposed environments vulnerable to tampering and cyber attacks. Scalability issues arise from the need to efficiently manage and distribute keys across millions of interconnected devices while maintaining robust authentication mechanisms.
Best Practices for Securing IoT with Asymmetric Keys
Securing IoT devices with asymmetric keys involves using public keys for encrypting data and private keys for decryption to ensure confidentiality and authentication. Best practices include generating strong, unique key pairs, securely storing private keys using hardware security modules (HSMs) or secure elements, and regularly rotating keys to minimize exposure. Implementing robust key management protocols and leveraging Public Key Infrastructure (PKI) enhances trust and protects IoT ecosystems against unauthorized access and data breaches.
Future Trends: Public and Private Key Usage in IoT
Emerging trends in IoT security increasingly leverage hybrid cryptographic models combining public and private keys to balance scalability and efficiency across diverse devices. Quantum-resistant algorithms are being integrated with traditional public key infrastructure to future-proof IoT ecosystems against advances in quantum computing threats. The proliferation of edge computing further drives innovation in secure key management, enabling decentralized authentication and encryption tailored to real-time IoT applications.
Public key vs Private key Infographic
 techiny.com
techiny.com