SYN Flood attacks overwhelm a network by exploiting the TCP handshake process, sending numerous SYN requests without completing the connection, leading to resource exhaustion on the target server. ICMP Flood attacks saturate the network by bombarding the target with excessive ICMP Echo Request packets, causing high latency and packet loss. Both attack types disrupt service availability but target different protocol vulnerabilities, with SYN Flood focusing on TCP connection resources and ICMP Flood overwhelming network bandwidth.
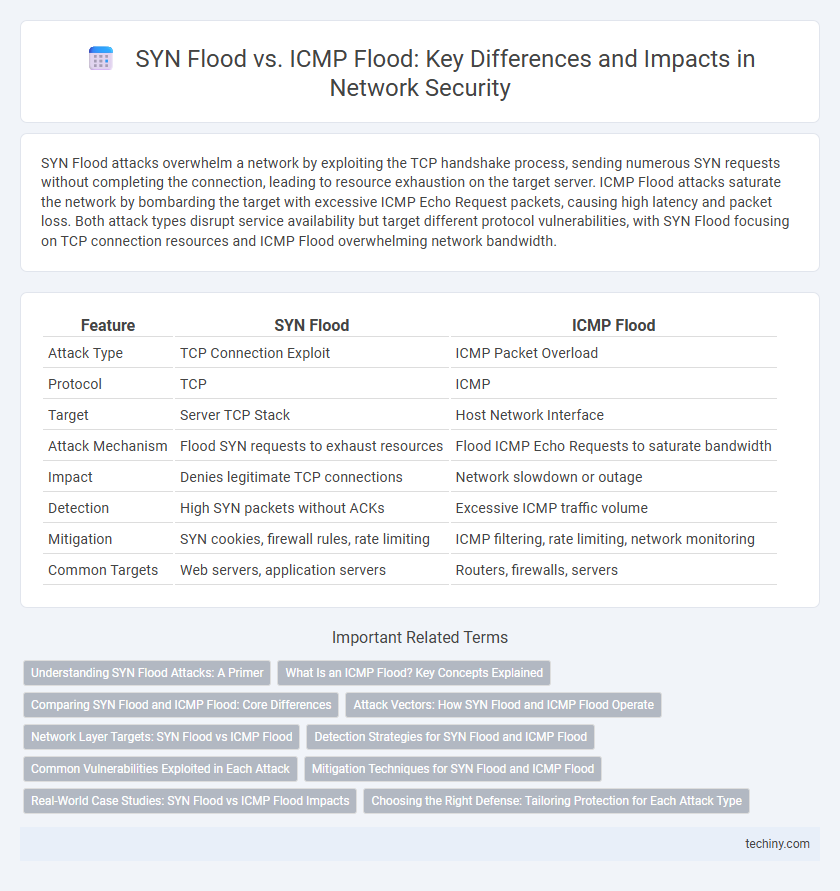
Table of Comparison
| Feature | SYN Flood | ICMP Flood |
|---|---|---|
| Attack Type | TCP Connection Exploit | ICMP Packet Overload |
| Protocol | TCP | ICMP |
| Target | Server TCP Stack | Host Network Interface |
| Attack Mechanism | Flood SYN requests to exhaust resources | Flood ICMP Echo Requests to saturate bandwidth |
| Impact | Denies legitimate TCP connections | Network slowdown or outage |
| Detection | High SYN packets without ACKs | Excessive ICMP traffic volume |
| Mitigation | SYN cookies, firewall rules, rate limiting | ICMP filtering, rate limiting, network monitoring |
| Common Targets | Web servers, application servers | Routers, firewalls, servers |
Understanding SYN Flood Attacks: A Primer
SYN flood attacks exploit the TCP handshake process by overwhelming a target server with a high volume of SYN requests, causing resource exhaustion and denial of legitimate connections. This attack differs from ICMP flood attacks, which rely on saturating the target's bandwidth with excessive ping requests rather than exploiting protocol vulnerabilities. Understanding the mechanics of SYN flood attacks is essential for implementing effective mitigation strategies such as SYN cookies and rate limiting to maintain network availability.
What Is an ICMP Flood? Key Concepts Explained
An ICMP Flood is a type of Denial of Service (DoS) attack that overwhelms a target network or device by sending a high volume of Internet Control Message Protocol (ICMP) Echo Request packets, commonly known as pings. Unlike a SYN Flood, which exploits the TCP handshake process to exhaust server resources, an ICMP Flood saturates the victim's bandwidth or processing capacity by flooding it with ICMP traffic, causing network congestion and service disruption. Key concepts include the attacker exploiting the network layer, the use of ICMP Echo Request and Echo Reply messages, and the impact on network availability due to resource depletion.
Comparing SYN Flood and ICMP Flood: Core Differences
SYN Flood attacks exploit the TCP handshake by overwhelming a server with SYN requests, causing resource depletion and connection table overflow, while ICMP Flood attacks saturate the target's bandwidth by sending excessive ICMP Echo Request packets, leading to network congestion and service disruption. SYN Floods primarily affect server availability through stateful connection exhaustion, whereas ICMP Floods degrade network performance by flooding data packets at the network layer. Both pose significant threats but differ fundamentally in their attack vectors and mitigation strategies, with SYN Flood defenses focusing on connection rate limiting and ICMP Flood typically requiring network traffic filtering.
Attack Vectors: How SYN Flood and ICMP Flood Operate
SYN Flood attacks exploit the TCP handshake process by sending a large number of SYN requests to a target server, overwhelming its ability to complete connections and causing resource exhaustion. ICMP Flood attacks generate a high volume of ICMP Echo Request packets (ping) to saturate the target's bandwidth and processing capacity, leading to network disruption. Both attacks leverage different protocols and mechanisms, but their common goal is to degrade or deny legitimate network service availability.
Network Layer Targets: SYN Flood vs ICMP Flood
SYN Flood attacks exploit TCP's handshake mechanism by overwhelming the target's network layer with half-open connection requests, exhausting server resources and causing denial of service. ICMP Flood attacks saturate the network layer by inundating the target with large volumes of ICMP Echo Request packets, leading to bandwidth exhaustion and degraded network performance. Both attacks compromise network layer availability but differ in protocol exploitation--SYN Flood targets TCP stateful connections while ICMP Flood leverages stateless ICMP echo operations.
Detection Strategies for SYN Flood and ICMP Flood
Effective detection of SYN Flood attacks relies on monitoring an abnormal surge in SYN packets without corresponding ACK responses, often using threshold-based algorithms and stateful inspection in firewalls or intrusion detection systems. ICMP Flood detection typically involves analyzing traffic patterns for excessive ICMP echo request packets by comparing baseline network behavior and employing rate limiting or anomaly-based detection methods. Combining packet rate analysis with behavioral profiling enhances accuracy in distinguishing SYN Flood and ICMP Flood attacks from legitimate network activity.
Common Vulnerabilities Exploited in Each Attack
SYN Flood attacks exploit the vulnerability in the TCP handshake process by overwhelming a target server with half-open SYN requests, exhausting its connection table and causing denial of service. ICMP Flood attacks leverage the lack of rate limiting in many networks, sending large volumes of ICMP Echo Request (ping) packets to consume bandwidth and processing resources. Both attacks exploit fundamental protocol weaknesses--SYN Flood abuses TCP state management, while ICMP Flood targets network-layer traffic handling.
Mitigation Techniques for SYN Flood and ICMP Flood
Effective mitigation of SYN Flood attacks involves deploying SYN cookies, adjusting the TCP backlog queue, and implementing rate limiting to reduce resource exhaustion on servers. For ICMP Flood attacks, techniques such as ICMP rate limiting, filtering suspicious ICMP packets at the network perimeter, and monitoring anomalous traffic patterns are essential to maintain network availability. Combining deep packet inspection and anomaly-based intrusion detection systems enhances the detection and prevention of both flood types.
Real-World Case Studies: SYN Flood vs ICMP Flood Impacts
SYN Flood attacks exploit the TCP handshake by overwhelming servers with half-open connections, causing resource exhaustion and service disruption in high-traffic environments, as seen in the 2018 GitHub outage. ICMP Floods saturate network bandwidth by flooding the target with echo requests, exemplified in the 2013 Spamhaus attack, which caused widespread internet slowdowns. Real-world impact analysis shows SYN Floods primarily degrade server availability, while ICMP Floods disrupt network-level connectivity, demanding tailored mitigation strategies.
Choosing the Right Defense: Tailoring Protection for Each Attack Type
SYN flood attacks exploit the TCP handshake by overwhelming a server with half-open connections, requiring defenses like SYN cookies and rate limiting to effectively mitigate. ICMP flood attacks target network bandwidth through excessive ping requests, making rate limiting and traffic filtering essential for reducing impact. Tailoring protection involves deploying stateful firewalls and intrusion prevention systems (IPS) that identify and block specific attack signatures for each flood type, ensuring optimized network security.
SYN Flood vs ICMP Flood Infographic
 techiny.com
techiny.com