Least Privilege limits user access strictly to the resources necessary for their role, minimizing potential attack surfaces and reducing insider threat risks. Zero Trust continuously verifies every access request, assuming no implicit trust based on network location or user credentials, which strengthens protection against sophisticated cyber threats. Combining Least Privilege with Zero Trust principles creates a robust security framework that enforces strict access controls and continuous monitoring to safeguard sensitive data and systems.
Table of Comparison
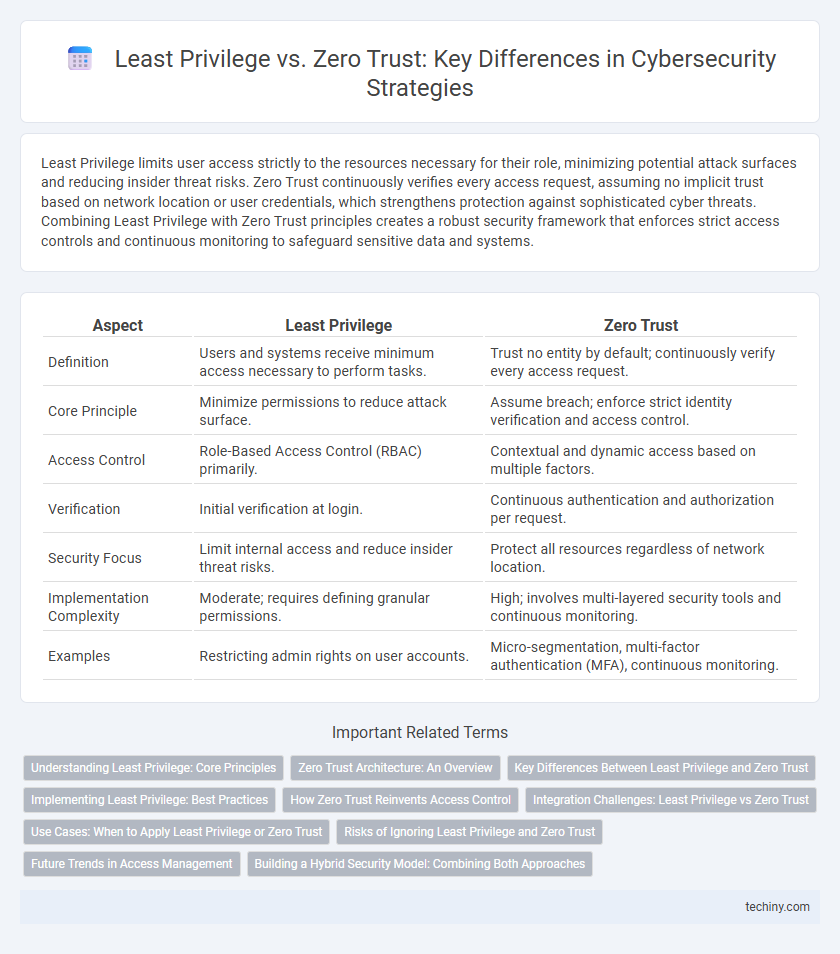
| Aspect | Least Privilege | Zero Trust |
|---|---|---|
| Definition | Users and systems receive minimum access necessary to perform tasks. | Trust no entity by default; continuously verify every access request. |
| Core Principle | Minimize permissions to reduce attack surface. | Assume breach; enforce strict identity verification and access control. |
| Access Control | Role-Based Access Control (RBAC) primarily. | Contextual and dynamic access based on multiple factors. |
| Verification | Initial verification at login. | Continuous authentication and authorization per request. |
| Security Focus | Limit internal access and reduce insider threat risks. | Protect all resources regardless of network location. |
| Implementation Complexity | Moderate; requires defining granular permissions. | High; involves multi-layered security tools and continuous monitoring. |
| Examples | Restricting admin rights on user accounts. | Micro-segmentation, multi-factor authentication (MFA), continuous monitoring. |
Understanding Least Privilege: Core Principles
Least Privilege is a fundamental cybersecurity principle that restricts users' access rights to the minimum necessary for their job functions, limiting potential damage from insider threats or compromised accounts. It enforces strict access control by granting permissions only based on role requirements, reducing attack surfaces and enhancing security posture. Implementing Least Privilege ensures continuous evaluation and adjustment of access rights, supporting strong identity governance and minimizing privilege escalation risks.
Zero Trust Architecture: An Overview
Zero Trust Architecture (ZTA) enforces strict identity verification for every user and device attempting to access resources, regardless of their location within or outside the network perimeter. Unlike traditional Least Privilege models that limit access based on predefined roles, ZTA continuously assesses trust using real-time context, anomaly detection, and behavioral analytics. This approach reduces the attack surface by ensuring that no entity is inherently trusted, minimizing lateral movement and insider threats in complex cybersecurity environments.
Key Differences Between Least Privilege and Zero Trust
Least Privilege enforces minimal user permissions necessary for specific tasks, reducing attack surfaces by limiting access rights. Zero Trust adopts a broader security model requiring continuous verification of all users and devices, regardless of their location within or outside the network perimeter. The key difference lies in Least Privilege's focus on permission minimization versus Zero Trust's emphasis on never trusting any entity by default and validating every access attempt.
Implementing Least Privilege: Best Practices
Implementing Least Privilege involves granting users and systems the minimum access necessary to perform their tasks, significantly reducing attack surfaces and insider threat risks. Best practices include regularly reviewing and updating access controls, enforcing role-based access control (RBAC), and utilizing automated tools to detect privilege creep and anomalies. Continuous monitoring combined with strict authentication mechanisms ensures that least privilege policies adapt dynamically to evolving cybersecurity threats.
How Zero Trust Reinvents Access Control
Zero Trust revolutionizes access control by verifying every user and device regardless of their location, eliminating implicit trust within the network perimeter. Unlike Least Privilege, which restricts access based on predefined roles, Zero Trust employs continuous authentication, real-time risk assessment, and micro-segmentation to minimize attack surfaces. This dynamic approach ensures that access permissions adapt instantly to context, significantly enhancing protection against advanced cyber threats.
Integration Challenges: Least Privilege vs Zero Trust
Integrating Least Privilege principles with Zero Trust architectures often encounters challenges due to differing scopes and implementation complexities; Least Privilege focuses on restricting user access rights to minimum necessary levels, while Zero Trust requires continuous verification of every access attempt regardless of location. Aligning these models necessitates advanced identity and access management (IAM) solutions capable of granular policy enforcement and real-time threat detection. Organizations must overcome potential conflicts in policy definition and scalability while ensuring seamless interoperability between access controls and network segmentation protocols.
Use Cases: When to Apply Least Privilege or Zero Trust
Least Privilege is essential in environments where users require minimal access to perform specific tasks, such as managing sensitive databases or configuring system settings, reducing insider threats and accidental damage. Zero Trust is better suited for dynamic, cloud-based, or hybrid infrastructures demanding continuous verification of user identities and device integrity, especially in remote work scenarios or when dealing with third-party vendors. Applying Least Privilege strengthens internal controls, while Zero Trust offers comprehensive protection against external and lateral threats by validating every access request.
Risks of Ignoring Least Privilege and Zero Trust
Ignoring Least Privilege and Zero Trust principles significantly elevates the risk of unauthorized access, data breaches, and lateral movement within networks. Excessive user permissions provide cyber attackers with multiple opportunities to exploit vulnerabilities, leading to compromised sensitive information and disrupted operations. Implementing these frameworks mitigates potential attack surfaces, fortifies access controls, and enhances overall cybersecurity resilience.
Future Trends in Access Management
Future trends in access management emphasize the convergence of least privilege and zero trust models, leveraging AI-driven continuous authentication and behavior analytics to minimize insider threats. Adaptive access controls will dynamically adjust permissions based on contextual risk factors such as device health, location, and user behavior patterns. Cloud-native security frameworks and decentralized identity technologies are set to enhance granular access enforcement, ensuring resilient protection against evolving cyber threats.
Building a Hybrid Security Model: Combining Both Approaches
Implementing a hybrid security model that integrates Least Privilege and Zero Trust principles enhances protection by minimizing access rights while continuously verifying user identities and device health. This combined approach reduces attack surfaces by enforcing strict access controls and dynamic authentication, adapting to evolving threats in real-time. Organizations adopting this strategy benefit from improved compliance, reduced insider risks, and stronger defenses against lateral movement within networks.
Least Privilege vs Zero Trust Infographic
 techiny.com
techiny.com