Plaintext refers to readable data or messages before encryption, making it vulnerable to unauthorized access. Ciphertext is the encoded version of plaintext generated by encryption algorithms, ensuring data confidentiality during transmission or storage. Effective cybersecurity relies on transforming plaintext into ciphertext to protect sensitive information from cyber threats.
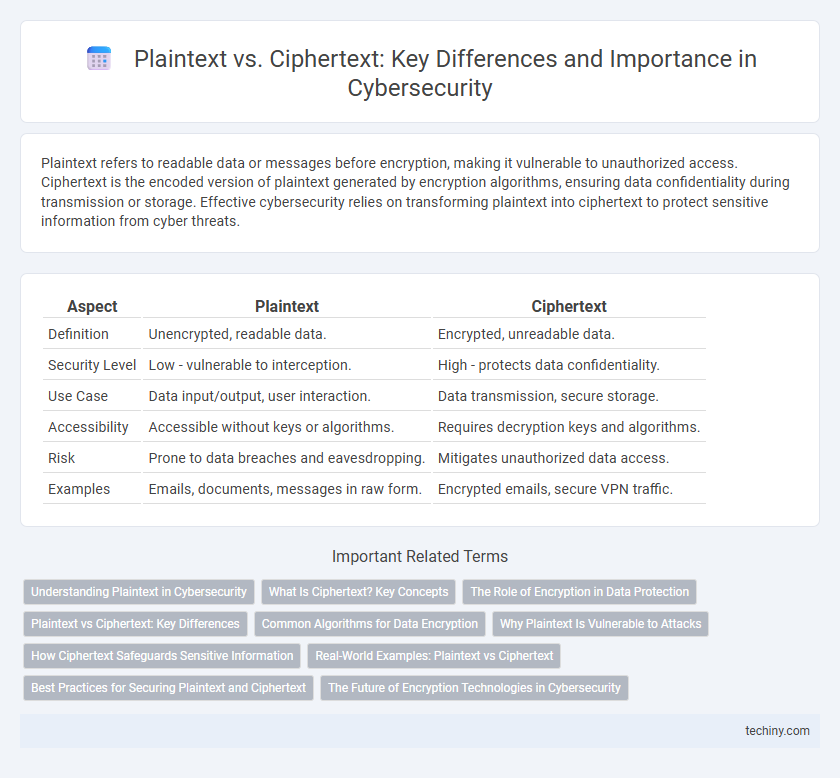
Table of Comparison
| Aspect | Plaintext | Ciphertext |
|---|---|---|
| Definition | Unencrypted, readable data. | Encrypted, unreadable data. |
| Security Level | Low - vulnerable to interception. | High - protects data confidentiality. |
| Use Case | Data input/output, user interaction. | Data transmission, secure storage. |
| Accessibility | Accessible without keys or algorithms. | Requires decryption keys and algorithms. |
| Risk | Prone to data breaches and eavesdropping. | Mitigates unauthorized data access. |
| Examples | Emails, documents, messages in raw form. | Encrypted emails, secure VPN traffic. |
Understanding Plaintext in Cybersecurity
Plaintext in cybersecurity refers to data that is readable and unencrypted, making it vulnerable to interception and unauthorized access during transmission or storage. Protecting plaintext requires implementing robust encryption methods to convert it into ciphertext, ensuring confidentiality and data integrity. Understanding the risks associated with plaintext exposure is critical for developing effective security protocols and safeguarding sensitive information.
What Is Ciphertext? Key Concepts
Ciphertext is encrypted data transformed from plaintext using cryptographic algorithms to prevent unauthorized access. It appears as a scrambled, unintelligible string of characters that can only be deciphered back into readable plaintext with the correct decryption key. Key concepts include encryption, decryption, cryptographic keys, and algorithms such as AES or RSA that ensure data confidentiality and secure communication.
The Role of Encryption in Data Protection
Encryption transforms plaintext, the readable data, into ciphertext, an encoded format that protects sensitive information from unauthorized access. This process is crucial in cybersecurity as it ensures data confidentiality and integrity during storage and transmission. Strong encryption algorithms create ciphertext that can only be decrypted with the correct cryptographic key, effectively safeguarding data against cyber threats and breaches.
Plaintext vs Ciphertext: Key Differences
Plaintext refers to readable data or information before encryption, easily understood by humans or computers without any special decryption method. Ciphertext is the scrambled, unreadable form of plaintext generated by encryption algorithms to secure data from unauthorized access. The key differences between plaintext and ciphertext lie in data visibility, with plaintext being openly accessible and ciphertext requiring cryptographic keys for decryption to restore original content.
Common Algorithms for Data Encryption
Common algorithms for data encryption convert plaintext into ciphertext using mathematical transformations designed to ensure confidentiality and integrity. Symmetric key algorithms like AES (Advanced Encryption Standard) and DES (Data Encryption Standard) use the same secret key for both encryption and decryption, providing efficient performance for large data volumes. Asymmetric algorithms such as RSA and ECC (Elliptic Curve Cryptography) employ public and private keys, enabling secure key exchange and digital signatures in complex cybersecurity environments.
Why Plaintext Is Vulnerable to Attacks
Plaintext is vulnerable to attacks because it is data in its original, readable form, which can be easily intercepted and exploited by unauthorized parties. Without encryption, sensitive information such as passwords, personal details, and confidential communications remain exposed during transmission and storage. Cybercriminals can capture plaintext data through methods like packet sniffing, man-in-the-middle attacks, and database breaches, leading to identity theft, data breaches, and financial loss.
How Ciphertext Safeguards Sensitive Information
Ciphertext obscures sensitive information by transforming plaintext into an unreadable format through encryption algorithms, rendering data unintelligible without the correct decryption key. This process prevents unauthorized access, ensuring data confidentiality during transmission and storage, especially in environments vulnerable to cyber attacks. The robustness of ciphertext depends on encryption strength and key management, critical factors in safeguarding personal, financial, and organizational data from breaches and espionage.
Real-World Examples: Plaintext vs Ciphertext
In cybersecurity, plaintext refers to readable data such as emails or financial records before encryption, while ciphertext is the scrambled output that protects this information from unauthorized access. For example, when a user sends a message via encrypted messaging apps like Signal or WhatsApp, the original text (plaintext) is transformed into ciphertext during transmission, ensuring confidentiality. Real-world breaches, such as the 2017 Equifax hack, highlight the risks of exposed plaintext data, emphasizing the critical role of encryption in safeguarding sensitive information.
Best Practices for Securing Plaintext and Ciphertext
Storing plaintext data demands strict access controls and encryption at rest to prevent unauthorized exposure, while ciphertext must be protected through robust key management and secure transmission protocols like TLS. Regularly updating cryptographic algorithms and using multi-factor authentication further fortify defenses against breaches targeting both plaintext and ciphertext. Implementing data loss prevention (DLP) tools and continuous monitoring ensures early detection of attempts to access plaintext or ciphertext improperly, enhancing overall cybersecurity resilience.
The Future of Encryption Technologies in Cybersecurity
Advancements in encryption technologies are rapidly transforming cybersecurity by enhancing the protection of plaintext data through more sophisticated ciphertext algorithms. Quantum-resistant encryption methods are emerging to secure sensitive information against the computational power of quantum computers. The integration of machine learning with encryption ensures dynamic adaptation to evolving cyber threats, promising a resilient future for data confidentiality and integrity.
Plaintext vs Ciphertext Infographic
 techiny.com
techiny.com