Coded obfuscation disguises the true nature of code by making it intentionally difficult to understand, thereby protecting software from reverse engineering and unauthorized access. Steganography conceals information within digital media, such as images or audio, hiding the presence of data rather than encrypting it. Both techniques enhance cybersecurity by safeguarding sensitive information, but obfuscation targets code protection while steganography focuses on covert data transmission.
Table of Comparison
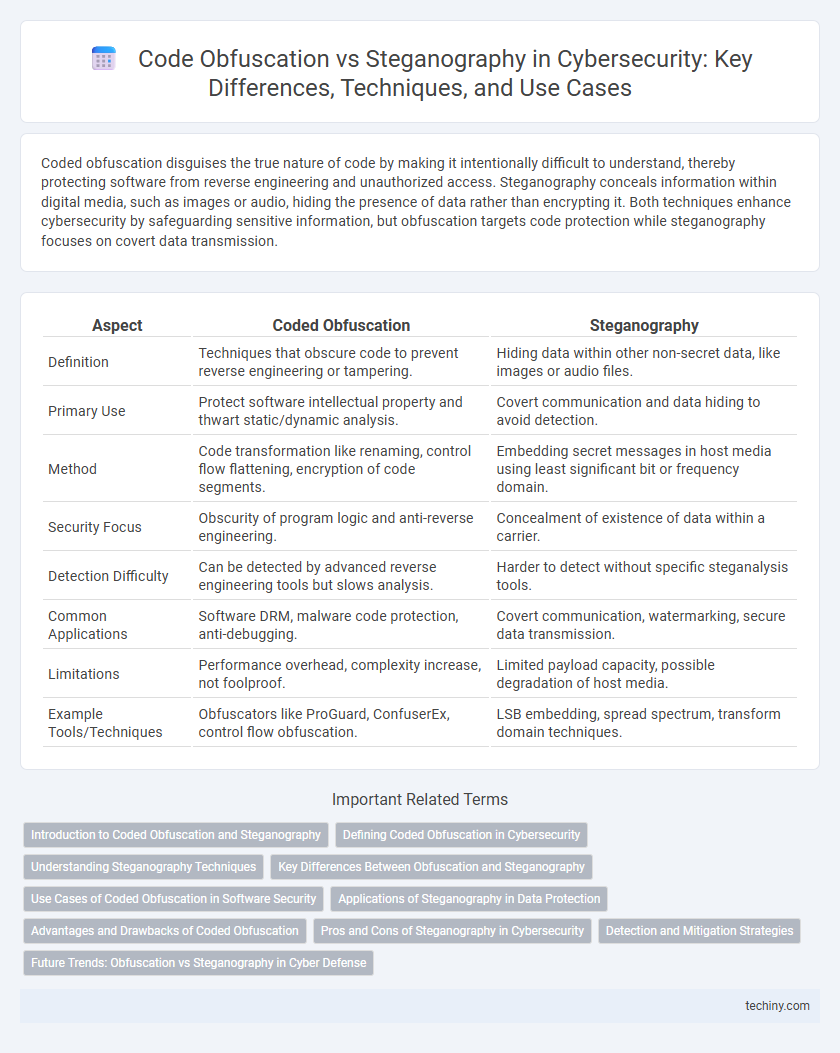
| Aspect | Coded Obfuscation | Steganography |
|---|---|---|
| Definition | Techniques that obscure code to prevent reverse engineering or tampering. | Hiding data within other non-secret data, like images or audio files. |
| Primary Use | Protect software intellectual property and thwart static/dynamic analysis. | Covert communication and data hiding to avoid detection. |
| Method | Code transformation like renaming, control flow flattening, encryption of code segments. | Embedding secret messages in host media using least significant bit or frequency domain. |
| Security Focus | Obscurity of program logic and anti-reverse engineering. | Concealment of existence of data within a carrier. |
| Detection Difficulty | Can be detected by advanced reverse engineering tools but slows analysis. | Harder to detect without specific steganalysis tools. |
| Common Applications | Software DRM, malware code protection, anti-debugging. | Covert communication, watermarking, secure data transmission. |
| Limitations | Performance overhead, complexity increase, not foolproof. | Limited payload capacity, possible degradation of host media. |
| Example Tools/Techniques | Obfuscators like ProGuard, ConfuserEx, control flow obfuscation. | LSB embedding, spread spectrum, transform domain techniques. |
Introduction to Coded Obfuscation and Steganography
Coded obfuscation transforms executable code or algorithms into a deliberately complex and unreadable format to protect intellectual property and prevent reverse engineering in cybersecurity. Steganography conceals sensitive data within innocuous files like images, audio, or video, hiding the very existence of the information from unauthorized users. Both techniques enhance security by obscuring data, but coded obfuscation focuses on protecting code structure, while steganography conceals the presence of hidden messages.
Defining Coded Obfuscation in Cybersecurity
Coded obfuscation in cybersecurity involves deliberately transforming code or algorithms to make them difficult to understand or reverse-engineer without altering their functionality. This technique protects intellectual property, sensitive logic, and software integrity by masking the true purpose of the code from attackers. Unlike steganography, which hides data within other files, coded obfuscation directly modifies program structure to resist code analysis and tampering.
Understanding Steganography Techniques
Steganography techniques involve embedding hidden messages within digital media such as images, audio, or video files, allowing confidential information to be concealed in plain sight without altering the file's apparent structure. Modern steganographic methods often utilize least significant bit (LSB) manipulation, masking, and transform domain techniques like DCT or DWT to securely encode data while minimizing detectability. These approaches contrast with coded obfuscation, which focuses on making code unintelligible but remains visibly present, whereas steganography's core advantage lies in covert communication through data concealment.
Key Differences Between Obfuscation and Steganography
Coded obfuscation transforms code to make it difficult to understand or reverse-engineer, primarily enhancing software security by hiding the program's logic. Steganography conceals information within other seemingly innocuous data, such as images or audio files, aiming to hide the very existence of the message. Unlike obfuscation, which protects code from analysis, steganography protects communication by embedding secrets in carriers, ensuring data confidentiality through concealment rather than complexity.
Use Cases of Coded Obfuscation in Software Security
Coded obfuscation is primarily used in software security to protect intellectual property and prevent reverse engineering by making code difficult to understand and analyze. It enables developers to safeguard sensitive algorithms, license verification processes, and cryptographic keys from attackers attempting to exploit software vulnerabilities. This technique enhances the resilience of software against tampering, piracy, and unauthorized modifications, ensuring data integrity and secure execution environments.
Applications of Steganography in Data Protection
Steganography is widely applied in data protection by embedding sensitive information within innocuous files, such as images, audio, or video, to prevent detection during transmission. This technique enhances confidentiality by concealing the existence of the message rather than just encrypting its content, making it a valuable tool against cyber espionage and data interception. Its applications include watermarking digital media for copyright protection and securely transmitting authentication credentials in covert communication channels.
Advantages and Drawbacks of Coded Obfuscation
Coded obfuscation enhances cybersecurity by making code difficult to reverse-engineer, protecting intellectual property and deterring unauthorized tampering. Its advantages include robust protection against static analysis and code theft, while drawbacks encompass increased complexity, performance overhead, and potential compatibility issues. Compared to steganography, coded obfuscation directly secures the functional code rather than hiding information within other data, but it may be less effective against sophisticated dynamic analysis techniques.
Pros and Cons of Steganography in Cybersecurity
Steganography enhances cybersecurity by concealing sensitive data within innocuous files, making detection by unauthorized users difficult and improving covert communication. However, its reliance on specific cover media and potential susceptibility to steganalysis tools limit its effectiveness against advanced attacks. Despite low visibility advantages, steganography does not inherently provide encryption, necessitating additional security measures to protect the embedded information from extraction or manipulation.
Detection and Mitigation Strategies
Coded obfuscation complicates static and dynamic analysis by transforming code structure while retaining functionality, demanding advanced signature-less detection techniques like behavioral analysis and heuristic scanning to identify malicious patterns. Steganography conceals data within innocuous files, requiring forensic methods such as anomaly-based detection and statistical image or audio analysis to uncover hidden payloads. Mitigation strategies involve layered security frameworks combining machine learning models with real-time monitoring to enhance detection accuracy and automated response systems for faster containment.
Future Trends: Obfuscation vs Steganography in Cyber Defense
Future trends in cyber defense reveal increasing sophistication in coded obfuscation techniques, leveraging artificial intelligence to create adaptive and polymorphic code that resists reverse engineering. Steganography is evolving with advanced algorithms embedding data within multimedia files and network protocols, enhancing covert communication and data exfiltration detection challenges. Emerging defenses will integrate machine learning to identify subtle anomalies, balancing the battle between invisibility of steganographic payloads and complexity of obfuscation methods.
coded obfuscation vs steganography Infographic
 techiny.com
techiny.com