Data at rest refers to information stored on physical or digital media, such as hard drives or cloud storage, requiring robust encryption and access controls to prevent unauthorized access. Data in transit is data actively moving across networks, necessitating secure transmission protocols like TLS or VPNs to protect against interception and eavesdropping. Understanding the distinct security needs of data at rest versus data in transit is crucial for implementing comprehensive cybersecurity strategies.
Table of Comparison
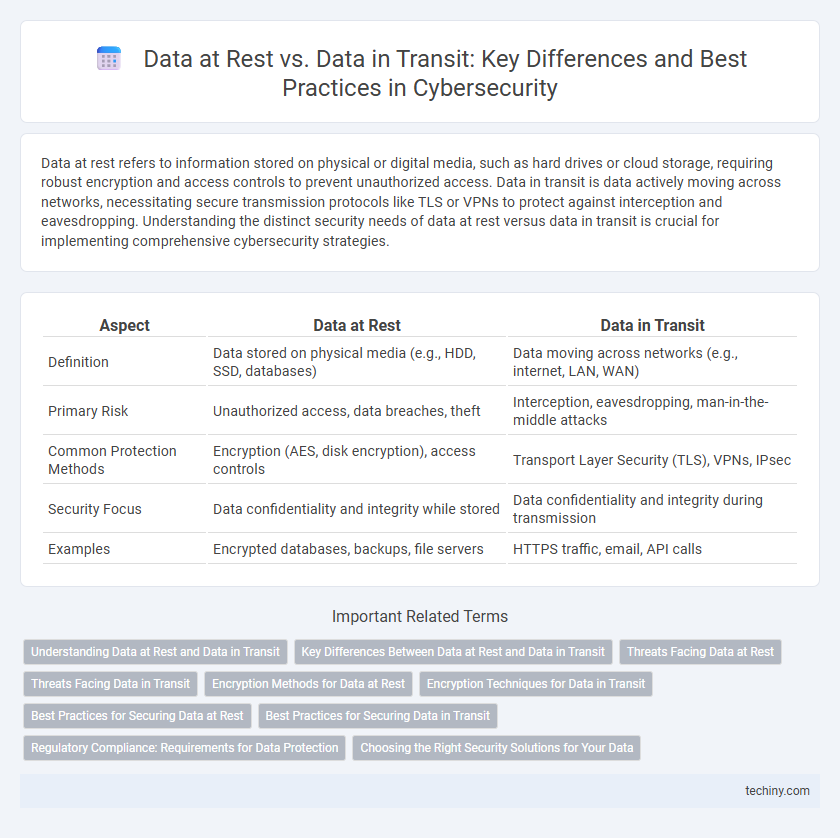
| Aspect | Data at Rest | Data in Transit |
|---|---|---|
| Definition | Data stored on physical media (e.g., HDD, SSD, databases) | Data moving across networks (e.g., internet, LAN, WAN) |
| Primary Risk | Unauthorized access, data breaches, theft | Interception, eavesdropping, man-in-the-middle attacks |
| Common Protection Methods | Encryption (AES, disk encryption), access controls | Transport Layer Security (TLS), VPNs, IPsec |
| Security Focus | Data confidentiality and integrity while stored | Data confidentiality and integrity during transmission |
| Examples | Encrypted databases, backups, file servers | HTTPS traffic, email, API calls |
Understanding Data at Rest and Data in Transit
Data at rest refers to information stored on physical or digital media, such as hard drives, databases, or cloud storage, requiring encryption and strong access controls to prevent unauthorized access. Data in transit involves data actively moving across networks, including emails, file transfers, and web traffic, necessitating secure communication protocols like TLS/SSL to protect against interception and tampering. Effective cybersecurity strategies must address both data at rest and data in transit to ensure comprehensive data protection across all storage and transmission points.
Key Differences Between Data at Rest and Data in Transit
Data at rest refers to information stored on physical or digital media, such as databases, hard drives, or cloud storage, while data in transit pertains to data actively moving across networks, including emails, file transfers, or online transactions. A primary difference lies in the security measures required: data at rest demands robust encryption and access controls to protect against unauthorized access, whereas data in transit requires secure protocols like TLS or VPN to prevent interception and tampering during transmission. Understanding these distinctions is crucial for implementing comprehensive cybersecurity strategies that safeguard sensitive information both when stored and while being transmitted.
Threats Facing Data at Rest
Data at rest faces significant cybersecurity threats including unauthorized access, malware infections, and physical theft of storage devices that can lead to data breaches or loss. Attackers often exploit weak encryption or poor access controls, making sensitive information vulnerable to exposure or manipulation. Protecting data at rest requires robust encryption standards, strict access management, and continuous monitoring for suspicious activities to mitigate risks effectively.
Threats Facing Data in Transit
Data in transit is vulnerable to threats such as interception, man-in-the-middle attacks, and eavesdropping, which can lead to unauthorized access and data breaches. Attackers exploit network vulnerabilities by capturing data packets during transmission, compromising the confidentiality and integrity of sensitive information. Implementing robust encryption protocols like TLS and VPNs is essential to safeguard data in transit from cyber threats.
Encryption Methods for Data at Rest
Encryption methods for data at rest primarily include Advanced Encryption Standard (AES) with 256-bit keys, which offers robust protection by converting stored data into unreadable ciphertext. Disk encryption tools such as BitLocker and FileVault use AES to secure entire drives, preventing unauthorized access even if physical storage devices are compromised. Hardware Security Modules (HSMs) and Trusted Platform Modules (TPMs) enhance encryption key management, safeguarding cryptographic keys from exposure and ensuring the integrity of data at rest.
Encryption Techniques for Data in Transit
Encryption techniques for data in transit primarily rely on protocols such as TLS (Transport Layer Security) and SSL (Secure Sockets Layer) to ensure data confidentiality and integrity while being transmitted across networks. Advanced methods like end-to-end encryption (E2EE) protect data from interception by encrypting it at the source and only decrypting it at the destination, preventing unauthorized access during transmission. These encryption mechanisms use symmetric and asymmetric cryptography to secure communications over public and private channels, safeguarding sensitive information against cyber threats like man-in-the-middle attacks.
Best Practices for Securing Data at Rest
Encrypting data at rest using robust algorithms such as AES-256 ensures sensitive information remains protected even if storage media is compromised. Implementing strict access controls and multi-factor authentication limits unauthorized access to stored data, enhancing security posture. Regularly updating and patching storage systems prevents exploitation of vulnerabilities that could expose data at rest.
Best Practices for Securing Data in Transit
Encrypting data in transit using strong protocols such as TLS and IPSec ensures confidentiality and integrity against interception and tampering. Implementing robust authentication mechanisms like mutual TLS or VPNs restricts access to authorized parties, preventing unauthorized data access during transmission. Continuous monitoring and intrusion detection systems enhance security by identifying and mitigating anomalies or attacks targeting data in transit.
Regulatory Compliance: Requirements for Data Protection
Regulatory compliance mandates distinct safeguards for data at rest and data in transit to ensure comprehensive protection. Data at rest requires encryption, access controls, and monitoring to prevent unauthorized access within storage systems, aligning with standards such as GDPR and HIPAA. Data in transit must employ secure transmission protocols like TLS and VPNs to protect sensitive information from interception or tampering during transfer, fulfilling requirements set by frameworks like PCI DSS and NIST.
Choosing the Right Security Solutions for Your Data
Choosing the right security solutions for data at rest involves implementing strong encryption standards such as AES-256 and robust access controls like multi-factor authentication and role-based permissions. For data in transit, securing communication channels with protocols such as TLS 1.3 or IPsec ensures data integrity and confidentiality against interception or man-in-the-middle attacks. Combining endpoint security tools and network monitoring enhances protection by addressing vulnerabilities specific to both stored and transmitted data in comprehensive cybersecurity strategies.
Data at Rest vs Data in Transit Infographic
 techiny.com
techiny.com