A botnet is a network of compromised computers controlled by a central attacker to perform coordinated cyberattacks, such as DDoS or spam distribution. Each compromised device within the botnet is known as a zombie, which operates without the user's knowledge, executing commands remotely. Understanding the distinction between botnets and zombies is crucial for developing effective cybersecurity strategies to detect and dismantle these malicious networks.
Table of Comparison
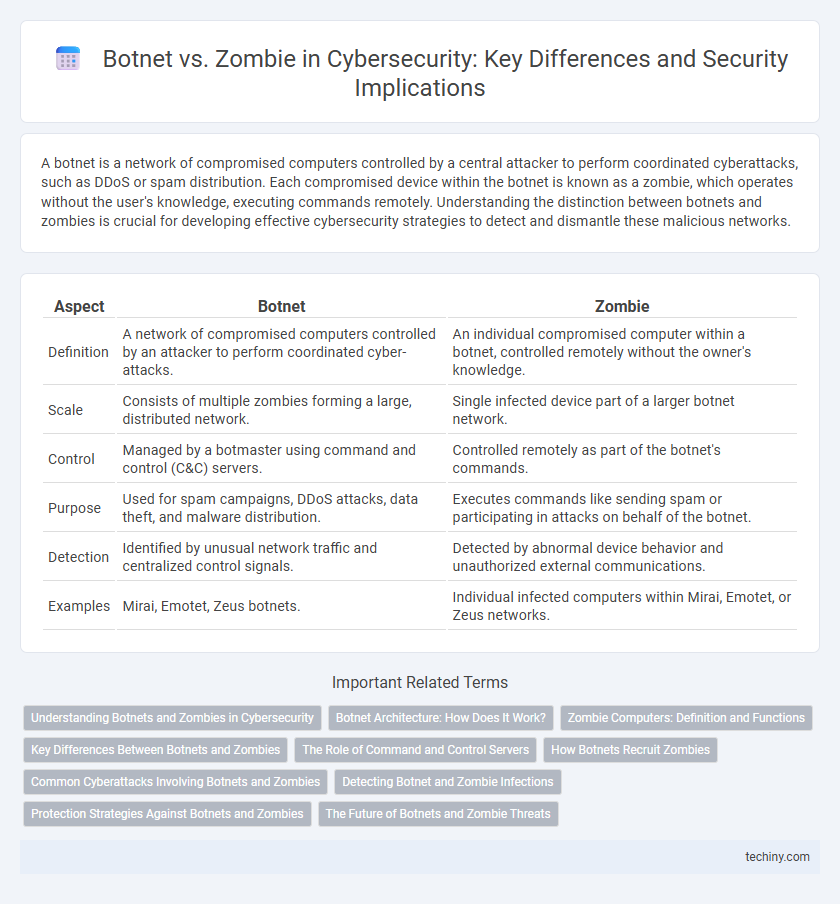
| Aspect | Botnet | Zombie |
|---|---|---|
| Definition | A network of compromised computers controlled by an attacker to perform coordinated cyber-attacks. | An individual compromised computer within a botnet, controlled remotely without the owner's knowledge. |
| Scale | Consists of multiple zombies forming a large, distributed network. | Single infected device part of a larger botnet network. |
| Control | Managed by a botmaster using command and control (C&C) servers. | Controlled remotely as part of the botnet's commands. |
| Purpose | Used for spam campaigns, DDoS attacks, data theft, and malware distribution. | Executes commands like sending spam or participating in attacks on behalf of the botnet. |
| Detection | Identified by unusual network traffic and centralized control signals. | Detected by abnormal device behavior and unauthorized external communications. |
| Examples | Mirai, Emotet, Zeus botnets. | Individual infected computers within Mirai, Emotet, or Zeus networks. |
Understanding Botnets and Zombies in Cybersecurity
Botnets are networks of compromised computers controlled by cybercriminals to execute large-scale attacks such as DDoS or spam campaigns, while zombies refer to the individual infected devices within this network. Understanding botnets involves analyzing how these zombie devices are infected via malware and exploited to perform malicious activities without user knowledge. Effective cybersecurity strategies target detecting, isolating, and dismantling these zombies to disrupt the command-and-control infrastructure of botnets.
Botnet Architecture: How Does It Work?
A botnet consists of a vast network of compromised devices, known as bots or zombies, controlled by a central command-and-control (C&C) server that issues instructions to execute coordinated cyberattacks such as Distributed Denial of Service (DDoS) or data theft. The architecture typically involves multiple layers, including the C&C server, intermediary bots acting as relay points, and the infected zombie machines that carry out the commands, allowing attackers to maintain control and evade detection through decentralized communication protocols like peer-to-peer (P2P). This layered design enhances resilience and scalability, making botnets powerful tools for malicious activities within cybersecurity threats.
Zombie Computers: Definition and Functions
Zombie computers are compromised devices infected by malware that allows attackers to control them remotely without the owner's knowledge. These machines form the backbone of botnets, executing malicious tasks such as distributed denial-of-service (DDoS) attacks, spamming, and data theft. By harnessing the collective power of numerous zombie computers, cybercriminals amplify their cyberattack capabilities and evade detection.
Key Differences Between Botnets and Zombies
Botnets consist of a network of compromised devices controlled by a single attacker to execute coordinated cyberattacks, while zombies are individual infected machines within a botnet that follow commands without user knowledge. Key differences include scale and control, where botnets orchestrate large-scale attacks leveraging numerous zombies, and zombies serve as the individual nodes executing these malicious tasks. Understanding these distinctions is crucial for identifying infection sources and mitigating distributed denial-of-service (DDoS) attacks effectively.
The Role of Command and Control Servers
Command and Control (C&C) servers act as the central hubs that issue commands to botnets, orchestrating coordinated cyberattacks, while zombie devices serve as compromised endpoints executing these instructions unbeknownst to their owners. In botnet architecture, C&C servers maintain control and communication with thousands to millions of infected zombies, facilitating activities such as distributed denial-of-service (DDoS) attacks and spam distribution. Advanced botnets employ decentralized or peer-to-peer C&C models to evade detection and disruption, enhancing their resilience against cybersecurity defenses.
How Botnets Recruit Zombies
Botnets recruit zombies by exploiting vulnerabilities in devices through malware distribution, phishing attacks, or software exploits to gain unauthorized control. Infected devices, known as zombies, are then coerced into executing automated tasks like sending spam or launching DDoS attacks without the user's knowledge. Command-and-control servers manage these zombies, coordinating their actions to maximize the botnet's impact on targeted networks.
Common Cyberattacks Involving Botnets and Zombies
Botnets and zombies are frequently exploited in distributed denial-of-service (DDoS) attacks, overwhelming targets with massive traffic to disrupt services. These networks of compromised devices also facilitate spam campaigns and credential stuffing attacks, leveraging infected machines to spread malware or automate login attempts. Cybercriminals use botnets and zombies to execute large-scale phishing schemes and data breaches, amplifying their reach and impact through coordinated infection.
Detecting Botnet and Zombie Infections
Detecting botnet and zombie infections involves monitoring unusual network traffic patterns, such as spikes in outbound connections or communications with known command-and-control servers. Analyzing system behavior for signs like frequent CPU spikes, unauthorized access attempts, and abnormal outbound messages aids in identifying compromised machines. Employing advanced intrusion detection systems (IDS) and endpoint security solutions enhances the ability to pinpoint and mitigate botnet-related threats effectively.
Protection Strategies Against Botnets and Zombies
Effective protection strategies against botnets and zombies include deploying advanced intrusion detection systems (IDS) and maintaining up-to-date antivirus software to identify and neutralize malicious traffic and infected devices. Network segmentation and rigorous firewall configurations limit the spread of botnet infections and isolate compromised machines to prevent further damage. Regular patch management and user education on phishing threats significantly reduce the attack surface exploited by botnet controllers to recruit zombie devices.
The Future of Botnets and Zombie Threats
Botnet architectures are evolving with AI-driven automation, enabling more sophisticated and adaptive attacks that complicate detection and mitigation efforts. The proliferation of IoT devices increases the attack surface, creating more vulnerable nodes for zombie computers to exploit and integrate into massive, decentralized botnets. Developing advanced anomaly detection systems and real-time threat intelligence sharing is crucial for combating the growing complexity and scale of future botnet and zombie-generated cyber threats.
Botnet vs Zombie Infographic
 techiny.com
techiny.com