An exploit targets a vulnerability within a system or application to gain unauthorized access or cause unintended behavior. The payload is the malicious code delivered through the exploit, designed to execute a specific harmful function such as data theft or system damage. Understanding the distinction between exploit and payload is crucial for developing effective cybersecurity defenses.
Table of Comparison
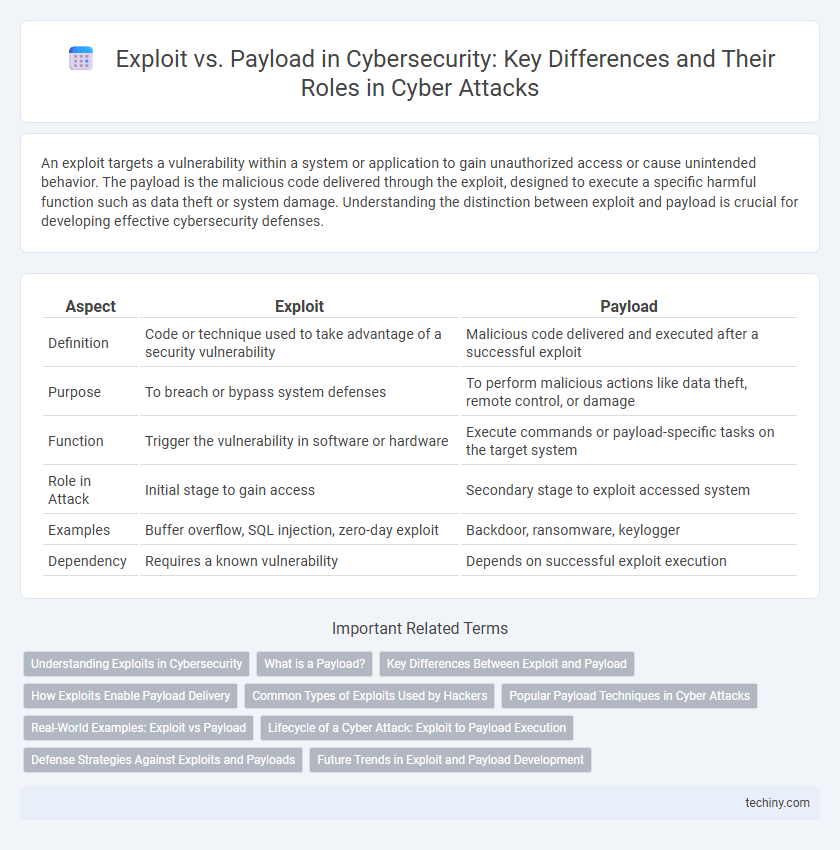
| Aspect | Exploit | Payload |
|---|---|---|
| Definition | Code or technique used to take advantage of a security vulnerability | Malicious code delivered and executed after a successful exploit |
| Purpose | To breach or bypass system defenses | To perform malicious actions like data theft, remote control, or damage |
| Function | Trigger the vulnerability in software or hardware | Execute commands or payload-specific tasks on the target system |
| Role in Attack | Initial stage to gain access | Secondary stage to exploit accessed system |
| Examples | Buffer overflow, SQL injection, zero-day exploit | Backdoor, ransomware, keylogger |
| Dependency | Requires a known vulnerability | Depends on successful exploit execution |
Understanding Exploits in Cybersecurity
Exploits in cybersecurity refer to code or techniques designed to take advantage of vulnerabilities within software or systems, enabling unauthorized actions such as privilege escalation or code execution. These exploits target security flaws like buffer overflows, injection vulnerabilities, or authentication weaknesses to gain initial access. Understanding exploits is critical for developing effective defenses, including patch management, intrusion detection, and vulnerability assessments.
What is a Payload?
A payload in cybersecurity refers to the part of malware or a cyberattack code designed to perform a malicious action on a target system, such as data theft, system damage, or unauthorized access. Unlike an exploit, which is used to identify and take advantage of a vulnerability, the payload delivers the harmful effect once the exploit has successfully breached security defenses. Effective cybersecurity measures focus on detecting and neutralizing payloads to prevent damage after an exploit occurs.
Key Differences Between Exploit and Payload
An exploit is a piece of code or technique that takes advantage of a vulnerability or security flaw in a system to gain unauthorized access or control. A payload is the actual malicious code delivered and executed on the target system after a successful exploit, often designed to perform specific actions like stealing data or creating backdoors. Key differences lie in their roles: exploits serve as the delivery mechanism to breach defenses, while payloads execute the attacker's intent once inside the system.
How Exploits Enable Payload Delivery
Exploits take advantage of software vulnerabilities to breach systems and bypass security measures, creating a pathway for payloads to be executed. By manipulating weaknesses in code, exploits enable payloads--such as malware, ransomware, or remote access tools--to be delivered and triggered on the target device. This chain of attack leverages exploit techniques to ensure payload installation and maximize the impact of the cybersecurity breach.
Common Types of Exploits Used by Hackers
Common types of exploits used by hackers include buffer overflow, SQL injection, cross-site scripting (XSS), and privilege escalation attacks. These exploits target vulnerabilities in software or web applications to gain unauthorized access or execute malicious code. Understanding these exploit techniques is essential for developing effective cybersecurity defenses and mitigating potential threats.
Popular Payload Techniques in Cyber Attacks
Popular payload techniques in cyber attacks include remote code execution, where attackers inject malicious code to take control of a system, and ransomware, which encrypts files and demands payment for decryption keys. Another common payload method is the deployment of backdoors, enabling unauthorized persistent access to compromised networks. These payloads often follow exploits that leverage vulnerabilities in software or systems to deliver the malicious code effectively.
Real-World Examples: Exploit vs Payload
Exploits like the EternalBlue vulnerability in Windows systems enable attackers to gain unauthorized access by leveraging software flaws, while payloads such as ransomware encrypt user data to extort victims after the exploit's success. The WannaCry attack demonstrated how the EternalBlue exploit delivered a ransomware payload, causing widespread disruption across global networks. Real-world incidents highlight the critical distinction between exploits as entry mechanisms and payloads as the malicious actions executed post-exploitation.
Lifecycle of a Cyber Attack: Exploit to Payload Execution
An exploit leverages a specific software vulnerability to gain unauthorized access during the initial phase of a cyber attack, effectively breaching system defenses. Once the exploit successfully executes, the payload is delivered, which can consist of malware or malicious code designed to achieve the attacker's objectives such as data exfiltration, system control, or disruption. The transition from exploit to payload execution marks a critical point in the attack lifecycle, transforming initial access into persistent security threats that require immediate detection and response.
Defense Strategies Against Exploits and Payloads
Effective defense strategies against exploits involve timely patch management and robust input validation to prevent attackers from leveraging vulnerabilities. Payload mitigation requires advanced detection systems such as intrusion prevention and endpoint protection to identify and neutralize malicious code execution. Integrating threat intelligence and behavioral analytics improves the ability to recognize and respond to evolving exploit and payload techniques.
Future Trends in Exploit and Payload Development
Emerging trends in exploit development emphasize the use of artificial intelligence to create more adaptive and evasive techniques that bypass traditional detection methods. Modern payloads increasingly integrate modular architectures, allowing dynamic functionality updates and seamless integration with advanced command-and-control infrastructures. The convergence of machine learning and automation is accelerating the evolution of exploits and payloads, driving the need for proactive defense strategies leveraging behavioral analytics and threat intelligence.
Exploit vs Payload Infographic
 techiny.com
techiny.com