Symmetric encryption uses a single key for both encryption and decryption, offering faster processing suitable for large data volumes but requiring secure key distribution. Asymmetric encryption involves a pair of keys--public and private--enabling secure communication without key sharing but with higher computational overhead. Combining both methods enhances overall cybersecurity by balancing speed and security through hybrid encryption systems.
Table of Comparison
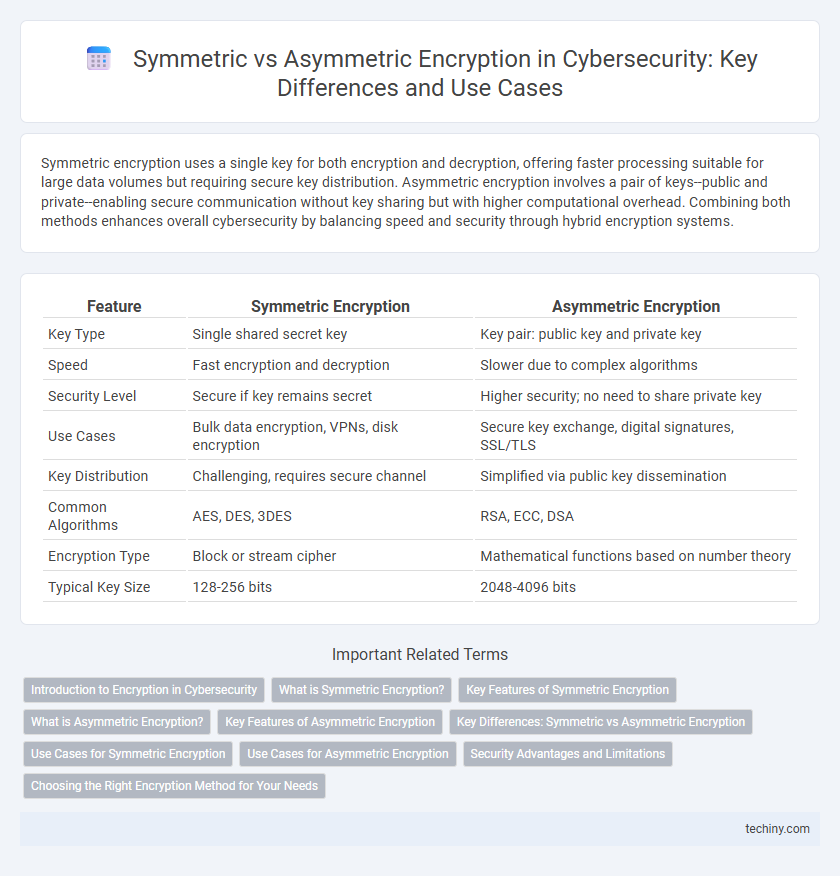
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Type | Single shared secret key | Key pair: public key and private key |
| Speed | Fast encryption and decryption | Slower due to complex algorithms |
| Security Level | Secure if key remains secret | Higher security; no need to share private key |
| Use Cases | Bulk data encryption, VPNs, disk encryption | Secure key exchange, digital signatures, SSL/TLS |
| Key Distribution | Challenging, requires secure channel | Simplified via public key dissemination |
| Common Algorithms | AES, DES, 3DES | RSA, ECC, DSA |
| Encryption Type | Block or stream cipher | Mathematical functions based on number theory |
| Typical Key Size | 128-256 bits | 2048-4096 bits |
Introduction to Encryption in Cybersecurity
Encryption in cybersecurity protects data by converting it into unreadable formats using algorithms and keys. Symmetric encryption employs a single shared key for both encryption and decryption, offering faster processing but requiring secure key distribution. Asymmetric encryption uses a pair of keys--public and private--enabling secure communication without sharing private keys, though it generally demands more computational resources.
What is Symmetric Encryption?
Symmetric encryption is a cryptographic method where the same secret key is used for both encrypting and decrypting data, enabling fast and efficient processing ideal for large volumes of information. This technique relies on key confidentiality, as the security of the data depends entirely on keeping the shared key secret between communicating parties. Common symmetric encryption algorithms include AES (Advanced Encryption Standard), DES (Data Encryption Standard), and ChaCha20, widely used for securing data at rest and in transit.
Key Features of Symmetric Encryption
Symmetric encryption uses a single secret key for both encryption and decryption, enabling faster processing and lower computational overhead compared to asymmetric encryption. Its key features include simplicity in implementation, efficient handling of large data volumes, and strong protection when keys are securely managed. However, secure key distribution remains a critical challenge, as both sender and receiver must share and protect the same secret key.
What is Asymmetric Encryption?
Asymmetric encryption uses a pair of keys--a public key for encryption and a private key for decryption--enabling secure communication without sharing secret keys beforehand. It is fundamental to technologies like SSL/TLS for secure internet connections, digital signatures, and key exchange protocols. Unlike symmetric encryption, asymmetric methods provide enhanced security by eliminating the need to transmit private keys, reducing risk of interception.
Key Features of Asymmetric Encryption
Asymmetric encryption employs a pair of mathematically linked keys: a public key for encryption and a private key for decryption, enhancing security by eliminating the need to share secret keys. Its key features include enabling secure communication over open channels, facilitating digital signatures for authentication and non-repudiation, and supporting key exchange protocols that underpin SSL/TLS and other encryption standards. Unlike symmetric encryption, asymmetric methods are computationally intensive but provide scalable solutions for key management in distributed environments.
Key Differences: Symmetric vs Asymmetric Encryption
Symmetric encryption uses a single shared key for both encryption and decryption, offering faster processing speeds suitable for large data volumes but requiring secure key distribution. Asymmetric encryption relies on a pair of keys--a public key for encryption and a private key for decryption--enabling secure communication without sharing secret keys, albeit with slower performance. Key differences center on speed, key management, and security model, where symmetric methods excel in efficiency and asymmetric in secure key exchange.
Use Cases for Symmetric Encryption
Symmetric encryption is ideal for securing large volumes of data due to its fast processing speed and lower computational overhead compared to asymmetric encryption. Common use cases include encrypting data at rest in databases and filesystems, securing communication channels in virtual private networks (VPNs), and protecting sensitive information in real-time applications like video streaming and instant messaging. Its efficiency makes it the preferred choice for bulk data encryption where key distribution is managed securely.
Use Cases for Asymmetric Encryption
Asymmetric encryption is essential for secure communications, enabling encrypted email, digital signatures, and SSL/TLS protocols that safeguard web browsing and data transfers. This encryption method supports public key infrastructure (PKI) used in VPNs and secure file sharing, providing authentication and confidentiality. Its key distribution advantage makes it ideal for scenarios where secure key exchange is critical.
Security Advantages and Limitations
Symmetric encryption offers faster data processing and efficiency for securing large volumes of information but requires secure key distribution, which poses a vulnerability risk. Asymmetric encryption enhances security through the use of distinct public and private keys, enabling secure key exchange and digital signatures, yet it is computationally intensive and slower. Both methods are complementary, with symmetric encryption often securing data transmission while asymmetric encryption manages secure key exchanges and authentication.
Choosing the Right Encryption Method for Your Needs
Symmetric encryption uses a single key for both encryption and decryption, making it faster and ideal for encrypting large amounts of data within secure environments. Asymmetric encryption employs a pair of keys--public and private--which enhances security through secure key exchange but typically involves slower processing speeds. Selecting the right encryption method depends on factors like data sensitivity, system performance requirements, and the necessity for secure key distribution in your cybersecurity strategy.
Symmetric vs Asymmetric (Encryption) Infographic
 techiny.com
techiny.com