A DMZ (Demilitarized Zone) is a network segment that acts as a buffer zone between an internal network and untrusted external networks, providing an additional layer of security by isolating public-facing services. A Bastion Host is a specialized system hardened and exposed to external threats, designed to withstand attacks while allowing secure access to a protected network. Unlike a DMZ, which is a separate network area, a Bastion Host serves as a controlled point of entry, often hosting gateway services like firewalls or proxies.
Table of Comparison
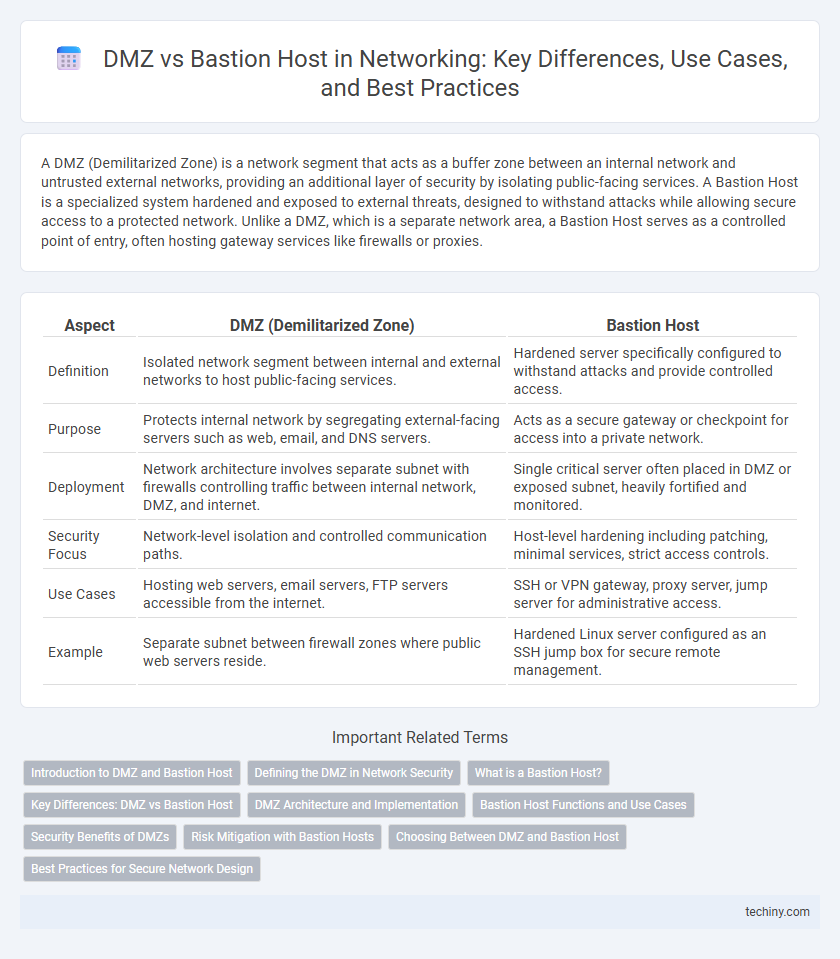
| Aspect | DMZ (Demilitarized Zone) | Bastion Host |
|---|---|---|
| Definition | Isolated network segment between internal and external networks to host public-facing services. | Hardened server specifically configured to withstand attacks and provide controlled access. |
| Purpose | Protects internal network by segregating external-facing servers such as web, email, and DNS servers. | Acts as a secure gateway or checkpoint for access into a private network. |
| Deployment | Network architecture involves separate subnet with firewalls controlling traffic between internal network, DMZ, and internet. | Single critical server often placed in DMZ or exposed subnet, heavily fortified and monitored. |
| Security Focus | Network-level isolation and controlled communication paths. | Host-level hardening including patching, minimal services, strict access controls. |
| Use Cases | Hosting web servers, email servers, FTP servers accessible from the internet. | SSH or VPN gateway, proxy server, jump server for administrative access. |
| Example | Separate subnet between firewall zones where public web servers reside. | Hardened Linux server configured as an SSH jump box for secure remote management. |
Introduction to DMZ and Bastion Host
A DMZ (Demilitarized Zone) is a network segment that acts as a buffer zone between an organization's internal network and untrusted external networks, such as the internet, designed to host public-facing services while protecting the internal infrastructure. A Bastion Host is a specialized server located within the DMZ, hardened and configured to withstand attacks, serving as a secure gateway for external users to access specific services. Both concepts enhance network security by isolating and controlling access, with the DMZ providing a protective boundary and the Bastion Host functioning as a fortified access point.
Defining the DMZ in Network Security
A Demilitarized Zone (DMZ) in network security is a physical or logical subnet that separates an internal local area network (LAN) from untrusted external networks, typically the internet, to add an additional layer of security. It hosts public-facing servers like web, email, and DNS servers, allowing external users to access these services while keeping the internal network shielded from direct exposure. By restricting direct access between the public internet and the internal network, the DMZ mitigates the risk of external attacks spreading inward.
What is a Bastion Host?
A Bastion Host is a specialized server designed to withstand attacks and provide secure access to a private network from an external environment. It acts as a fortified gateway, often configured with strict security policies and minimal services to reduce vulnerabilities. Commonly positioned within the network architecture's DMZ, a Bastion Host enables controlled and monitored access, enhancing overall network security.
Key Differences: DMZ vs Bastion Host
A DMZ (Demilitarized Zone) is a physical or logical subnet that separates an internal local area network (LAN) from untrusted external networks, typically used to host public-facing services like web servers, providing an additional layer of security. A Bastion Host is a specifically hardened server within the DMZ designed to withstand attacks, often acting as a gateway or proxy between external users and internal networks. While the DMZ provides a buffer zone for exposing services, the Bastion Host serves as a critical secure access point with minimal services and strict access controls.
DMZ Architecture and Implementation
A DMZ (Demilitarized Zone) architecture establishes a physical or logical subnet that separates an organization's internal network from untrusted external networks, typically the internet, enhancing security by isolating public-facing services. Implementation involves deploying multiple firewalls or a firewall with multiple interfaces to control and monitor traffic between the internal network, the DMZ, and external networks, ensuring only necessary services are exposed. This layered approach minimizes attack surface and prevents direct access to internal systems, improving overall network defense.
Bastion Host Functions and Use Cases
A Bastion Host serves as a specialized gateway, providing a secure access point to a private network by filtering and monitoring incoming traffic on critical ports like SSH and RDP. It functions as a hardened system, often isolated from other internal resources, to withstand direct attacks while facilitating controlled remote management and administration. Common use cases include enabling secure remote access for administrators, acting as a jump server for accessing internal machines, and serving as a critical defense layer in network security architectures.
Security Benefits of DMZs
DMZs enhance network security by isolating public-facing services from the internal network, reducing the attack surface and limiting potential damage from breaches. They provide a controlled buffer zone where incoming traffic is filtered and monitored before reaching sensitive internal systems. Compared to bastion hosts, DMZs offer layered defense with multiple security mechanisms such as intrusion detection systems, firewalls, and segmented zones to prevent lateral movement of threats.
Risk Mitigation with Bastion Hosts
Bastion hosts enhance risk mitigation by serving as hardened, single points of entry within a network, reducing the attack surface exposed to external threats. Unlike DMZs, which create segmented network zones, bastion hosts are specifically fortified to resist attacks through strict access controls and minimal services. Their strategic placement and configuration help prevent unauthorized access, limiting potential damage from intrusions.
Choosing Between DMZ and Bastion Host
Choosing between a DMZ and a bastion host depends on network security requirements and architecture complexity. A DMZ provides a segmented network zone that isolates external-facing services from the internal network, enhancing protection against unauthorized access. Bastion hosts, hardened and exposed to untrusted networks, offer focused defense for specific services but require rigorous monitoring and maintenance.
Best Practices for Secure Network Design
Implementing a DMZ (Demilitarized Zone) isolates public-facing services from the internal network, reducing attack surfaces by placing web servers, mail servers, and DNS servers in a controlled subnet. A Bastion Host serves as a hardened gateway for accessing internal resources, typically configured with minimal services and strict access controls to prevent unauthorized entry. Best practices include rigorous firewall rules, regular security patching, and network segmentation to ensure both the DMZ and Bastion Host effectively mitigate potential threats.
DMZ vs Bastion Host Infographic
 techiny.com
techiny.com