Obfuscation disguises code to make it difficult for attackers to understand, while encryption transforms data into unreadable formats requiring a key for access. Encryption provides strong data protection by securely encoding information, whereas obfuscation primarily complicates reverse engineering efforts. Combining both techniques enhances overall cybersecurity by safeguarding sensitive data and hindering unauthorized code analysis.
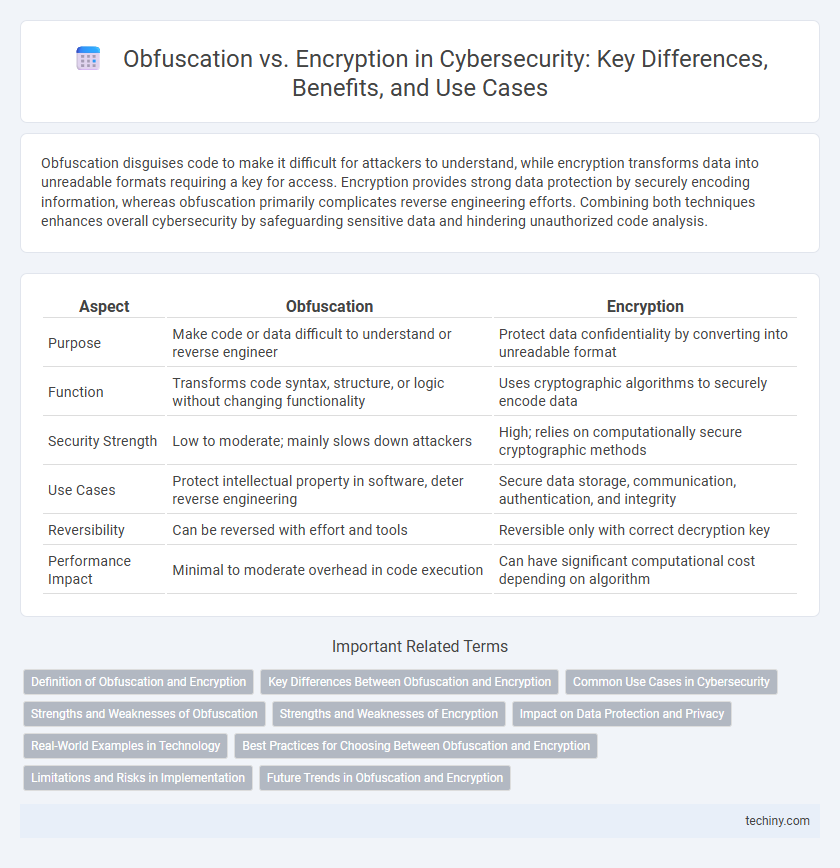
Table of Comparison
| Aspect | Obfuscation | Encryption |
|---|---|---|
| Purpose | Make code or data difficult to understand or reverse engineer | Protect data confidentiality by converting into unreadable format |
| Function | Transforms code syntax, structure, or logic without changing functionality | Uses cryptographic algorithms to securely encode data |
| Security Strength | Low to moderate; mainly slows down attackers | High; relies on computationally secure cryptographic methods |
| Use Cases | Protect intellectual property in software, deter reverse engineering | Secure data storage, communication, authentication, and integrity |
| Reversibility | Can be reversed with effort and tools | Reversible only with correct decryption key |
| Performance Impact | Minimal to moderate overhead in code execution | Can have significant computational cost depending on algorithm |
Definition of Obfuscation and Encryption
Obfuscation is a cybersecurity technique that deliberately disguises code or data to make it difficult for unauthorized users to understand or analyze. Encryption transforms data into an unreadable format using algorithms and keys, ensuring confidentiality and secure communication. Both methods protect sensitive information but differ in approach: obfuscation masks the inner workings, while encryption secures the data content.
Key Differences Between Obfuscation and Encryption
Obfuscation transforms code or data to make it difficult to understand while remaining functional, without necessarily using cryptographic keys. Encryption relies on mathematical algorithms and keys to convert plain text into unreadable ciphertext, ensuring confidentiality and enabling secure data transmission. Unlike encryption, obfuscation does not guarantee data confidentiality but is primarily used to hinder reverse engineering and protect intellectual property.
Common Use Cases in Cybersecurity
Obfuscation is commonly used in cybersecurity to protect source code from reverse engineering, making malware analysis and intellectual property theft more difficult. Encryption is widely employed to secure data in transit and at rest, ensuring confidentiality and preventing unauthorized access. While encryption safeguards data integrity and privacy, obfuscation primarily obscures code logic to hinder adversary understanding and tampering.
Strengths and Weaknesses of Obfuscation
Obfuscation enhances software security by making code difficult to understand or reverse-engineer, thereby protecting intellectual property and deterring casual attackers. However, it does not provide strong protection against determined adversaries since obfuscated code can eventually be decompiled or analyzed with advanced tools. Unlike encryption, obfuscation lacks formal cryptographic guarantees, making it a weaker defense mechanism that should be combined with other security measures for comprehensive protection.
Strengths and Weaknesses of Encryption
Encryption provides robust data protection by transforming information into unintelligible ciphertext, ensuring confidentiality and preventing unauthorized access. Its primary strength lies in strong cryptographic algorithms that resist brute-force attacks and maintain data integrity during transmission or storage. However, encryption requires secure key management, and improper handling of keys or weak algorithms can lead to vulnerabilities, potentially exposing sensitive information.
Impact on Data Protection and Privacy
Obfuscation disguises data by making it difficult to interpret without altering the actual data, providing a layer of security primarily against casual or automated attacks, but it does not prevent unauthorized access to the original content. Encryption transforms data into unreadable ciphertext, ensuring that only authorized parties with the correct decryption key can access the sensitive information, thereby offering robust protection for data confidentiality and privacy. While obfuscation can complement encryption by adding complexity, encryption remains the fundamental technique for safeguarding data integrity and privacy in cybersecurity.
Real-World Examples in Technology
Obfuscation techniques are widely used in software development to protect intellectual property by making code difficult to understand, as seen in mobile apps where JavaScript obfuscators prevent reverse engineering. Encryption, on the other hand, secures data through algorithms like AES and RSA, exemplified by HTTPS protocols encrypting web communication to safeguard user information. Real-world applications reveal obfuscation's role in protecting executable files and encryption's critical function in securing sensitive data transmissions across networks.
Best Practices for Choosing Between Obfuscation and Encryption
Choosing between obfuscation and encryption depends on the desired balance of security and performance; encryption provides strong data protection through complex algorithms, while obfuscation makes code or data difficult to interpret without altering its function. Best practices recommend using encryption for sensitive data confidentiality and obfuscation for protecting intellectual property or deterring reverse engineering in software. Combining both methods can enhance security by encrypting critical data and obfuscating the supporting code to prevent unauthorized access and tampering.
Limitations and Risks in Implementation
Obfuscation obscures code or data to hinder understanding but does not provide true confidentiality, making it vulnerable to reverse engineering and tampering. Encryption offers strong data protection using cryptographic algorithms but requires proper key management and can introduce performance overhead. Both methods face implementation risks such as misuse, insufficient complexity, and potential backdoors, necessitating combined strategies for robust cybersecurity.
Future Trends in Obfuscation and Encryption
Emerging trends in cybersecurity emphasize advancements in obfuscation techniques such as polymorphic and metamorphic code to enhance software protection against reverse engineering. Quantum-resistant encryption algorithms are gaining traction to secure data against future quantum computing threats, while homomorphic encryption enables computation on encrypted data without decryption. Integrating AI-driven adaptive obfuscation with next-generation encryption methods promises robust defense mechanisms against evolving cyber threats.
Obfuscation vs Encryption Infographic
 techiny.com
techiny.com