Keyloggers capture and record every keystroke made on a device, allowing attackers to steal sensitive information such as passwords and credit card numbers. Rootkits, on the other hand, provide attackers with persistent, stealthy control over a system by hiding their presence and enabling unauthorized access at the deepest level. While keyloggers primarily focus on data theft through monitoring inputs, rootkits manipulate the operating system to maintain long-term covert access and evade detection by security software.
Table of Comparison
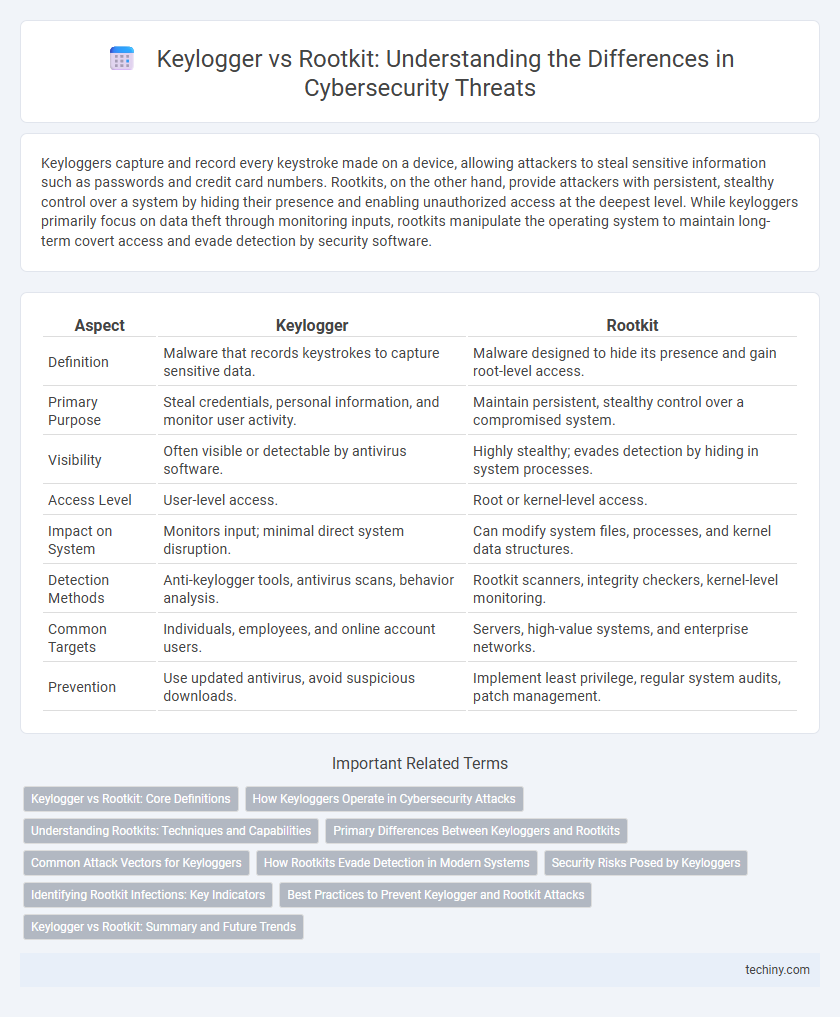
| Aspect | Keylogger | Rootkit |
|---|---|---|
| Definition | Malware that records keystrokes to capture sensitive data. | Malware designed to hide its presence and gain root-level access. |
| Primary Purpose | Steal credentials, personal information, and monitor user activity. | Maintain persistent, stealthy control over a compromised system. |
| Visibility | Often visible or detectable by antivirus software. | Highly stealthy; evades detection by hiding in system processes. |
| Access Level | User-level access. | Root or kernel-level access. |
| Impact on System | Monitors input; minimal direct system disruption. | Can modify system files, processes, and kernel data structures. |
| Detection Methods | Anti-keylogger tools, antivirus scans, behavior analysis. | Rootkit scanners, integrity checkers, kernel-level monitoring. |
| Common Targets | Individuals, employees, and online account users. | Servers, high-value systems, and enterprise networks. |
| Prevention | Use updated antivirus, avoid suspicious downloads. | Implement least privilege, regular system audits, patch management. |
Keylogger vs Rootkit: Core Definitions
Keyloggers are malicious software designed to record every keystroke made by a user, capturing sensitive information such as passwords and credit card numbers. Rootkits operate at a deeper level by gaining unauthorized root or administrative access to a computer system, allowing attackers to hide their presence and control the system covertly. While keyloggers focus on data capture, rootkits emphasize stealth and persistent access to compromised systems.
How Keyloggers Operate in Cybersecurity Attacks
Keyloggers operate by secretly recording keystrokes made by a user, capturing sensitive information such as passwords, credit card numbers, and personal messages, which are then transmitted to cybercriminals. These malicious programs often install themselves through phishing emails, infected software downloads, or exploiting system vulnerabilities, remaining undetected while monitoring user inputs. Unlike rootkits that conceal system processes or files to maintain control, keyloggers focus specifically on intercepting and logging input data to facilitate identity theft and unauthorized access.
Understanding Rootkits: Techniques and Capabilities
Rootkits employ advanced stealth techniques to gain persistent, unauthorized access to a system by hiding their presence from traditional security tools. They manipulate low-level system functions, including kernel modules and system libraries, to conceal malicious activity and maintain control over compromised devices. Unlike keyloggers that solely capture keystrokes, rootkits possess broader capabilities such as enabling remote control, data exfiltration, and evading detection by masking malware components.
Primary Differences Between Keyloggers and Rootkits
Keyloggers primarily focus on capturing and recording keystrokes to steal sensitive information such as passwords and credit card numbers, while rootkits operate at a deeper system level to hide malicious activities and maintain persistent access to compromised devices. Unlike keyloggers, rootkits manipulate the operating system kernel or firmware to remain undetected by traditional security measures. Both pose severe cybersecurity threats, but their mechanisms and targets differ significantly, with keyloggers targeting user input and rootkits targeting system integrity.
Common Attack Vectors for Keyloggers
Keyloggers commonly infiltrate systems through phishing emails, malicious downloads, and compromised software installations, capturing keystrokes to steal sensitive information like passwords and credit card numbers. Unlike rootkits, which primarily aim to hide malicious activities and maintain persistent control over a system, keyloggers focus on discreetly recording user input data. Effective cybersecurity measures include regularly updating software, employing robust antivirus programs, and educating users about recognizing suspicious links and attachments.
How Rootkits Evade Detection in Modern Systems
Rootkits evade detection in modern systems by integrating deeply into the operating system kernel, enabling them to manipulate system processes and hide their presence from traditional security tools. They use techniques such as hooking system calls and modifying kernel data structures to intercept and alter system behaviors, making their activities invisible to antivirus and monitoring software. This stealth approach contrasts with keyloggers, which primarily capture keystrokes but are easier to detect due to less sophisticated concealment strategies.
Security Risks Posed by Keyloggers
Keyloggers pose significant security risks by covertly capturing sensitive information such as passwords, credit card details, and personal communications, often without the user's knowledge. Unlike rootkits, which primarily focus on maintaining privileged access and hiding malicious activity, keyloggers directly compromise privacy by logging every keystroke and transmitting the data to attackers. This enables identity theft, financial fraud, and unauthorized access to critical systems, making keyloggers a severe threat in cybersecurity defense.
Identifying Rootkit Infections: Key Indicators
Rootkit infections often manifest through unusual system behavior such as hidden files, unexplained CPU usage spikes, and compromised security settings that are difficult to alter or detect. Unlike keyloggers that primarily capture keystrokes, rootkits embed deeply into the operating system, enabling attackers to maintain persistent control while evading traditional antivirus detection. Monitoring system integrity with specialized rootkit detectors and analyzing abnormal network activity are critical strategies for identifying these stealthy threats.
Best Practices to Prevent Keylogger and Rootkit Attacks
Implementing multi-layered security measures such as regular software updates, robust antivirus programs, and advanced malware detection tools effectively prevents keylogger and rootkit infections. Employing user education on phishing attacks, avoiding suspicious downloads, and enabling two-factor authentication reduces the risk of unauthorized access. Network segmentation and continuous monitoring of system behavior enhance early detection and mitigation of stealthy rootkit activities.
Keylogger vs Rootkit: Summary and Future Trends
Keylogger vs Rootkit comparison reveals distinct cybersecurity threats: keyloggers covertly capture keystrokes to steal sensitive information, while rootkits enable attackers to maintain persistent, stealthy access to compromised systems. Future trends emphasize advanced detection techniques leveraging AI and machine learning to identify behavioral anomalies caused by these malware types. Enhanced endpoint security and real-time monitoring are critical to mitigating evolving keylogger and rootkit threats.
Keylogger vs Rootkit Infographic
 techiny.com
techiny.com