Threat refers to any potential danger that can exploit a vulnerability to cause harm to a system or network, while risk represents the likelihood and impact of that threat materializing. Understanding the distinction between threat and risk is essential for developing effective cybersecurity strategies and prioritizing resources. Accurately assessing risk involves analyzing both the probability of a threat and the potential damage it could inflict on digital assets.
Table of Comparison
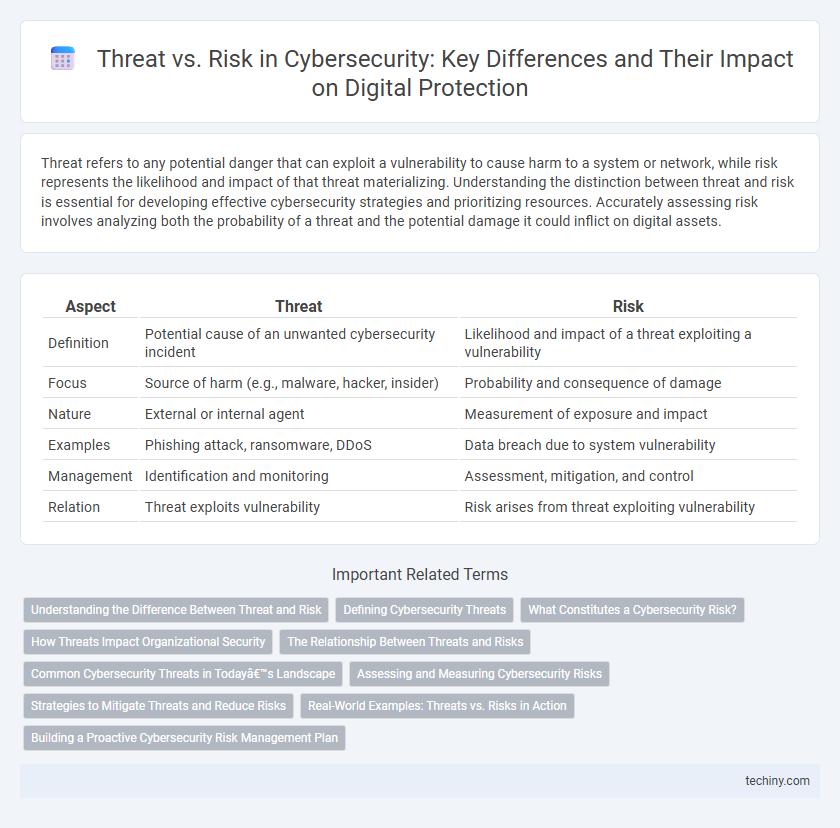
| Aspect | Threat | Risk |
|---|---|---|
| Definition | Potential cause of an unwanted cybersecurity incident | Likelihood and impact of a threat exploiting a vulnerability |
| Focus | Source of harm (e.g., malware, hacker, insider) | Probability and consequence of damage |
| Nature | External or internal agent | Measurement of exposure and impact |
| Examples | Phishing attack, ransomware, DDoS | Data breach due to system vulnerability |
| Management | Identification and monitoring | Assessment, mitigation, and control |
| Relation | Threat exploits vulnerability | Risk arises from threat exploiting vulnerability |
Understanding the Difference Between Threat and Risk
Threat refers to any potential cause of an unwanted impact on a system or organization, such as malware, hackers, or natural disasters. Risk represents the likelihood and potential severity of a threat exploiting vulnerabilities, resulting in harm to assets or operations. Understanding the difference between threat and risk enables cybersecurity professionals to prioritize resources effectively by assessing both the existence of threats and the probability of their impact.
Defining Cybersecurity Threats
Cybersecurity threats refer to potential malicious actions or events targeting digital systems, networks, or data with the intent to cause harm, unauthorized access, or disruption. These threats include malware, phishing attacks, ransomware, insider threats, and advanced persistent threats (APTs), each exploiting specific vulnerabilities within an organization's security infrastructure. Understanding the nature and methods of cybersecurity threats is crucial for implementing effective defense measures and minimizing exposure to cyber risks.
What Constitutes a Cybersecurity Risk?
A cybersecurity risk constitutes the potential for loss or damage when a threat exploits a vulnerability within an information system or network. It encompasses the likelihood of a cyber threat materializing and the impact it could have on critical digital assets, including data breaches, system downtime, or financial loss. Effective risk management requires identifying vulnerabilities, assessing threat capabilities, and evaluating potential consequences to prioritize mitigation strategies.
How Threats Impact Organizational Security
Threats directly compromise organizational security by exploiting vulnerabilities in systems, leading to data breaches, financial losses, and reputational damage. The presence of advanced persistent threats (APTs) and ransomware attacks increases the likelihood of operational disruption and unauthorized access to sensitive information. Understanding the nature and evolution of cyber threats enables organizations to implement proactive defense mechanisms and minimize potential impacts on security infrastructure.
The Relationship Between Threats and Risks
Threats represent potential sources of harm to digital assets, such as malware, phishing attacks, or insider breaches, while risks quantify the likelihood and impact of these threats exploiting vulnerabilities. The relationship between threats and risks is dynamic; effective risk management requires continuously identifying evolving threats and assessing their probability and consequences on an organization's security posture. Understanding this interplay enables cybersecurity professionals to prioritize resources, implement targeted controls, and mitigate potential damages effectively.
Common Cybersecurity Threats in Today’s Landscape
Common cybersecurity threats in today's landscape include ransomware, phishing attacks, and advanced persistent threats (APTs), all of which exploit vulnerabilities to compromise sensitive data and disrupt operations. Threats represent potential dangers from malicious actors, whereas risk quantifies the likelihood and impact of these threats exploiting specific vulnerabilities. Effective cybersecurity strategies prioritize identifying and mitigating these threats to minimize organizational risk and safeguard digital assets.
Assessing and Measuring Cybersecurity Risks
Assessing cybersecurity risks involves identifying potential threats, evaluating vulnerabilities, and estimating the potential impact on organizational assets. Unlike threats, which represent possible sources of harm such as malware or phishing attacks, risks quantify the likelihood and consequences of these threats exploiting vulnerabilities. Effective risk measurement uses frameworks like NIST SP 800-30 or ISO 27005 to prioritize security controls based on risk scores derived from asset value, threat probability, and exploitability.
Strategies to Mitigate Threats and Reduce Risks
Effective cybersecurity strategies prioritize identifying potential threats such as malware, phishing, and insider attacks while assessing associated risks like data breaches and financial loss. Implementing multi-layered defenses including firewalls, intrusion detection systems, regular patch management, and employee training significantly reduces vulnerabilities. Continuous risk assessment combined with proactive threat intelligence enables organizations to adapt and strengthen security postures against evolving cyber threats.
Real-World Examples: Threats vs. Risks in Action
A ransomware attack exemplifies a cyber threat targeting an organization's critical data, while the risk involves the potential financial loss and reputational damage if defenses fail. In 2017, the WannaCry malware exploited vulnerabilities in outdated Windows systems, demonstrating a real-world threat leading to widespread operational disruption and payment demands. Effective risk management includes patching systems promptly and implementing robust backup strategies to mitigate the impact of such threats.
Building a Proactive Cybersecurity Risk Management Plan
Understanding the distinction between threat and risk is crucial for building a proactive cybersecurity risk management plan. Threats represent potential sources of harm such as malware, phishing attacks, or insider threats, while risks assess the likelihood and impact of these threats exploiting vulnerabilities in an organization. Implementing continuous threat intelligence, real-time monitoring, and rigorous vulnerability assessments enables organizations to anticipate and mitigate cybersecurity risks effectively before incidents occur.
Threat vs Risk Infographic
 techiny.com
techiny.com