Data masking and data anonymization both protect sensitive information but serve different purposes in cybersecurity. Data masking hides original data by replacing it with fictitious yet realistic values, maintaining data usability for testing or analysis without exposing actual data. Data anonymization irreversibly removes or alters Personally Identifiable Information (PII) to ensure privacy compliance and prevent re-identification in shared datasets.
Table of Comparison
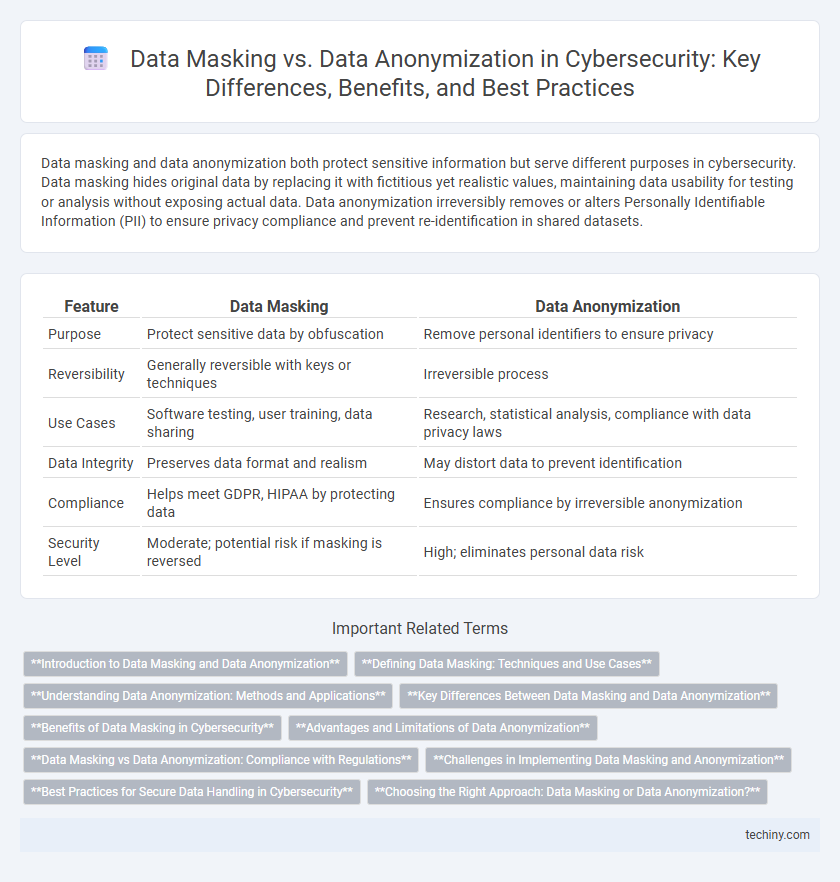
| Feature | Data Masking | Data Anonymization |
|---|---|---|
| Purpose | Protect sensitive data by obfuscation | Remove personal identifiers to ensure privacy |
| Reversibility | Generally reversible with keys or techniques | Irreversible process |
| Use Cases | Software testing, user training, data sharing | Research, statistical analysis, compliance with data privacy laws |
| Data Integrity | Preserves data format and realism | May distort data to prevent identification |
| Compliance | Helps meet GDPR, HIPAA by protecting data | Ensures compliance by irreversible anonymization |
| Security Level | Moderate; potential risk if masking is reversed | High; eliminates personal data risk |
Introduction to Data Masking and Data Anonymization
Data Masking and Data Anonymization are crucial techniques in cybersecurity for protecting sensitive information. Data Masking involves substituting original data with fictional yet realistic values to prevent unauthorized access while maintaining format integrity. Data Anonymization permanently removes or modifies personal identifiers, ensuring data cannot be traced back to an individual, which is essential for compliance with privacy regulations like GDPR and HIPAA.
Defining Data Masking: Techniques and Use Cases
Data masking involves replacing sensitive information with fictional but realistic data to protect confidentiality in non-production environments. Common techniques include static data masking, dynamic data masking, and tokenization, each ensuring that masked data maintains usability while preventing unauthorized access. Use cases span software testing, user training, and analytics, where operational efficiency requires working with data that cannot expose real personal or proprietary information.
Understanding Data Anonymization: Methods and Applications
Data anonymization involves transforming sensitive data into a format that prevents identification of individuals while preserving data utility for analysis and compliance purposes. Common methods include pseudonymization, data aggregation, and noise addition, which protect privacy in sectors like healthcare, finance, and marketing. Effective anonymization enables secure data sharing and regulatory adherence, minimizing the risk of data breaches.
Key Differences Between Data Masking and Data Anonymization
Data masking replaces sensitive data with fictional but realistic values to preserve data format while ensuring confidentiality, primarily used in non-production environments. Data anonymization irreversibly removes or modifies personal identifiers, making re-identification impossible and supporting compliance with privacy regulations like GDPR. Unlike masking, anonymization focuses on protecting user privacy in data sharing and analytics by preventing any link back to the original data subject.
Benefits of Data Masking in Cybersecurity
Data masking enhances cybersecurity by protecting sensitive information during testing and development, ensuring that real data is not exposed to unauthorized users. It reduces the risk of data breaches by providing realistic but obfuscated data, maintaining compliance with regulations such as GDPR and HIPAA. This technique also supports secure data sharing across departments without compromising privacy or confidentiality.
Advantages and Limitations of Data Anonymization
Data anonymization enhances privacy by irreversibly transforming sensitive data, reducing the risk of re-identification and ensuring compliance with regulations like GDPR. It allows secure data sharing and analysis without exposing personal information, supporting data-driven insights while protecting user confidentiality. However, anonymized data can lose analytical value due to distortion or loss of detail, and sophisticated attacks may sometimes re-identify anonymized records, highlighting limitations in absolute security.
Data Masking vs Data Anonymization: Compliance with Regulations
Data masking and data anonymization serve distinct roles in regulatory compliance, with data masking providing controlled data obfuscation to protect sensitive information while allowing usability in non-production environments. Data anonymization irreversibly removes personally identifiable information (PII), enabling organizations to meet stringent regulations such as GDPR and HIPAA by ensuring data cannot be traced back to individuals. Compliance frameworks prioritize anonymization for data sharing and masking for internal testing, balancing privacy requirements and operational needs.
Challenges in Implementing Data Masking and Anonymization
Implementing data masking and anonymization faces challenges such as maintaining data utility while ensuring privacy, as excessive masking can degrade analytical value. Technical complexities arise in selecting appropriate masking techniques that align with compliance requirements like GDPR and HIPAA. Additionally, ongoing management and monitoring are required to prevent re-identification risks and address evolving cyber threats effectively.
Best Practices for Secure Data Handling in Cybersecurity
Data masking and data anonymization are essential techniques for protecting sensitive information, with data masking altering data to prevent exposure while maintaining usability, and data anonymization irreversibly removing identifiable details. Best practices for secure data handling in cybersecurity include implementing role-based access controls, regularly auditing masked and anonymized datasets for compliance, and using encryption alongside these methods to strengthen data protection. Ensuring data is properly classified before masking or anonymization enhances overall security posture by minimizing the risk of data breaches.
Choosing the Right Approach: Data Masking or Data Anonymization?
Choosing between data masking and data anonymization depends on the intended use and level of data protection required. Data masking replaces sensitive information with fictional but realistic data, ideal for testing and development environments where usability must be retained without exposing real data. Data anonymization irreversibly removes identifying details, making it suitable for compliance with regulations like GDPR when using data for analytics or sharing with third parties.
Data Masking vs Data Anonymization Infographic
 techiny.com
techiny.com