Packet sniffing involves capturing and analyzing network traffic to monitor data flow and identify potential threats, while packet injection refers to the deliberate insertion of forged packets into a network to manipulate or disrupt communication. Understanding the distinctions between these techniques is crucial for implementing robust cybersecurity measures, as sniffing is primarily passive and detection-oriented, whereas injection is an active attack method used to bypass security controls or propagate malicious payloads. Both require specialized tools and expertise, but their prevention and mitigation strategies vary significantly depending on the network environment and security protocols in place.
Table of Comparison
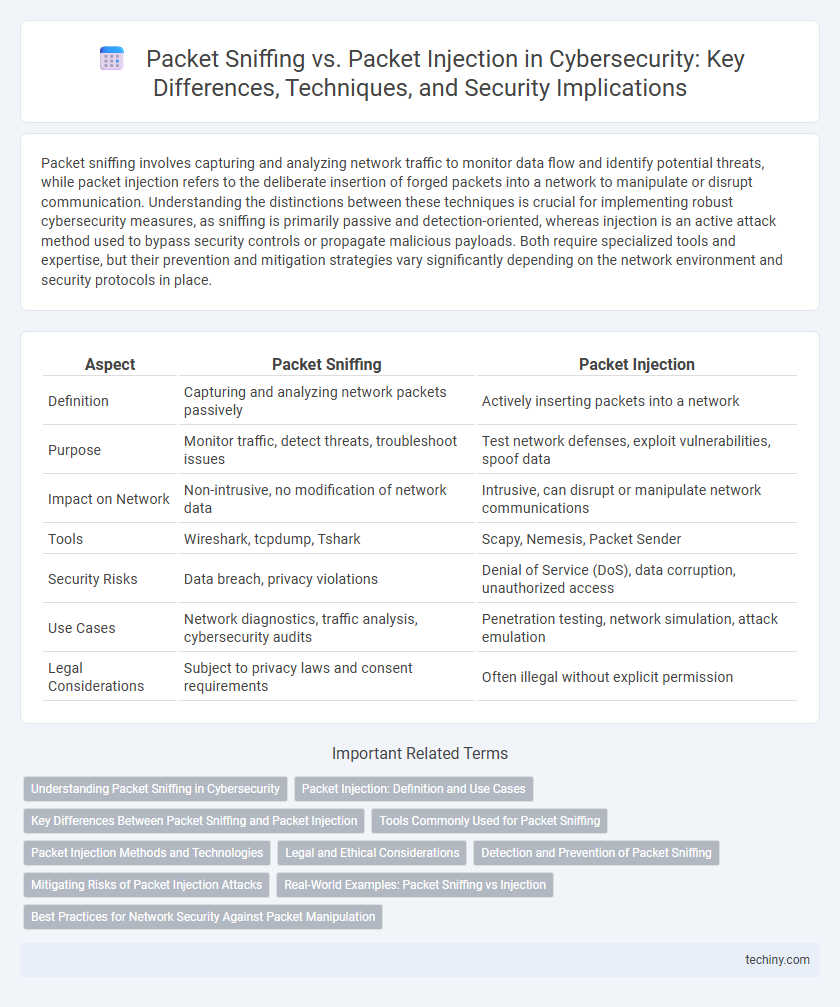
| Aspect | Packet Sniffing | Packet Injection |
|---|---|---|
| Definition | Capturing and analyzing network packets passively | Actively inserting packets into a network |
| Purpose | Monitor traffic, detect threats, troubleshoot issues | Test network defenses, exploit vulnerabilities, spoof data |
| Impact on Network | Non-intrusive, no modification of network data | Intrusive, can disrupt or manipulate network communications |
| Tools | Wireshark, tcpdump, Tshark | Scapy, Nemesis, Packet Sender |
| Security Risks | Data breach, privacy violations | Denial of Service (DoS), data corruption, unauthorized access |
| Use Cases | Network diagnostics, traffic analysis, cybersecurity audits | Penetration testing, network simulation, attack emulation |
| Legal Considerations | Subject to privacy laws and consent requirements | Often illegal without explicit permission |
Understanding Packet Sniffing in Cybersecurity
Packet sniffing in cybersecurity involves capturing and analyzing network packets to monitor data flow and detect unauthorized access or anomalies. This technique allows cybersecurity professionals to identify malicious activities like data breaches, intrusion attempts, and malware communication by examining packet headers and payloads. Packet sniffing tools, such as Wireshark and tcpdump, are essential for network traffic analysis, vulnerability assessment, and enhancing overall security posture.
Packet Injection: Definition and Use Cases
Packet injection involves deliberately inserting forged packets into a network to manipulate traffic, test defenses, or exploit vulnerabilities. It is primarily used in penetration testing, network troubleshooting, and cyberattack scenarios such as man-in-the-middle attacks and denial-of-service. Understanding packet injection helps cybersecurity professionals identify and mitigate risks linked to unauthorized data alteration and network breach attempts.
Key Differences Between Packet Sniffing and Packet Injection
Packet sniffing involves capturing and analyzing network traffic passively to monitor data packets without altering them, primarily used for network diagnostics and security monitoring. Packet injection actively inserts or modifies packets within a network, enabling testing of network resilience or conducting attacks such as session hijacking and man-in-the-middle exploits. The key difference lies in packet sniffing's passive observation role versus packet injection's active manipulation of network communication.
Tools Commonly Used for Packet Sniffing
Packet sniffing tools like Wireshark, tcpdump, and Microsoft Network Monitor are commonly used to capture and analyze network traffic for cybersecurity purposes. These tools enable security professionals to detect anomalies, troubleshoot network issues, and monitor data packets in real time. Packet injection, by contrast, involves actively inserting packets into a network, often using specialized tools such as Scapy or Cain & Abel, which serve different roles in penetration testing and network analysis.
Packet Injection Methods and Technologies
Packet injection techniques involve inserting crafted packets into a network to manipulate traffic, often used for penetration testing or exploiting vulnerabilities. Common technologies include tools like Scapy, Nemesis, and specialized hardware such as Wi-Fi Pineapple for wireless packet injection. These methods enable attackers or security professionals to simulate attacks, test firewall rules, or perform man-in-the-middle attacks by injecting malicious or spoofed packets into live network streams.
Legal and Ethical Considerations
Packet sniffing involves capturing network data packets to monitor and analyze traffic, typically requiring explicit authorization to avoid violating privacy laws such as the Computer Fraud and Abuse Act (CFAA) in the United States or the General Data Protection Regulation (GDPR) in Europe. Packet injection, which entails inserting crafted packets into a network to manipulate communication, carries higher legal risks and ethical concerns due to potential unauthorized network disruption and data tampering, often classified as malicious hacking under cybersecurity regulations. Ethical cybersecurity practitioners must obtain proper consent and adhere to strict usage policies to ensure compliance with laws governing data interception and network integrity.
Detection and Prevention of Packet Sniffing
Packet sniffing detection involves monitoring network traffic for unusual patterns or unauthorized devices using tools like intrusion detection systems (IDS) and network analyzers. Preventing packet sniffing requires implementing strong encryption protocols such as SSL/TLS, employing secure network architectures with segmentation, and enforcing strict access controls and authentication mechanisms. Regular network audits and anomaly detection algorithms enhance early identification of sniffing activities, reducing the risk of sensitive data exposure.
Mitigating Risks of Packet Injection Attacks
Mitigating risks of packet injection attacks involves deploying advanced intrusion detection systems (IDS) that monitor network traffic for abnormal packet patterns and signatures. Implementing strong authentication protocols like 802.1X and encrypting data with TLS or IPsec significantly reduce the attack surface by preventing unauthorized packet transmission. Regular network segmentation and updated firewall rules further isolate critical systems, minimizing the impact of potential injection attempts.
Real-World Examples: Packet Sniffing vs Injection
Packet sniffing involves capturing data packets in transit, as demonstrated by Wireshark's widespread use in network troubleshooting and intrusion detection. Packet injection manipulates or inserts packets into a network, with the Wi-Fi Pineapple device exemplifying this technique in penetration testing and network spoofing attacks. Both methods reveal critical vulnerabilities but serve distinct roles in cybersecurity, from passive monitoring to active exploitation.
Best Practices for Network Security Against Packet Manipulation
Implementing robust encryption protocols like TLS and IPsec prevents unauthorized packet sniffing by securing data in transit. Network segmentation and strict access controls minimize risks of packet injection by limiting attack surfaces and unauthorized device access. Continuous monitoring using intrusion detection systems (IDS) can quickly identify anomalies indicative of packet manipulation, enabling prompt response and mitigation.
Packet Sniffing vs Packet Injection Infographic
 techiny.com
techiny.com