UEBA (User and Entity Behavior Analytics) enhances cybersecurity by analyzing patterns of user behavior to detect insider threats and anomalous activities that traditional SIEM (Security Information and Event Management) systems might miss. SIEM aggregates and correlates log data from various sources for real-time threat detection and compliance reporting, but it often generates high volumes of alerts requiring manual analysis. Integrating UEBA with SIEM creates a more comprehensive security posture by combining event data with advanced behavioral insights for accurate and proactive threat identification.
Table of Comparison
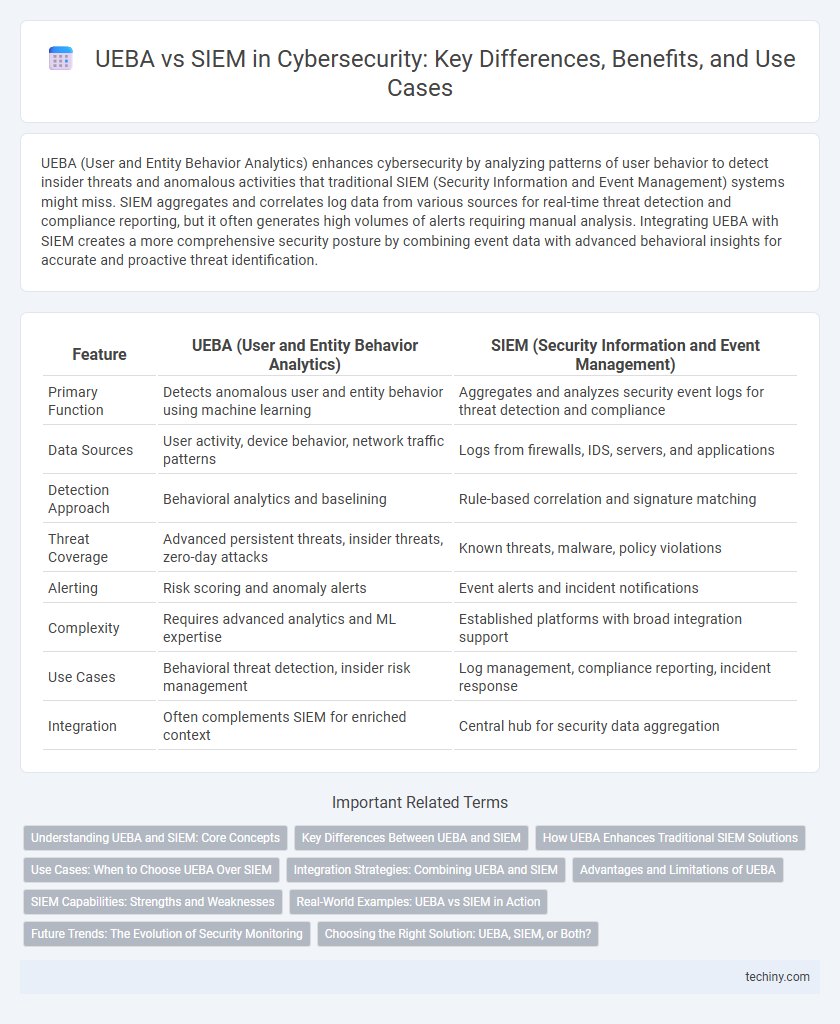
| Feature | UEBA (User and Entity Behavior Analytics) | SIEM (Security Information and Event Management) |
|---|---|---|
| Primary Function | Detects anomalous user and entity behavior using machine learning | Aggregates and analyzes security event logs for threat detection and compliance |
| Data Sources | User activity, device behavior, network traffic patterns | Logs from firewalls, IDS, servers, and applications |
| Detection Approach | Behavioral analytics and baselining | Rule-based correlation and signature matching |
| Threat Coverage | Advanced persistent threats, insider threats, zero-day attacks | Known threats, malware, policy violations |
| Alerting | Risk scoring and anomaly alerts | Event alerts and incident notifications |
| Complexity | Requires advanced analytics and ML expertise | Established platforms with broad integration support |
| Use Cases | Behavioral threat detection, insider risk management | Log management, compliance reporting, incident response |
| Integration | Often complements SIEM for enriched context | Central hub for security data aggregation |
Understanding UEBA and SIEM: Core Concepts
User and Entity Behavior Analytics (UEBA) leverages machine learning to identify anomalous patterns in user activities, enhancing threat detection beyond traditional signature-based methods. Security Information and Event Management (SIEM) aggregates and analyzes log data from multiple sources to provide real-time event correlation and incident response capabilities. Combining UEBA with SIEM creates a comprehensive security approach by merging behavioral analysis with centralized log management and alerting.
Key Differences Between UEBA and SIEM
User and Entity Behavior Analytics (UEBA) leverages machine learning to identify anomalous activities by analyzing behavioral patterns of users and entities, while Security Information and Event Management (SIEM) primarily aggregates and correlates logs and events for real-time threat detection and compliance reporting. UEBA excels in detecting insider threats and sophisticated attacks by focusing on deviations from normal behavior, whereas SIEM provides comprehensive visibility through log management and rule-based alerting. Integration of UEBA with SIEM enhances threat detection accuracy by combining behavioral insights with event correlation.
How UEBA Enhances Traditional SIEM Solutions
User and Entity Behavior Analytics (UEBA) enhances traditional Security Information and Event Management (SIEM) solutions by providing advanced behavioral analysis to detect insider threats, compromised accounts, and sophisticated cyberattacks that signature-based SIEM tools might miss. UEBA utilizes machine learning algorithms and anomaly detection to analyze user activities, generating more accurate alerts with lower false positives. Integrating UEBA with SIEM improves incident response times and strengthens overall threat detection capabilities by correlating behavioral data with log events.
Use Cases: When to Choose UEBA Over SIEM
UEBA excels in detecting insider threats, compromised accounts, and subtle anomalous behaviors by analyzing user and entity patterns over time, which traditional SIEM systems may overlook due to their rule-based approach. SIEM is more effective for log management, compliance reporting, and alerting based on predefined correlation rules, making UEBA the preferred choice when advanced behavioral analytics and risk scoring are critical. Organizations aiming to enhance threat detection through machine learning-driven insights and reduce false positives should prioritize UEBA over SIEM.
Integration Strategies: Combining UEBA and SIEM
Integrating UEBA (User and Entity Behavior Analytics) with SIEM (Security Information and Event Management) enhances threat detection by combining behavioral analysis with real-time event correlation. Effective integration strategies involve leveraging UEBA's machine learning models to enrich the contextual data SIEM collects, enabling more accurate anomaly detection and reducing false positives. Centralized dashboards and automated workflows streamline incident response, ensuring cohesive security operations that maximize the strengths of both technologies.
Advantages and Limitations of UEBA
User and Entity Behavior Analytics (UEBA) excels in detecting insider threats, zero-day attacks, and advanced persistent threats by analyzing normal behavior patterns and identifying anomalies that traditional Security Information and Event Management (SIEM) systems may miss. UEBA leverages machine learning and advanced analytics to provide contextual insights, reducing false positives and improving threat detection accuracy. However, UEBA requires large volumes of quality data and can be resource-intensive to implement, often necessitating expertise in tuning models and interpreting results to avoid alert fatigue.
SIEM Capabilities: Strengths and Weaknesses
Security Information and Event Management (SIEM) systems excel in aggregating and correlating large volumes of log data from diverse sources, enabling real-time threat detection and compliance reporting. Their strength lies in centralized visibility, rule-based alerts, and detailed forensic analysis, but they often struggle with false positives and require significant tuning and expert management. SIEM's reliance on predefined signatures limits detection of novel threats, highlighting the need for complementary tools like UEBA for behavioral anomaly detection.
Real-World Examples: UEBA vs SIEM in Action
UEBA (User and Entity Behavior Analytics) enhances traditional SIEM (Security Information and Event Management) systems by detecting insider threats and advanced persistent threats through behavior-based anomaly detection. For instance, UEBA identified a compromised employee account in a financial institution by flagging unusual access patterns, which SIEM alone missed due to its rule-based approach. In another example, SIEM efficiently aggregated and correlated log data across a healthcare network, enabling rapid incident response, while UEBA provided deeper insights by highlighting deviations from normal user behavior.
Future Trends: The Evolution of Security Monitoring
UEBA (User and Entity Behavior Analytics) leverages advanced machine learning algorithms to detect anomalies in user behavior, offering deeper insights compared to traditional SIEM (Security Information and Event Management) systems that primarily focus on log aggregation and correlation. Future security monitoring trends indicate an integrated approach combining UEBA's behavioral analytics with SIEM's real-time event management to enhance threat detection accuracy and reduce false positives. The evolution emphasizes automation, AI-driven predictive analytics, and contextual awareness to proactively identify sophisticated cyber threats in dynamic and complex environments.
Choosing the Right Solution: UEBA, SIEM, or Both?
Choosing between UEBA (User and Entity Behavior Analytics) and SIEM (Security Information and Event Management) depends on your organization's threat detection needs and resource availability. UEBA excels at identifying anomalous behavior by analyzing patterns and user activities, making it ideal for insider threat detection and advanced attacks. SIEM integrates and correlates log data from multiple sources, providing real-time monitoring and compliance management; combining both solutions can maximize security effectiveness by leveraging behavioral analytics alongside comprehensive event logging.
UEBA vs SIEM Infographic
 techiny.com
techiny.com