Tunneling involves creating a virtual link between two networks that allows data packets to be sent securely across an incompatible or public network by wrapping them in a new packet with a different protocol header. Encapsulation refers to the process of enclosing data within protocol-specific headers and trailers to ensure proper transmission and routing through various layers of the network. While tunneling specifically creates a secure pathway by encapsulating packets for transport across intermediary networks, encapsulation broadly describes the method of packaging data for communication within or between network protocols.
Table of Comparison
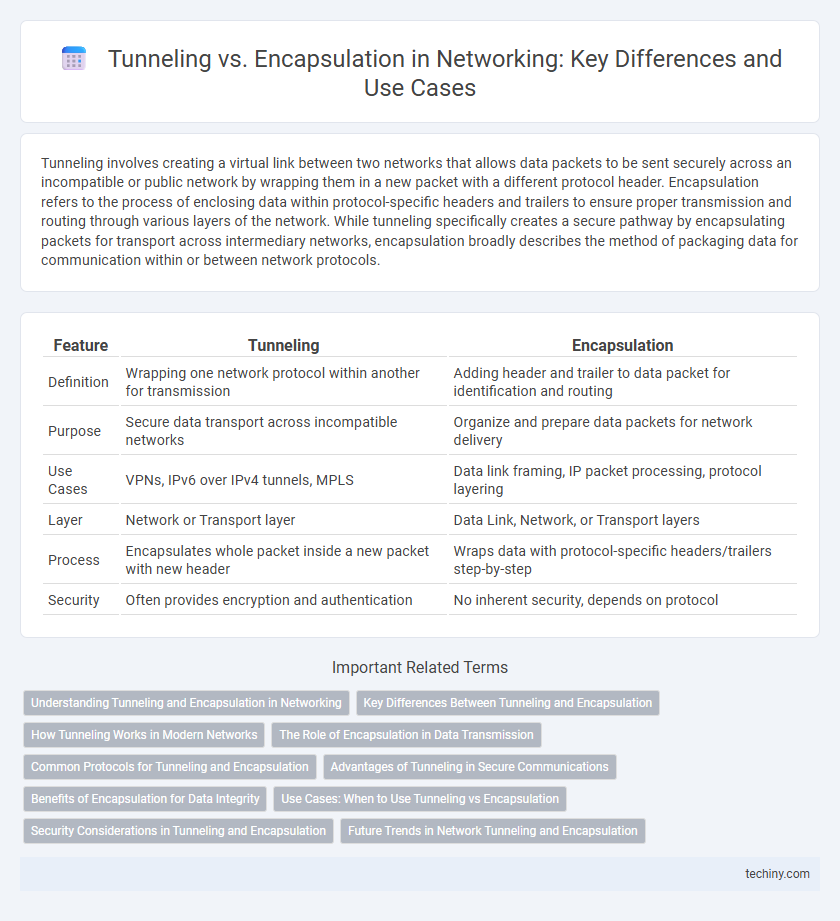
| Feature | Tunneling | Encapsulation |
|---|---|---|
| Definition | Wrapping one network protocol within another for transmission | Adding header and trailer to data packet for identification and routing |
| Purpose | Secure data transport across incompatible networks | Organize and prepare data packets for network delivery |
| Use Cases | VPNs, IPv6 over IPv4 tunnels, MPLS | Data link framing, IP packet processing, protocol layering |
| Layer | Network or Transport layer | Data Link, Network, or Transport layers |
| Process | Encapsulates whole packet inside a new packet with new header | Wraps data with protocol-specific headers/trailers step-by-step |
| Security | Often provides encryption and authentication | No inherent security, depends on protocol |
Understanding Tunneling and Encapsulation in Networking
Tunneling in networking refers to the process of encapsulating packets within another protocol to create a private communication path across a public network, often used in VPNs to securely transmit data. Encapsulation involves wrapping data with protocol-specific headers and trailers at each layer of the OSI model, enabling proper routing and delivery between network devices. Both techniques are essential for network interoperability and security, with tunneling providing a specific use case of encapsulation to maintain data integrity and confidentiality over diverse network infrastructures.
Key Differences Between Tunneling and Encapsulation
Tunneling involves encapsulating an entire packet within another packet to securely transmit data across incompatible networks, often using protocols like GRE or IPsec. Encapsulation refers to the process of wrapping data with protocol information at each layer of the OSI model, enabling proper delivery and communication between devices. Key differences include that tunneling creates a virtual point-to-point link over a public network, while encapsulation is a fundamental technique within network protocols for data packaging and transmission.
How Tunneling Works in Modern Networks
Tunneling in modern networks involves encapsulating one network protocol within another to securely transmit data across incompatible or public networks, such as the internet. It creates a virtual point-to-point connection by wrapping the original packet inside a new packet with a different protocol header, enabling secure and private communication over shared infrastructure. Protocols like GRE, IPsec, and L2TP are commonly employed to establish tunnels that maintain data integrity and confidentiality while facilitating seamless network interoperability.
The Role of Encapsulation in Data Transmission
Encapsulation plays a critical role in data transmission by wrapping data with necessary protocol information at each layer of the OSI model, ensuring proper routing and delivery across networks. Unlike tunneling, which creates a virtual pathway to transmit encapsulated packets through incompatible networks, encapsulation standardizes data packaging, allowing seamless communication between diverse systems. Efficient encapsulation enhances security and data integrity by enclosing payloads within headers and trailers that define control and error-checking mechanisms.
Common Protocols for Tunneling and Encapsulation
Common protocols for tunneling include GRE (Generic Routing Encapsulation), IPsec, and L2TP, which enable the secure transmission of data by encapsulating packets within another protocol header. Encapsulation often uses protocols like Ethernet, MPLS, and VLAN tagging to add metadata and facilitate data forwarding across networks. Tunneling focuses on creating virtual pathways for data through an encapsulation process, while encapsulation itself refers to the broader method of wrapping data for transmission within different protocol layers.
Advantages of Tunneling in Secure Communications
Tunneling enhances secure communications by creating a private pathway through an untrusted network, effectively isolating data from external threats. It supports encryption protocols such as IPsec and SSL/TLS, ensuring data confidentiality and integrity during transmission. Tunneling also enables seamless connectivity across heterogeneous networks, optimizing interoperability and reducing potential attack vectors.
Benefits of Encapsulation for Data Integrity
Encapsulation enhances data integrity by packaging data with protocol-specific headers and trailers, ensuring accurate delivery and error detection throughout network transmission. It provides a structured format that isolates and protects the original data from corruption or unauthorized access during routing across diverse networks. This methodology supports reliable communication by maintaining the integrity of data packets through each layer of the OSI model.
Use Cases: When to Use Tunneling vs Encapsulation
Tunneling is ideal for securely transmitting entire protocols or networks over incompatible or public infrastructures, commonly used in Virtual Private Networks (VPNs) and connecting disparate network segments. Encapsulation is preferred within local or controlled environments to package data with specific headers for routing, such as VLAN tagging or protocol layering in OSI models. Use tunneling for privacy and protocol transport across the internet, while encapsulation efficiently enables protocol interoperability and data segmentation within networks.
Security Considerations in Tunneling and Encapsulation
Tunneling and encapsulation both provide methods to secure data transmission by hiding original packet contents, but tunneling often offers enhanced security through techniques like encryption and secure protocols such as IPsec or GRE. Encapsulation primarily focuses on wrapping data within additional headers for routing or protocol compatibility, with security relying heavily on the outer protocol's features rather than inherent protection. Effective network security strategies integrate robust tunneling protocols to ensure data confidentiality, integrity, and resistance against interception or tampering during transmission.
Future Trends in Network Tunneling and Encapsulation
Future trends in network tunneling and encapsulation emphasize increased adoption of lightweight protocols such as GRE and VXLAN to support scalable virtualization and cloud environments. Emerging technologies focus on enhanced security through advanced encryption methods integrated within tunneling frameworks to safeguard data in transit. Integration with software-defined networking (SDN) and network function virtualization (NFV) drives dynamic, programmable tunnel management for improved network agility and efficiency.
Tunneling vs Encapsulation Infographic
 techiny.com
techiny.com