A vulnerability is a weakness or flaw in a system, software, or network that can be targeted by cyberattacks. An exploit is a specific piece of code or technique used by attackers to take advantage of a vulnerability and gain unauthorized access or cause damage. Effective cybersecurity strategies involve identifying vulnerabilities and mitigating exploits through patches, updates, and robust defense mechanisms.
Table of Comparison
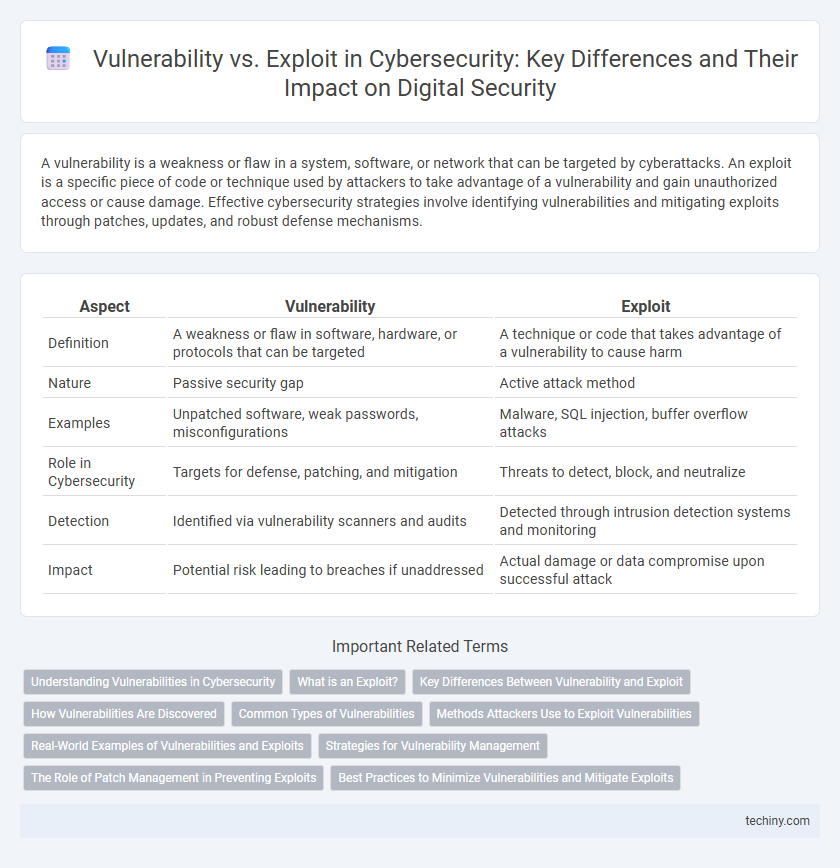
| Aspect | Vulnerability | Exploit |
|---|---|---|
| Definition | A weakness or flaw in software, hardware, or protocols that can be targeted | A technique or code that takes advantage of a vulnerability to cause harm |
| Nature | Passive security gap | Active attack method |
| Examples | Unpatched software, weak passwords, misconfigurations | Malware, SQL injection, buffer overflow attacks |
| Role in Cybersecurity | Targets for defense, patching, and mitigation | Threats to detect, block, and neutralize |
| Detection | Identified via vulnerability scanners and audits | Detected through intrusion detection systems and monitoring |
| Impact | Potential risk leading to breaches if unaddressed | Actual damage or data compromise upon successful attack |
Understanding Vulnerabilities in Cybersecurity
Vulnerabilities in cybersecurity represent weaknesses or flaws within software, hardware, or network systems that can be exploited by malicious actors to gain unauthorized access or cause damage. These security gaps often stem from coding errors, misconfigurations, or inadequate security practices, making them prime targets for cyberattacks. Understanding the nature and scope of vulnerabilities is crucial for effective risk assessment and the implementation of proactive defense mechanisms against potential exploits.
What is an Exploit?
An exploit is a specialized piece of code or technique that takes advantage of a software vulnerability to gain unauthorized access or perform malicious actions on a system. Exploits target specific security flaws, enabling attackers to bypass protections, execute arbitrary code, or escalate privileges. Understanding exploits is crucial for developing effective cybersecurity defenses and patching vulnerabilities before they are weaponized.
Key Differences Between Vulnerability and Exploit
A vulnerability is a flaw or weakness in a system, application, or network that can be targeted by cyber attackers, while an exploit is the specific method or code used to take advantage of that vulnerability. Vulnerabilities exist independently and may remain unexploited until an attacker discovers or develops an exploit to leverage them. Understanding the distinction helps cybersecurity professionals prioritize patching vulnerabilities and defend against active exploitation attempts.
How Vulnerabilities Are Discovered
Security researchers utilize techniques such as penetration testing, code review, and automated scanning tools to identify vulnerabilities within software and systems. Bug bounty programs encourage external experts to report weaknesses responsibly, enhancing the discovery process. Vulnerabilities can also be uncovered through analysis of past security incidents, reverse engineering, and monitoring public disclosures in cybersecurity databases like CVE.
Common Types of Vulnerabilities
Common types of cybersecurity vulnerabilities include software bugs, misconfigurations, and weak authentication mechanisms, which create entry points for attackers. Buffer overflows, injection flaws, and insecure deserialization are among the prevalent vulnerabilities exploited in attacks. Understanding these vulnerabilities is essential for developing effective defensive strategies against exploits that leverage these weaknesses.
Methods Attackers Use to Exploit Vulnerabilities
Attackers utilize various methods to exploit vulnerabilities, including buffer overflow attacks, SQL injection, and cross-site scripting (XSS). These techniques manipulate software weaknesses to gain unauthorized access, execute arbitrary code, or extract sensitive data. Understanding these tactics enables cybersecurity professionals to implement robust defenses such as input validation, patch management, and intrusion detection systems.
Real-World Examples of Vulnerabilities and Exploits
The CVE-2017-0144 vulnerability in Microsoft Windows, known as EternalBlue, allowed attackers to exploit a flaw in the SMB protocol, leading to the widespread WannaCry ransomware attack in 2017 that affected over 200,000 computers worldwide. Another example is the Heartbleed bug (CVE-2014-0160) in OpenSSL, which exposed sensitive data by exploiting improper bounds checking in the heartbeat extension, allowing attackers to steal encryption keys and user information. These real-world cases demonstrate how identifying vulnerabilities is critical to defending against exploits that can cause massive data breaches and operational disruptions.
Strategies for Vulnerability Management
Effective vulnerability management hinges on identifying security weaknesses before they can be exploited by attackers, utilizing continuous scanning and risk prioritization based on asset criticality. Implementing patch management and configuration controls reduces exposure, while threat intelligence integration enables proactive defenses against known exploits. Regular penetration testing and real-time monitoring ensure vulnerabilities are addressed swiftly, minimizing potential breach impacts in cybersecurity infrastructures.
The Role of Patch Management in Preventing Exploits
Patch management is critical in cybersecurity for addressing vulnerabilities by regularly updating software to fix security flaws before attackers can exploit them. Effective patch deployment reduces the attack surface by closing known vulnerabilities, thereby preventing exploit techniques from compromising systems. Organizations that prioritize timely patching greatly enhance their defense against malware, ransomware, and unauthorized access attempts.
Best Practices to Minimize Vulnerabilities and Mitigate Exploits
Regularly updating software and applying security patches are essential best practices to minimize vulnerabilities in cybersecurity. Implementing robust access controls and continuous monitoring helps detect and mitigate exploits before they cause significant damage. Employing multi-layered defense strategies, including intrusion detection systems and endpoint protection, further strengthens an organization's security posture against exploitation attempts.
Vulnerability vs Exploit Infographic
 techiny.com
techiny.com