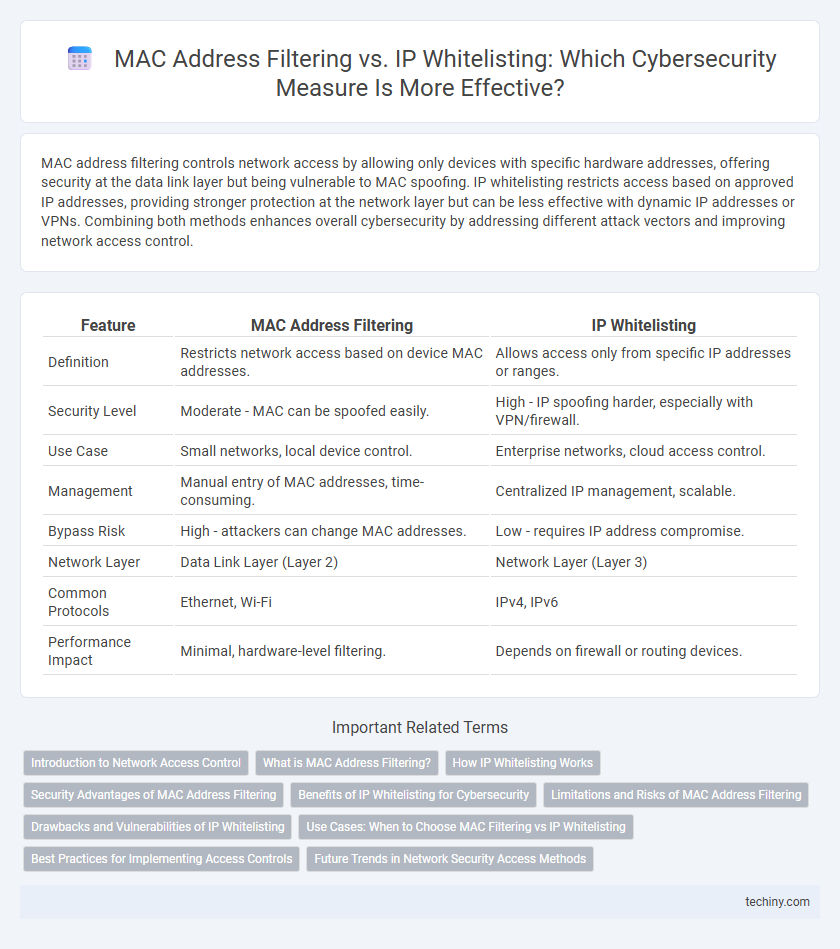
MAC address filtering controls network access by allowing only devices with specific hardware addresses, offering security at the data link layer but being vulnerable to MAC spoofing. IP whitelisting restricts access based on approved IP addresses, providing stronger protection at the network layer but can be less effective with dynamic IP addresses or VPNs. Combining both methods enhances overall cybersecurity by addressing different attack vectors and improving network access control.
Table of Comparison
| Feature | MAC Address Filtering | IP Whitelisting |
|---|---|---|
| Definition | Restricts network access based on device MAC addresses. | Allows access only from specific IP addresses or ranges. |
| Security Level | Moderate - MAC can be spoofed easily. | High - IP spoofing harder, especially with VPN/firewall. |
| Use Case | Small networks, local device control. | Enterprise networks, cloud access control. |
| Management | Manual entry of MAC addresses, time-consuming. | Centralized IP management, scalable. |
| Bypass Risk | High - attackers can change MAC addresses. | Low - requires IP address compromise. |
| Network Layer | Data Link Layer (Layer 2) | Network Layer (Layer 3) |
| Common Protocols | Ethernet, Wi-Fi | IPv4, IPv6 |
| Performance Impact | Minimal, hardware-level filtering. | Depends on firewall or routing devices. |
Introduction to Network Access Control
MAC Address Filtering restricts network access by allowing only devices with specific hardware identifiers, enhancing security at the data link layer. IP Whitelisting controls access by permitting only predefined IP addresses, providing protection at the network layer and enabling more dynamic and scalable management. Both methods are essential components of network access control strategies, balancing device authentication and flexible policy enforcement to safeguard organizational assets.
What is MAC Address Filtering?
MAC Address Filtering is a network security technique that controls device access based on the unique Media Access Control (MAC) address assigned to each network interface. This method restricts network entry to authorized devices by allowing only those with pre-approved MAC addresses to connect. Despite providing a layer of security, MAC Address Filtering can be bypassed through MAC address spoofing, making it less robust than IP whitelisting in dynamic or larger network environments.
How IP Whitelisting Works
IP whitelisting works by allowing only pre-approved IP addresses to access a network, thereby blocking any unauthorized or unknown IPs from gaining entry. This method enhances network security by restricting access based on the IP address, which is often more reliable than MAC address filtering due to the difficulty of spoofing IP addresses when combined with additional security measures. Many organizations implement IP whitelisting in firewalls and VPNs to create a trusted list of IP addresses that can access sensitive systems and data.
Security Advantages of MAC Address Filtering
MAC address filtering enhances network security by allowing only registered hardware devices to access the system, ensuring that unauthorized devices are blocked at the data link layer. This method reduces the risk of IP spoofing, as MAC addresses are unique to each network interface card, providing a more granular control over device access compared to IP whitelisting. By limiting access to known physical devices, MAC address filtering helps prevent unauthorized intrusion and mitigates the threat of network breaches originating from unknown hardware.
Benefits of IP Whitelisting for Cybersecurity
IP whitelisting enhances cybersecurity by allowing only pre-approved IP addresses to access sensitive networks, significantly reducing the attack surface from unknown or malicious sources. This method offers precise control over network access, preventing unauthorized entry even if credentials are compromised. Unlike MAC address filtering, IP whitelisting can be managed centrally and scaled efficiently across cloud environments and remote users.
Limitations and Risks of MAC Address Filtering
MAC address filtering presents significant limitations such as easy spoofing since attackers can mimic authorized MAC addresses, rendering the security ineffective. It also suffers from scalability issues in large networks due to the manual process of maintaining extensive MAC address lists. Unlike IP whitelisting, which controls access based on network-layer addresses, MAC filtering operates at the data link layer, providing less robust protection against sophisticated cyber threats and network infiltration.
Drawbacks and Vulnerabilities of IP Whitelisting
IP whitelisting can be bypassed through IP spoofing, allowing attackers to impersonate trusted addresses and gain unauthorized access. It also struggles with dynamic IP environments, causing legitimate users to be inadvertently blocked when their IP changes. Furthermore, maintaining accurate and up-to-date IP whitelists is resource-intensive and prone to human error, increasing the risk of security gaps.
Use Cases: When to Choose MAC Filtering vs IP Whitelisting
MAC address filtering is ideal for securing local networks by restricting device access based on hardware identifiers, making it effective for controlling physical device connections in environments like offices or home Wi-Fi. IP whitelisting is better suited for protecting applications and servers by allowing only specific IP addresses to communicate, which is essential for managing remote access and reducing exposure to unauthorized internet traffic. Choosing between MAC filtering and IP whitelisting depends on whether the security measure targets device-level control within a network or network-level access for external connections.
Best Practices for Implementing Access Controls
MAC Address Filtering enhances network security by restricting device access based on hardware identifiers, making it effective for small-scale networks with known devices. IP Whitelisting controls access by allowing only specified IP addresses, offering stronger security for remote access and broader network environments. Combining both methods with regular updates, strong authentication protocols, and monitoring ensures robust, layered access control defenses against unauthorized intrusions.
Future Trends in Network Security Access Methods
Emerging network security access methods emphasize enhanced identity verification through MAC Address Filtering and IP Whitelisting, integrating AI-driven analytics to detect and prevent unauthorized access in real time. The convergence of zero trust architecture with dynamic IP and MAC validation enables adaptive policy enforcement, reducing dependency on static lists vulnerable to spoofing or IP changes. Future trends highlight increased automation and machine learning applications to refine access control, ensuring robust protection against evolving cyber threats in complex network environments.
MAC Address Filtering vs IP Whitelisting Infographic
 techiny.com
techiny.com