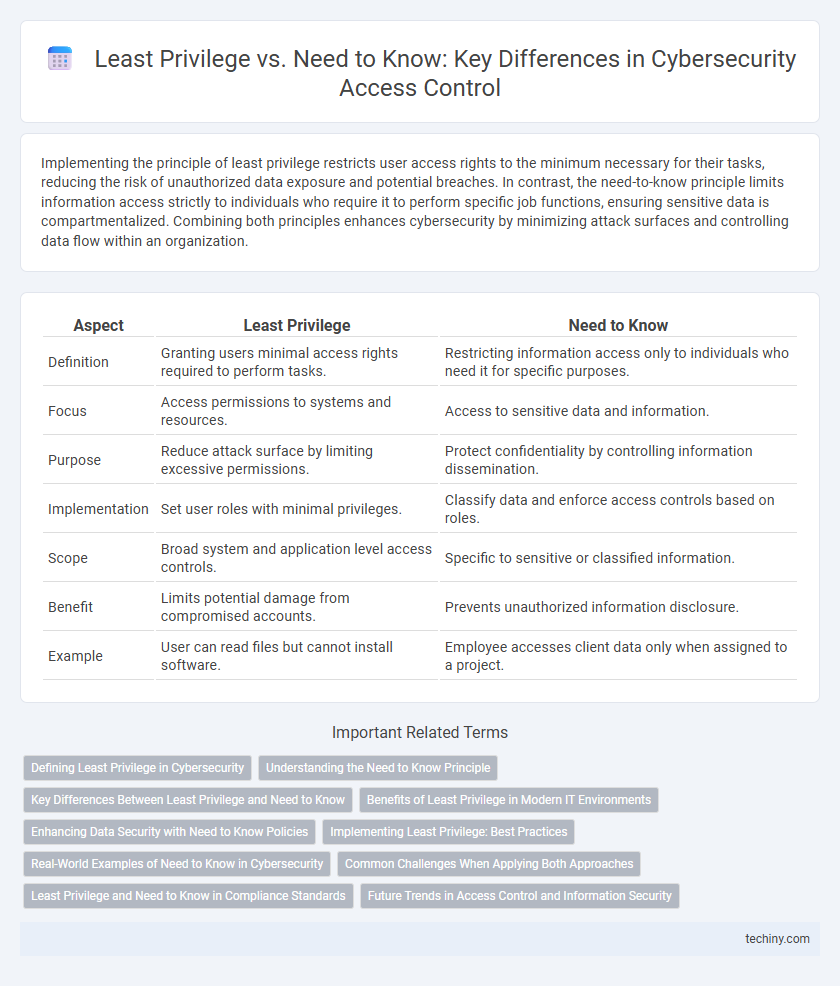
Implementing the principle of least privilege restricts user access rights to the minimum necessary for their tasks, reducing the risk of unauthorized data exposure and potential breaches. In contrast, the need-to-know principle limits information access strictly to individuals who require it to perform specific job functions, ensuring sensitive data is compartmentalized. Combining both principles enhances cybersecurity by minimizing attack surfaces and controlling data flow within an organization.
Table of Comparison
| Aspect | Least Privilege | Need to Know |
|---|---|---|
| Definition | Granting users minimal access rights required to perform tasks. | Restricting information access only to individuals who need it for specific purposes. |
| Focus | Access permissions to systems and resources. | Access to sensitive data and information. |
| Purpose | Reduce attack surface by limiting excessive permissions. | Protect confidentiality by controlling information dissemination. |
| Implementation | Set user roles with minimal privileges. | Classify data and enforce access controls based on roles. |
| Scope | Broad system and application level access controls. | Specific to sensitive or classified information. |
| Benefit | Limits potential damage from compromised accounts. | Prevents unauthorized information disclosure. |
| Example | User can read files but cannot install software. | Employee accesses client data only when assigned to a project. |
Defining Least Privilege in Cybersecurity
Least Privilege in cybersecurity restricts user access rights to the minimum necessary for performing job functions, significantly reducing the risk of unauthorized access or data breaches. By granting precise permissions, it limits exposure to critical systems and sensitive information, thereby enhancing overall network security. This principle enforces strict access controls, ensuring users cannot exceed their designated authority within the IT environment.
Understanding the Need to Know Principle
The Need to Know principle restricts access to sensitive information exclusively to individuals whose roles require it, minimizing data exposure and cyber risk. Unlike Least Privilege, which limits permissions system-wide, Need to Know focuses specifically on data access based on job necessity, enhancing confidentiality within organizations. Implementing Need to Know effectively reduces insider threats and supports compliance with data protection regulations such as GDPR and HIPAA.
Key Differences Between Least Privilege and Need to Know
Least Privilege restricts user access to only the minimal permissions required to perform their job functions, reducing the attack surface and limiting potential damage from insider threats. Need to Know, on the other hand, controls information access by granting users visibility strictly to data necessary for their specific tasks, thereby safeguarding sensitive information and maintaining confidentiality. The key difference lies in Least Privilege focusing on system permissions and operational capabilities, whereas Need to Know governs access to data based on confidentiality and information sensitivity.
Benefits of Least Privilege in Modern IT Environments
Implementing least privilege in modern IT environments significantly reduces the attack surface by limiting user access rights to only what is essential for their roles, thereby minimizing potential insider threats and lateral movement by attackers. This approach enhances compliance with regulations such as GDPR and HIPAA by enforcing strict access controls and detailed audit trails. Organizations benefit from improved system stability and reduced risk of accidental data breaches by preventing excessive permissions.
Enhancing Data Security with Need to Know Policies
Need to Know policies restrict access to sensitive data strictly to individuals who require it for their specific job functions, significantly reducing the risk of unauthorized data exposure. By enforcing Need to Know alongside Least Privilege principles, organizations limit access not only by permission levels but also by relevance to operational duties, strengthening overall data security. Implementing granular Need to Know controls within cybersecurity frameworks minimizes internal threats and supports compliance with data protection regulations such as GDPR and HIPAA.
Implementing Least Privilege: Best Practices
Implementing Least Privilege requires defining precise access controls that grant users only the permissions necessary for their roles, minimizing potential attack surfaces. Employ role-based access control (RBAC) and regularly audit permissions to ensure alignment with current job functions and prevent privilege creep. Employing automation tools for continuous monitoring and enforcing time-bound access further strengthens security posture by limiting exposure.
Real-World Examples of Need to Know in Cybersecurity
Need to Know principles in cybersecurity limit access to sensitive information strictly based on operational necessity, such as granting only network administrators access to firewall configurations to prevent unauthorized changes. In healthcare organizations, Need to Know restricts patient record access to doctors directly involved in treatment, minimizing data exposure risks. Financial institutions implement Need to Know by allowing only fraud investigators to view suspicious transaction data, enhancing security while maintaining compliance with data protection regulations.
Common Challenges When Applying Both Approaches
Implementing both Least Privilege and Need to Know principles often encounters challenges such as accurately identifying and classifying sensitive data and resources, which can lead to excessive restrictions or security gaps. Managing dynamic access needs requires constant monitoring and updating permissions to avoid workflow disruptions while maintaining security boundaries. Balancing usability and security demands clear policies, automated tools for access control, and continuous training to prevent privilege creep and unauthorized data exposure.
Least Privilege and Need to Know in Compliance Standards
Least Privilege and Need to Know are critical principles in cybersecurity compliance standards such as GDPR, HIPAA, and PCI-DSS. Least Privilege restricts user access rights to the minimum necessary for job functions, reducing the attack surface and mitigating insider threats. Need to Know complements this by ensuring sensitive data access is granted only when essential, enhancing data protection and aligning with regulatory requirements for privacy and information security.
Future Trends in Access Control and Information Security
Emerging trends in access control emphasize integrating least privilege and need-to-know principles through adaptive, AI-driven systems that dynamically adjust permissions based on user behavior and risk assessment. Zero Trust architectures are enhancing enforcement by continuously verifying user identities and contextual data to minimize unnecessary access. Future information security strategies focus on granular, real-time access management to reduce insider threats and improve compliance with evolving regulatory standards.
Least Privilege vs Need to Know Infographic
 techiny.com
techiny.com