JWT (JSON Web Token) serves as a compact, URL-safe means of representing claims between two parties, often used in stateless authentication to securely transmit user information. OAuth functions as an authorization framework that enables third-party applications to obtain limited access to user resources without exposing credentials, often leveraging tokens like JWT for access control. Understanding the distinction between JWT as a token format and OAuth as a protocol helps streamline secure user authentication and authorization in web development.
Table of Comparison
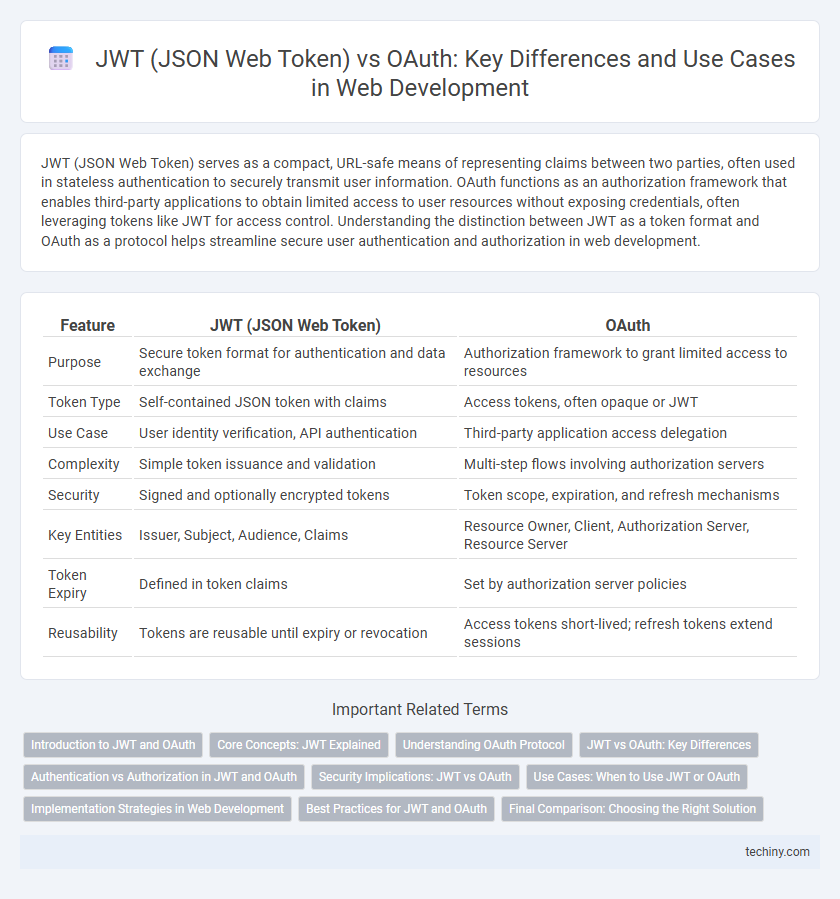
| Feature | JWT (JSON Web Token) | OAuth |
|---|---|---|
| Purpose | Secure token format for authentication and data exchange | Authorization framework to grant limited access to resources |
| Token Type | Self-contained JSON token with claims | Access tokens, often opaque or JWT |
| Use Case | User identity verification, API authentication | Third-party application access delegation |
| Complexity | Simple token issuance and validation | Multi-step flows involving authorization servers |
| Security | Signed and optionally encrypted tokens | Token scope, expiration, and refresh mechanisms |
| Key Entities | Issuer, Subject, Audience, Claims | Resource Owner, Client, Authorization Server, Resource Server |
| Token Expiry | Defined in token claims | Set by authorization server policies |
| Reusability | Tokens are reusable until expiry or revocation | Access tokens short-lived; refresh tokens extend sessions |
Introduction to JWT and OAuth
JWT (JSON Web Token) is a compact, URL-safe token format used for securely transmitting information between parties as a JSON object, commonly utilized for authentication and information exchange in web development. OAuth is an open standard authorization protocol that allows third-party applications to access user resources without exposing credentials, typically through token-based access delegation. Both JWT and OAuth are essential in modern web security, with JWT often employed as a token format within OAuth frameworks to facilitate secure user authentication and authorization.
Core Concepts: JWT Explained
JWT (JSON Web Token) is a compact, URL-safe token format used for securely transmitting information between parties as a JSON object, commonly employed for authentication and authorization in web development. It consists of three parts: a header, payload, and signature, enabling stateless, verifiable tokens that can be validated without server-side storage. Unlike OAuth, which is an authorization framework, JWT specifically provides a token mechanism that can be integrated into OAuth for identity and access management.
Understanding OAuth Protocol
OAuth protocol enables secure delegated access by allowing users to grant third-party applications limited permissions without sharing credentials. It operates through authorization tokens that define scopes and access duration, ensuring fine-grained control over resource sharing. Unlike JWT, which is a token format, OAuth is an authorization framework often using tokens like JWT to facilitate secure authentication and authorization workflows.
JWT vs OAuth: Key Differences
JWT (JSON Web Token) is a compact, URL-safe token format primarily used for securely transmitting information between parties as a JSON object, often utilized for authentication and information exchange. OAuth is an authorization framework that enables third-party applications to obtain limited access to user resources without exposing credentials, commonly leveraging tokens like JWT for access delegation. The key difference lies in JWT being a token specification focused on token structure and content, while OAuth defines a protocol for token issuance and access delegation processes.
Authentication vs Authorization in JWT and OAuth
JWT (JSON Web Token) primarily serves as a compact, URL-safe means of representing claims for user authentication, enabling secure identity verification without repeated credential exchanges. OAuth functions as an authorization framework that grants third-party applications limited access to user resources without exposing user credentials. While JWT is often used within OAuth protocols to convey authentication information, OAuth focuses on delegated authorization, differentiating user identity validation from access permissions.
Security Implications: JWT vs OAuth
JSON Web Tokens (JWT) provide stateless, compact, and self-contained token structures primarily used for authentication and information exchange but may be vulnerable to token theft and replay attacks if not properly secured. OAuth, as an authorization framework, leverages access tokens with scopes and expiration policies that enhance security by limiting permissions and reducing exposure duration. Implementing OAuth with JWT tokens can combine the benefits, but careful management of token storage, transmission, and validation is essential to mitigate risks such as token leakage and privilege escalation.
Use Cases: When to Use JWT or OAuth
JWT is ideal for stateless authentication in single-page applications, microservices, and API token sharing due to its compact, self-contained structure enabling secure information exchange. OAuth is better suited for delegated authorization scenarios, allowing third-party applications to access user resources without exposing credentials, commonly used in social login and permission granting across services. Choosing between JWT and OAuth depends on the need for simple identity verification versus complex authorization workflows involving multiple parties.
Implementation Strategies in Web Development
JWT (JSON Web Token) is primarily used for stateless authentication by securely transmitting user identity information between client and server, enabling scalable session management without server-side storage. OAuth, as an authorization framework, delegates access by issuing tokens for third-party applications to access user resources without exposing credentials, often integrating JWT tokens for access tokens. Effective implementation strategies in web development involve combining OAuth for secure authorization workflows with JWT for efficient authentication and token validation across distributed systems.
Best Practices for JWT and OAuth
Best practices for using JWT in web development include securely storing tokens on the client side, validating token signatures and expiration times on the server, and minimizing payload size to enhance performance and security. OAuth best practices emphasize using authorization code flow with PKCE to prevent interception, limiting scopes to the minimum required permissions, and securely managing client secrets and refresh tokens. Combining JWT with OAuth enables scalable, stateless authentication while maintaining fine-grained access control across distributed services.
Final Comparison: Choosing the Right Solution
JWT offers a compact and self-contained way for securely transmitting information between parties as a JSON object, ideal for stateless authentication in web applications. OAuth excels as an authorization framework that delegates access permissions without sharing user credentials, supporting complex permissions and third-party integrations. Choosing between JWT and OAuth depends on whether the goal is simple token-based authentication or robust delegated authorization for multi-service environments.
JWT (JSON Web Token) vs OAuth Infographic
 techiny.com
techiny.com