Man-in-the-Middle (MITM) attacks involve an adversary intercepting and potentially altering communication between two parties without their knowledge, compromising confidentiality and integrity. Replay attacks capture valid data transmissions and retransmit them to impersonate a legitimate user or gain unauthorized access, exploiting the lack of freshness in authentication protocols. Both attack types highlight the critical need for strong encryption, authentication mechanisms, and timestamping to secure network communications effectively.
Table of Comparison
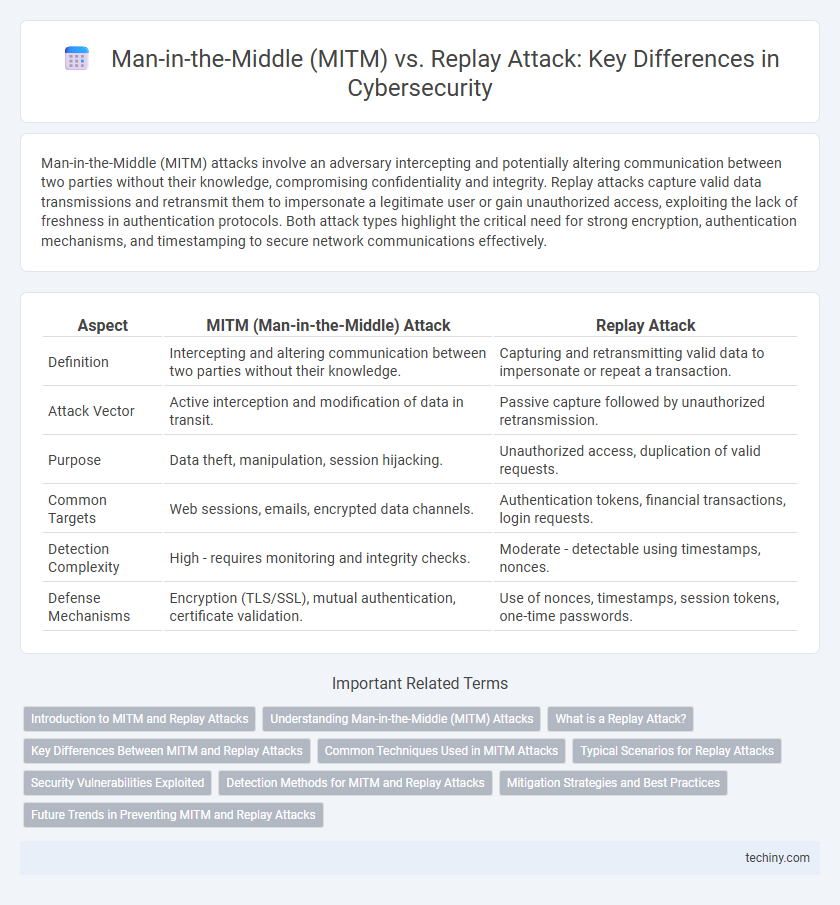
| Aspect | MITM (Man-in-the-Middle) Attack | Replay Attack |
|---|---|---|
| Definition | Intercepting and altering communication between two parties without their knowledge. | Capturing and retransmitting valid data to impersonate or repeat a transaction. |
| Attack Vector | Active interception and modification of data in transit. | Passive capture followed by unauthorized retransmission. |
| Purpose | Data theft, manipulation, session hijacking. | Unauthorized access, duplication of valid requests. |
| Common Targets | Web sessions, emails, encrypted data channels. | Authentication tokens, financial transactions, login requests. |
| Detection Complexity | High - requires monitoring and integrity checks. | Moderate - detectable using timestamps, nonces. |
| Defense Mechanisms | Encryption (TLS/SSL), mutual authentication, certificate validation. | Use of nonces, timestamps, session tokens, one-time passwords. |
Introduction to MITM and Replay Attacks
Man-in-the-Middle (MITM) attacks involve an attacker secretly intercepting and possibly altering communication between two parties without their knowledge. Replay attacks occur when an adversary captures valid data transmissions and fraudulently retransmits them to deceive the recipient into unauthorized actions. Both attacks exploit vulnerabilities in communication channels, but MITM focuses on active intervention, while replay attacks rely on passive data reuse.
Understanding Man-in-the-Middle (MITM) Attacks
Man-in-the-Middle (MITM) attacks involve an attacker secretly intercepting and potentially altering communication between two parties without their knowledge, posing a significant threat to confidentiality and data integrity in cybersecurity. Unlike replay attacks, which simply capture and resend valid data transmissions to deceive systems, MITM attacks actively manipulate the communication channel to eavesdrop or inject malicious content in real-time. Effective countermeasures against MITM attacks include strong encryption protocols, mutual authentication, and continuous monitoring of network traffic for anomalies.
What is a Replay Attack?
A replay attack involves intercepting and retransmitting valid data transmissions to deceive a system into unauthorized actions, exploiting the lack of freshness or timestamp verification. Unlike a Man-in-the-Middle (MITM) attack, which actively alters or injects data during communication, replay attacks solely replicate previously captured data without modification. Effective defenses include implementing nonces, timestamps, and session tokens to ensure message uniqueness and prevent unauthorized retransmission.
Key Differences Between MITM and Replay Attacks
Man-in-the-Middle (MITM) attacks involve an attacker intercepting and actively altering communication between two parties, while Replay Attacks consist of capturing and retransmitting valid data to gain unauthorized access without altering the original message. MITM attacks require real-time interception and manipulation, whereas Replay Attacks exploit previously recorded transmissions to bypass authentication. The key difference lies in MITM's dynamic interaction versus Replay's passive reuse of intercepted data.
Common Techniques Used in MITM Attacks
MITM attacks commonly use techniques such as IP spoofing, DNS spoofing, and Wi-Fi eavesdropping to intercept and manipulate communications between two parties. Attackers often employ session hijacking and SSL stripping to gain unauthorized access to sensitive data without detection. These methods exploit vulnerabilities in network protocols and encryption to compromise the integrity and confidentiality of transmitted information.
Typical Scenarios for Replay Attacks
Replay attacks typically occur in authentication systems where intercepted credentials or tokens are resent to gain unauthorized access, such as in wireless networks and online banking platforms. Attackers exploit vulnerable communication protocols lacking proper nonce or timestamp mechanisms, enabling them to duplicate valid data transmissions. Common scenarios include capturing login requests in public Wi-Fi environments and retransmitting financial transaction messages to fraudulently authorize payments.
Security Vulnerabilities Exploited
Man-in-the-Middle (MITM) attacks exploit vulnerabilities in communication channels by intercepting and potentially altering data transmitted between two parties, often targeting insecure Wi-Fi networks or unencrypted protocols like HTTP. Replay attacks exploit weaknesses in authentication protocols by capturing valid data transmissions and retransmitting them to gain unauthorized access, commonly targeting systems without nonce or timestamp validation. Both attacks leverage flaws in cryptographic protocol implementations, emphasizing the critical need for strong encryption, mutual authentication, and integrity checks to mitigate these security vulnerabilities.
Detection Methods for MITM and Replay Attacks
Detection methods for Man-in-the-Middle (MITM) attacks primarily involve monitoring network traffic for anomalies such as unexpected certificate changes, unauthorized ARP cache modifications, or deviations in SSL/TLS handshakes. Replay attacks are identified through techniques like timestamp verification, nonce utilization, and sequence number tracking to detect duplicated or out-of-order packets. Network security tools incorporating intrusion detection systems (IDS) with heuristic algorithms and anomaly detection models enhance real-time identification of both MITM and replay attack patterns.
Mitigation Strategies and Best Practices
Mitigation strategies for Man-in-the-Middle (MITM) attacks include implementing strong encryption protocols such as TLS, enforcing certificate pinning, and using multi-factor authentication to verify user identities. Replay attacks can be countered by incorporating nonces, timestamps, and sequence numbers in communication exchanges to ensure message freshness and prevent reuse. Both attack types require continuous network monitoring, timely software patching, and educating users to recognize suspicious activities as essential best practices.
Future Trends in Preventing MITM and Replay Attacks
Advanced cryptographic protocols and machine learning algorithms are shaping the future of preventing Man-in-the-Middle (MITM) and Replay Attacks by enhancing real-time threat detection and authentication processes. Zero Trust Architecture (ZTA) and quantum-resistant encryption methods are gaining traction as robust defenses against evolving attack vectors. Continuous network monitoring combined with AI-driven anomaly detection significantly reduces the window of vulnerability in both MITM and replay attack scenarios.
MITM (Man-in-the-Middle) vs Replay Attack Infographic
 techiny.com
techiny.com